- Engineering Mathematics
- Discrete Mathematics
- Operating System
- Computer Networks
- Digital Logic and Design
- C Programming
- Data Structures
- Theory of Computation
- Compiler Design
- Computer Org and Architecture

What is VPN and How It Works?
VPN is a mechanism of employing encryption, authentication, and integrity protection so that we can use a public network as if it is a private network. It offers a high amount of security and allows users to remotely access private networks. In this article, we will cover every point about virtual private networks.
What is a VPN?
A virtual private network (VPN) is a technology that creates a safe and encrypted connection over a less secure network, such as the Internet. A Virtual Private Network is a way to extend a private network using a public network such as the Internet. The name only suggests that it is a “Virtual Private Network”, i.e. user can be part of a local network sitting at a remote location. It makes use of tuneling protocols to establish a secure connection.
History of VPNs
ARPANET introduced the idea of connecting distant computers in the 1960s. The foundation for current internet connectivity was established by ensuring the development of protocols like TCP/IP in the 1980s. Particular VPN technologies first appeared in the 1990s in response to the growing concerns about online privacy and security.
Need for VPN
It could easily be said that VPNs are a necessity since privacy, security, and free internet access should be everybody’s right. First, they establish secure access to the corporate networks for remote users; then, they secure the data during the transmission and, finally, they help users to avoid geo-blocking and censorship. VPNs are highly useful for protecting data on open Wi-Fi, for privacy, and preventing one’s ISP from throttling one’s internet connection.
How Does a VPN Work?
Let us understand VPN with an example think of a situation where the corporate office of a bank is situated in Washington, USA. This office has a local network consisting of say 100 computers. Suppose other branches of the bank are in Mumbai, India, and Tokyo, Japan. The traditional method of establishing a secure connection between the head office and the branch was to have a leased line between the branches and head office which was a very costly as well as troublesome job. VPN lets us effectively overcome this issue.
The situation is described below
- All 100 hundred computers of the corporate office in Washington are connected to the VPN server(which is a well-configured server containing a public IP address and a switch to connect all computers present in the local network i.e. in the US head office).
- The person sitting in the Mumbai office connects to The VPN server using a dial-up window and the VPN server returns an IP address that belongs to the series of IP addresses belonging to a local network of the corporate office.
- Thus person from the Mumbai branch becomes local to the head office and information can be shared securely over the public internet.
- So this is the intuitive way of extending the local network even across the geographical borders of the country.
VPN is well Exploited all Across the Globe
We will explain to you with an example. Suppose we are using smartphones regularly. Spotify Swedish music app that is not active in India But we are making full use of it sitting in India. So how ?? VPN can be used to camouflage our geolocation.
- Suppose the IP address is 101.22.23.3 which belongs to India. That’s why our device is not able to access the Spotify music app.
- But the magic began when we used the Psiphon app which is an Android app used to change the device IP address to the IP address of the location we want(say US where Spotify works seamlessly).
- The IP address is changed using VPN technology. Basically what happens is that your device will connect to a VPN server of the respective country that you have entered in your location textbox of the Psiphon app and now you will inherit a new IP from this server.
Now we typed “What is my IP address”? Amazingly the IP address changed to 45.79.66.125 which belongs to the USA And since Spotify works well in the US, we can use it now being in India (virtually in the USA). Is not that good? obviously, it is very useful.

- VPN also ensures security by providing an encrypted tunnel between the client and the VPN server.
- VPN is used to bypass many blocked sites.
- VPN facilitates Anonymous browsing by hiding your IP address.
- Also, the most appropriate Search engine optimization (SEO) is done by analyzing the data from VPN providers which provide country-wise statics of browsing a particular product.
- VPNs encrypt your internet traffic, safeguarding your online activities from potential eavesdropping and cyber threats, thereby enhancing your privacy and data protection.
Characteristics of VPN
- Encryption: VPNs employ several encryption standards to maintain the confidentiality of the transmitted data and, even if intercepted, can’t be understood.
- Anonymity: Thus, VPN effectively hides the users IP address, thus offering anonymity and making tracking by websites or other third parties impossible.
- Remote Access: VPNs provide the means for secure remote connection to business’ networks thus fostering employee productivity through remote working.
- Geo-Spoofing: The user can also change the IP address to another country using the VPN hence breaking the regional restrictions of some sites.
- Data Integrity: VPNs make sure that the data communicated in the network in the exact form and not manipulated in any way.
Types of VPN
There are several types of VPN and these are vary from specific requirement in computer network. Some of the VPN are as follows:
- Remote Access VPN
- Site to Site VPN
For more details you can refer Types of VPN published article.
VPN Protocols
- OpenVPN: A cryptographic protocol that prioritises security is called OpenVPN. OpenVPN is compatible protocol that provides a variety of setup choices.
- Point-To-Point Tunneling Protocol(PPTP): PPTP is not utilized because there are many other secure choices with higher and more advanced encryption that protect data.
- WireGuard: Wireguard is a good choice that indicates capability in terms of performance.
- Secure Socket Tunneling Protocol(SSTP): SSTP is developed for Windows users by Microsoft. It is not widely used due to the lack of connectivity.
- Layer 2 Tunneling Protocol(L2TP) It connects a user to the VPN server but lacks encryption hence it is frequently used with IPSec to offer connection, encryption, and security simultaneously.
Why Should Use VPN?
- For Unlimited Streaming: Love streaming your favourite shows and sports games? A VPN is your ultimate companion for unlocking streaming services.
- For elevating your Gaming Experience: Unleash your gaming potential with the added layer of security and convenience provided by a VPN. Defend yourself against vengeful competitors aiming to disrupt your gameplay while improving your ping for smoother, lag-free sessions. Additionally, gain access to exclusive games that may be restricted in your region, opening up a world of endless gaming possibilities.
- For Anonymous Torrenting : When it comes to downloading copyrighted content through torrenting, it’s essential to keep your IP address hidden. A VPN can mask your identity and avoid potential exposure, ensuring a safe and private torrenting experience.
- For supercharging your Internet Speed: Are you tired of your Internet speed slowing down when downloading large files? Your Internet Service Provider (ISP) might be intentionally throttling your bandwidth. Thankfully, a VPN can rescue you by keeping your online activities anonymous, effectively preventing ISP throttling. Say goodbye to sluggish connections and embrace blazing-fast speeds.
- Securing Public Wi-Fi: VPNs are essential for maintaining security when using public Wi-Fi networks, such as those in coffee shops, airports, or hotels. These networks are often vulnerable to cyberattacks, and using a VPN encrypts your internet connection, protecting your data from potential hackers and eavesdroppers when you connect to untrusted Wi-Fi hotspots.
Tunnelling Protocols for VPN
- OpenVPN: An open source protocol with very good security and the ability to set up the functionality to use. Secure Sockets Layer / Transport Layer Security is for the key exchange; it can go through firewalls and network address translators (NATs).
- Point-To-Point Tunneling Protocol (PPTP) : Another outdated VPN protocol is PPTP as it is one of the oldest VPN protocols that are quite easy to configure but provides the weaker security than most contemporary VPN protocols.
- WireGuard: A relatively new protocol that has been widely recommended because of its relative ease of use and high performance. It incorporates modern techniques of encryption and it is perhaps easier to implement and to audit.
- Secure Socket Tunnelling Protocol (SSTP): SSTP is a Microsoft developed protocol; it is compatible with the Windows operating systems and uses SSL/TLS for encryption which is rather secure.
- Layer 2 Tunnelling Protocol (L2TP): L2TP is frequently combined with IPsec for encryption; however, L2TP does not have encryption integrated into it but does build a secure tunnel for data.
Authentication Mechanisms in VPN
- Pre-Shared Key (PSK): Is a secret key that is used for authenticating the two parties, that is, the client and the VPN server. It is easy to integrate but is also considered insecure when not administered properly.
- Digital Certificates: Based on certificates given by a reliable certificate authority, it is effective in identifying the identity of users and devices with a sense of security.
- Username and Password: Usually known in user authentication in which users submit their credentials for them to access the VPNs. This method is sometimes supported by other security measures such as MFA (multi-factor authentication).
- Two-Factor Authentication (2FA): Provides another level of protection by including a second factor of identification in the manner of a number received via one’s cellular telephone along with a user identification and password.
Security Concerns in VPN
- Data Leakage: VPNs also can some time not hide IP address and thus cause leakages of data collected. This can happen via DNS leaks or when the VPN connection is severed prematurely or when switches between servers.
- Weak Encryption: Even the security of a VPN can be affected by weak encryption standards as well as outdated encryption algorithms. In this case, it is essential to implement sound encryption/decryption methods.
- Trust in VPN Providers: VPN provider can only guarantee that they will secure the user’s data and refrain from abusing it if the user themselves trusts their service provider. Some providers may keep records of the use of the resource by a user and this can infringe on the privacy of a consumer.
- Man-in-the-Middle Attacks (MitM): If VPN setting is not safe, the attacker gets the chance to intervene and modify information exchanged between client and server.
- Performance Trade-offs: VPN security often affects internet connection since the encryption and routing through VPN servers cause slower connection. For security and performance are always equally important for the choice of the measures.
Are VPNs legal or illegal?
Using a VPN is legal in most countries, The legality of using a VPN service depends on the country and its geopolitical relations with another country as well. A reliable and secure VPN is always legal if you do not intend to use it for any illegal activities like committing fraud online, cyber theft, or in some countries downloading copyrighted content. China has decided to block all VPNs (Virtual private network) by next year, as per the report of Bloomberg. Many Chinese Internet users use VPNs to privately access websites that are blocked under China’s so-called “great firewall”. This is done to avoid any information leakage to rival countries and to tighten the information security.
What to Look for When Choosing a VPN?
- Be sure the VPN has appropriate speed, a lot of providers have trouble keeping up with Netflix viewing or downloading.
- Read both user and expert evaluations to gain a good idea of how well the VPN operates.
- Select a VPN provider that provides shared IP addresses .
- More servers translate into faster browsing because there will be less traffic on each one.
Benefits of VPN
- When you use VPN it is possible to switch IP.
- The internet connection is safe and encrypted with VPN
- Sharing files is confidential and secure.
- Your privacy is protected when using the internet.
- There is no longer a bandwidth restriction.
- It facilitates cost savings for internet shopping.
Limitations of VPN
- VPN may decrease your internet speed.
- Premium VPNs are not cheap.
- VPN usage may be banned in some nations.]
In conclusion, a VPN (Virtual Private Network) is a powerful tool that enhances your online privacy and security by encrypting your internet connection and masking your IP address. Whether you’re accessing public Wi-Fi, wanting to browse the web more securely, or bypassing geographical restrictions, a VPN offers a layer of protection that keeps your data safe. As the digital landscape continues to evolve, understanding and using a VPN can be an essential step in safeguarding your online presence.
Frequently Asked Question on VPN – FAQs
Can a vpn be traced.
While VPNs enhance privacy, it’s not entirely foolproof. In some cases, determined adversaries, such as government agencies, may employ advanced techniques to trace VPN usage. However, for typical online privacy needs, a VPN provides a high level of protection.
Do VPNs Slow Down Internet Speed?
VPNs can introduce some degree of latency due to the encryption and routing processes. The extent of the speed reduction depends on various factors, including the VPN provider’s infrastructure, server location, and your internet connection. In many cases, the impact on speed is minimal, and modern VPN services strive to provide fast connections.
Are There Free VPNs?
Yes, there are free VPN services available. However, they often come with limitations such as data caps, slower speeds, and less robust security features. Paid VPN services generally offer more reliable performance and better security.
Where are VPNs illegal?
Despite being heavily used in major parts of the worlds, VPNs are strictly prohibited in few countries that includes: Russia China Belarus North Korea Iraq, etc.
Please Login to comment...
Similar reads.
- 105 Funny Things to Do to Make Someone Laugh
- Best PS5 SSDs in 2024: Top Picks for Expanding Your Storage
- Best Nintendo Switch Controllers in 2024
- Xbox Game Pass Ultimate: Features, Benefits, and Pricing in 2024
- #geekstreak2024 – 21 Days POTD Challenge Powered By Deutsche Bank
Improve your Coding Skills with Practice
What kind of Experience do you want to share?

Virtual Private Networks (VPN’s)
Apr 07, 2019
3.76k likes | 8.85k Views
Virtual Private Networks (VPN’s). By: Agasi Aslanyan Joel Almasol Joe Nghe Michael Wong CIS 484 May 20, 2004. Table Of Contents. VPN Introduction – What is VPN and who uses it? 3 Types of VPN’s VPN Protocols VPN Tunneling VPN Packet Transmission VPN Security: Firewalls VPN Devices
Share Presentation
- different protocols
- company branches
- vpn advantages disadvantages
- internet protocol security protocol
- outside company headquarters

Presentation Transcript
Virtual Private Networks(VPN’s) By: Agasi Aslanyan Joel Almasol Joe Nghe Michael Wong CIS 484 May 20, 2004
Table Of Contents • VPN Introduction – What is VPN and who uses it? • 3 Types of VPN’s • VPN Protocols • VPN Tunneling • VPN Packet Transmission • VPN Security: Firewalls • VPN Devices • VPN Advantages/Disadvantages • VPN Connections in Windows XP • Summary/Conclusion
What is a VPN? • A virtual private network (VPN) is a network that uses public means of transmission (Internet) as its WAN link
What is a VPN? (Cont.) A VPN can be created by connecting offices and single users (including mobile users) to the nearest service providers POP (Point of Presence) and using that service provider’s backbone network, or even the Internet, as the tunnel between offices Traffic that flows through the backbone is encrypted to prevent intruders from spying or intercepting the data
What is a VPN? (Cont.)
Who uses VPN’s? • VPN’s can be found in homes, workplaces, or anywhere else as long as an ISP (Internet Service Provider) is available. • VPN’s allow company employees who travel often or who are outside their company headquarters to safely and securely connect to their company’s Intranet
3 Types of VPN • Remote-Access VPN • Site-to-Site VPN (Intranet-based) • Site-to-Site VPN (Extranet-based)
Remote-Access VPN • Remote-access, also called a virtual private dial-up network (VPDN), is a user-to-LAN connection used by a company that has employees who need to connect to the private network from various remote locations. • A good example of a company that needs a remote-access VPN would be a large firm with hundreds of sales people in the field. • Remote-access VPNs permit secure, encrypted connections between a company's private network and remote users through a third-party service provider.
Site-to-Site VPN • Intranet-based - If a company has one or more remote locations that they wish to join in a single private network, they can create an intranet VPN to connect LAN to LAN. • Extranet-based - When a company has a close relationship with another company (for example, a partner, supplier or customer), they can build an extranet VPN that connects LAN to LAN, and that allows all of the various companies to work in a shared environment.
All 3 types of VPN
VPN Protocols • There are three main protocols that power the vast majority of VPN’s: • PPTP • L2TP • IPsec • All three protocols emphasize encryption and authentication; preserving data integrity that may be sensitive and allowing clients/servers to establish an identity on the network
VPN Protocols (In depth) • Point-to-point tunneling protocol (PPTP) • PPTP is widely supported by Microsoft as it is built into the various flavors of the Windows OS • PPTP initially had weak security features, however, Microsoft continues to improve its support • Layer Two tunneling protocol (L2TP) • L2TP was the original competitor to PPTP and was implemented primarily in Cisco products • L2TP is a combination of the best features of an older protocol L2F and PPTP • L2TP exists at the datalink layer (Layer 2) of the OSI model
VPN Protocols (continued) • Internet Protocol Security Protocol (IPSec) provides enhanced security features such as better encryption algorithms and more comprehensive authentication. • IPSec has two encryption modes: tunnel and transport. Tunnel encrypts the header and the payload of each packet while transport only encrypts the payload. Only systems that are IPSec compliant can take advantage of this protocol. • IPSec can encrypt data between various devices, such as: • Router to router • Firewall to router • PC to router • PC to server
VPN Tunneling • VPN Tunneling supports two types: voluntary tunneling and compulsory tunneling • Voluntary tunneling is where the VPN client manages the connection setup. • Compulsory tunneling is where the carrier network provider manages the VPN connection setup.
Tunneling • Most VPNs rely on tunneling to create a private network that reaches across the Internet. Essentially, tunneling is the process of placing an entire packet within another packet and sending it over a network. Tunneling requires three different protocols: • Passenger protocol - The original data (IPX, IP) being carried • Encapsulating protocol - The protocol (GRE, IPSec, L2F, PPTP, L2TP) that is wrapped around the original data • Carrier protocol - The protocol used by the network that the information is traveling over
VPN Packet Transmission • Packets are first encrypted before sent out for transmission over the Internet. The encrypted packet is placed inside an unencrypted packet. The unencrypted outer packet is read by the routing equipment so that it may be properly routed to its destination • Once the packet reaches its destination, the outer packet is stripped off and the inner packet is decrypted
VPN Security: Firewalls A well-designed VPN uses several methods for keeping your connection and data secure: • Firewalls • Encryption • IPSec • AAA Server • You can set firewalls to restrict the number of open ports, what type of packets are passed through and which protocols are allowed through.
Cisco 1700 Series Routers Some VPN products, such as Cisco 1700 routers, can be upgraded to include firewall capabilities by running the appropriate Cisco IOS on them.
VPN Concentrator • Incorporating the most advanced encryption and authentication techniques available, Cisco VPN concentrators are built specifically for creating a remote-access VPN. • The concentrators are offered in models suitable for everything from small businesses with up to 100 remote-access users to large organizations with up to 10,000 simultaneous remote users.
Advantages of VPN’s • There are two main advantages of VPN’s, namely cost savings and scalability • VPN’s lower costs by eliminating the need for expensive long-distance leased lines. A local leased line or even a broadband connection is all that’s needed to connect to the Internet and utilize the public network to securely tunnel a private connection
Advantages of VPN’s (continued) • As the number of company branches grows, purchasing additional leased-lines increases cost exponentially, which is why VPN’s offer even greater cost savings when scalability is an issue • VPN’s may also be used to span globally, which lowers cost even more when compared to traditional leased lines
Disadvantages of VPN’s • Because the connection travels over public lines, a strong understanding of network security issues and proper precautions before VPN deployment are necessary • VPN connection stability is mainly in control of the Internet stability, factors outside an organizations control • Differing VPN technologies may not work together due to immature standards
VPN Connection in XP
Summary • A virtual private network (VPN) is a network that uses public means of transmission (Internet) as its WAN link, connecting clients who are geographically separated through secure tunneling methods • Main VPN protocols include PPTP, L2TP, and IPsec • VPN Tunneling supports two types: voluntary tunneling and compulsory tunneling • Cost and Scalability are the main advantages of a VPN • Network security and Internet stability are the main concerns for VPN’s
Resources Used • http://vpn.shmoo.com/ • http://www.uwsp.edu/it/vpn/ • http://info.lib.uh.edu/services/vpn.html • http://www.cites.uiuc.edu/vpn/ • http://www.positivenetworks.net/images/client-uploads/jumppage2.htm
The End Thank you all for your time. We hope you found this presentation informative.
- More by User

Information Security Internet, Intranet, Extranet
Information Security Internet, Intranet, Extranet Prof. dr. P.M.E. De Bra Department of Computing Science Eindhoven University of Technology Parts / Topics / Issues Basics of Internet technology / Organization Principles of Firewalls / Virtual Private Networks.
1.37k views • 73 slides

Private Pilot
Private Pilot. Private Pilot. The Process: Medical Exam Written FAA Aeronautical Knowledge Exam. 13 areas of knowledge required by 61.105 of the Federal Aviation Regulations. Practical Exam. Private Pilot. FAR’s NTSB AIM Charts Radio Procedures Weather Flight Safety. Private Pilot.
1.51k views • 41 slides

Hydro Networks in GIS
Hydro Networks in GIS. Network model Flow on Networks Hydrologic networks Linear referencing on networks. Some slides in this presentation were prepared by Dr Francisco Olivera. Raster to Vector Transition.
1.09k views • 69 slides

Querying Sensor Networks
Querying Sensor Networks. Sam Madden UC Berkeley November 18 th , 2002 @ Madison. Introduction. What are sensor networks? Programming Sensor Networks Is Hard Especially if you want to build a “real” application
1.09k views • 85 slides

Chapter VIII Virtual Memory
Chapter VIII Virtual Memory. Jehan-François Pâris [email protected]. Chapter overview. Virtual Memory Address translation On-demand fetch Page table organization Page replacement policies Performance issues. Basics. Virtual memory. Combines two big ideas
1.06k views • 87 slides

Vehicular Ad hoc Networks (VANET)
Vehicular Ad hoc Networks (VANET). Wireless Networks. 2008/10/1. A taxonomy of wireless networks. 4. 2008/10/1. Examples. Ad Hoc Networks. Non-infrastructure Fixed and Mobile Nodes Special Classes of Ad Hoc Networks Vehicular Ad Hoc Networks Wireless Mesh Networks
3.33k views • 78 slides
NETWORK MODELS
NETWORK MODELS. Networks. Physical Networks Road Networks Railway Networks Airline traffic Networks Electrical networks, e.g., the power grid Abstract networks organizational charts precedence relationships in projects Others?. Network Overview.
1.22k views • 86 slides

Tips for Locating Information on Private and Local Companies
Tips for Locating Information on Private and Local Companies. Presented by: Ed Hahn – Weber State University Britt Fagerheim – Utah State University. Private Companies. What is a Private Company? Private companies are owned by: Individuals Family Group of shareholders. Private Companies.
942 views • 72 slides
Chapter 7 Packet-Switching Networks
Chapter 7 Packet-Switching Networks. Chapter 7 Packet-Switching Networks. Network Services and Internal Network Operation Packet Network Topology Datagrams and Virtual Circuits Routing in Packet Networks Shortest Path Routing ATM Networks Traffic Management.
1.8k views • 151 slides

Missouri-NEA social media workshop
Missouri-NEA social media workshop. Don Blake, NEA MWRO. Agenda. Attitudes about social networking: what you said and are we in alignment with how our members say they use social media? Social Networks and Content Sharing tools: Are you familiar with them? A Primer … Private Social Networks
1.22k views • 92 slides

Interconnection Networks
Interconnection Networks. Interconnection Networks. Bus-oriented Ring Crossbar Two and Three dimensional mesh Multi-level switched Hypercube. General Issues. n − to − n networks connect PE ’ s directly n − by − n PE ’ s are interconnected through a network of switches.
2.71k views • 96 slides

Unit 4 The Virtual World
Unit 4 The Virtual World. Text A A Virtual Life. Before-Reading. 1. While-Reading. 2. After-Reading. 3. Before-Reading. Scanning. What We Can Do Online. Virtual College. Warm-Up Questions. SOHO. E- Vocabulary. Scanning.
1.17k views • 55 slides

Chapter 19 VPN and NAT
Chapter 19 VPN and NAT. Nelson Azadian Victor Seletskiy Pavel Dikhtyar. VPN Overview. Why we need Virtual Private Networks. What a Virtual Private Network consists of. What a Virtual Private Network does. How a Virtual Private Network does what it does. Pro’s and Con’s of VPN’s.
1.16k views • 69 slides

Chapter 05 Ad Hoc Networks
Chapter 05 Ad Hoc Networks. Outline. Introduction Unicast routing TCP on Mobile Ad Hoc Networks Selected security issues. 5.1 Mobile Ad Hoc Networks (MANET) Introduction and Generalities. 5.1.1 Mobile Ad Hoc Networks. Formed by wireless hosts which may be mobile
2.23k views • 187 slides

Computer Networks
Computer Networks. Why Computer Networks ?. Sharing Resources Sharing Data & Software Efficient Communication Using one database Saving time. Disadvantages of a Computer Networks. High cost to establish Spreading virus soon Need experts to maintain the network
949 views • 68 slides

Chapter 9: Virtual Memory
Chapter 9: Virtual Memory. Chapter 9: Virtual Memory. Background Demand Paging Process Creation Page Replacement Allocation of Frames Thrashing Demand Segmentation Operating System Examples. Background. Virtual memory – separation of user logical memory from physical memory.
1.12k views • 77 slides

Chapter 7 Packet-Switching Networks. Network Services and Internal Network Operation Packet Network Topology Datagrams and Virtual Circuits Routing in Packet Networks Shortest Path Routing. Chapter 7 Packet-Switching Networks. Network Services and Internal Network Operation. Network Layer.
1.15k views • 91 slides

Chapter 7 –Security in Networks
Chapter 7 –Security in Networks. Introduction to networks Threats against network applications Controls against network applications Firewalls Intrusion detection systems Private e-mail. Terminal-Host Systems. Created in the 1960s Central host computer does all the processing
1.61k views • 120 slides

Lecture 11: PKI, SSL and VPN Information Security – Theory vs. Reality 0368-4474-01 , Winter 2011. Yoav Nir. What is VPN. VPN stands for Virtual Private Network A private network is pretty obvious An Ethernet LAN running in my building Wifi with access control
1k views • 83 slides

Most Innovative Uses of Virtual Reality with Oculus apps
Most Innovative Uses of Virtual Reality with Oculus apps http://www.slideshare.net/scottgarza27/most-innovative-uses-of-virtual-reality-with-oculus-apps http://learnsauce.com/virtualrealitytutorial/ Innovative uses of Virtual Reality with Oculus apps can be ==> Virtual reality in Health care ==> Virtual reality in Military training ==> Virtual reality in Entertainment and many more Facebook : https://www.facebook.com/learnsauce Twitter : https://twitter.com/learnsauce Email : [email protected] Incoming Search Terms: "Virtual Reality Games" "Virtual Reality" "Virtual Reality Technology" "Virtual Reality Systems" "Virtual Reality Apps" "Virtual Gaming" "Virtual Reality Gaming" "Oculus Virtual Reality" "Virtual Reality Tutorials" "Virtual Reality Oculus Rift" "Oculus Rift Virtual Reality" "Virtual Reality Development" "Oculus Rift Virtual" "Virtual Reality Game"
1.23k views • 7 slides
Newly Launched - AI Presentation Maker

AI PPT Maker
Powerpoint Templates
Icon Bundle
Kpi Dashboard
Professional
Business Plans
Swot Analysis
Gantt Chart
Business Proposal
Marketing Plan
Project Management
Business Case
Business Model
Cyber Security
Business PPT
Digital Marketing
Digital Transformation
Human Resources
Product Management
Artificial Intelligence
Company Profile
Acknowledgement PPT
PPT Presentation
Reports Brochures
One Page Pitch
Interview PPT
All Categories

Virtual Private Network VPN Powerpoint Presentation Slides
Grab our professionally designed Virtual Private Networks VPN PowerPoint presentation. It briefly explains the overview of virtual private network, its features, types, applications and benefits. It also includes the process phases of implementing virtual private network along with the market scope of VPN. In addition, this Internet Protocol Security PPT contains the types of virtual private networks which include remote access, site-to-site, cloud VPNs. Furthermore, the module includes comparison of different virtual private network protocols, VPN and proxy servers, and a summarized comparison of all VPN protocols. Also, this VPN Protocols PPT presentation includes the overview, benefits, and demerits of various virtual private network protocols such as OpenVPN, IKEv2 or IPsec, SSTP, WireGuard, L2TP or IPsec, and PPTP. Lastly, this Remote Access PowerPoint Presentation outlines best practices, a checklist, a training budget, a timeline, a roadmap, and the impact of virtual private network. Download our 100 percent editable and customizable template, also compatible with Google Slides.

- Add a user to your subscription for free
You must be logged in to download this presentation.
PowerPoint presentation slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of ninety two slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.

People who downloaded this PowerPoint presentation also viewed the following :
- IT , Networking
- WireGuard ,
- Point To Point Tunneling Protocol ,
- Remote Access VPN ,
- Secure Socket Tunneling Protocol ,
- Proxy Servers
Content of this Powerpoint Presentation
Slide 1 : The slide introduces Virtual Private Network (VPN). State Your Company Name. Slide 2 : This is an Agenda slide. State your agendas here. Slide 3 : The slide displays Table of contents for the presentation. Slide 4 : The slide continues Title of contents. Slide 5 : This slide discusses the overview of virtual private network used for secure transfer of data through tunnelling protocols. Slide 6 : This slide outlines the pros of virtual private network which includes privacy protection, overcoming bandwidth, bypassing restrictions, etc. Slide 7 : This slide shows the main uses of virtual private network which include online anonymity, secure wi-fi, bypassing online censorship, etc. Slide 8 : The slide renders Title of contents further. Slide 9 : This slide discusses the market outlook of virtual private network in different years from 2022 to 2032. Slide 10 : The slide displays Title of contents further. Slide 11 : This slide gives an overview the introduction of remote access virtual private network to connect a private network. Slide 12 : The slide depicts Title of contents which is to be discussed further. Slide 13 : This slide discusses the introduction of site-to-site virtual private network for establishing connection between networks. Slide 14 : This slide outlines the categories of site-to-site Virtual Private Network which include intranet-based and extranet-based. Slide 15 : The slide displays another Title of contents. Slide 16 : This slide discusses the introduction of cloud virtual private network for secure connection through encryption and security protocols. Slide 17 : The slide renders Title of contents further. Slide 18 : This slide highlights the introduction and replacements of openvpn virtual private network protocol for secure transfer of data. Slide 19 : This slide outlines the advantages of open VPN which include robust security, extensive backing, customization, etc. Slide 20 : The slide displays another Title of contents. Slide 21 : This slide discusses the introduction of ikev2/ipsec protocol of virtual private network for secure transfer of data. Slide 22 : This slide showcases the pros of Ikev2/IPsec protocol in virtual private network which include speed, stability, and so on. Slide 23 : The slide again shows Title of contents. Slide 24 : This slide discusses the introduction of wireguard protocol in virtual private network for secure transfer of data. Slide 25 : This slide represents the configuration of WireGuard in windows 10 Virtual Private Network client. Slide 26 : This slide outlines the benefits and demerits of wireguard virtual private network protocol which include high speed, easy to use, etc. Slide 27 : The slide also renders Title of contents. Slide 28 : This slide discusses the introduction of secure socket tunneling virtual private network protocol for secure transfer. Slide 29 : This slide showcases the top providers of virtual private network with SSTP protocol, their features and comments. Slide 30 : This slide represents the working process of secure socket tunneling virtual private network protocol and its workflow. Slide 31 : This slide highlights the cons of secure socket tunneling virtual private network protocol which include security, internet speeds, and so on. Slide 32 : This slide outlines the problems faced by secure socket tunneling virtual private network protocol and related solutions. Slide 33 : The slide depicts Title of contents further. Slide 34 : This slide discusses the overview of layer two tunneling protocol in virtual private network for transfer of data. Slide 35 : This slide highlights the advantages of L2TP/ipsec virtual private network protocol which include security, wide availability, etc. Slide 36 : The slide displays Title of contents further. Slide 37 : This slide showcases the introduction and workflow of point-to-point tunneling virtual private network protocol. Slide 38 : This slide outlines the cons of point-to-point tunneling virtual private network protocol such as high-speed, user-friendly, etc. Slide 39 : This slide highlights the problems faced and related solutions of point-to-point tunneling virtual private network protocol. Slide 40 : The slide displays Title of contents which is to be discussed further. Slide 41 : This slide shows the working of virtual private network for secure and protected way of transferring data through various VPN protocols. Slide 42 : This slide represents the working of virtual private network for secure and protected way of transferring data through various VPN protocols. Slide 43 : The slide depicts another Title of contents. Slide 44 : This slide showcases the implementation setup of virtual private network which include collecting key components, prepping devices, etc. Slide 45 : The slide shows Title of contents further. Slide 46 : This slide discusses the working process of encryption in virtual private network for secure transfer of data. Slide 47 : This slide outlines the issues and troubleshooting ways in virtual private network which include connection issue, IP address visibility, etc. Slide 48 : The slide presents Title of contents which is to be discussed further. Slide 49 : This slide represents the difference between different virtual private network protocols on the basis of different aspects. Slide 50 : This slide highlights the comparison of WireGuard and OpenVPN protocols based on aspects such as speed, encryption, etc. Slide 51 : This slide renders the comparison of point-to-point tunneling protocol and Open Virtual Private Network protocol. Slide 52 : This slide outlines the difference between ipsec and open virtual private network protocols based on different factors. Slide 53 : This slide presents the comparison of layer two tunneling protocol and open virtual private network protocol based on aspects. Slide 54 : This slide showcases the difference of ipsec and openvpn protocols on the basis of aspects. Slide 55 : This slide represent the comparative analysis of IKEv2 and WireGuard on the basis of aspects such as stability, maturity, speed, and so on. Slide 56 : This slide highlights the difference between VPN and proxy servers based on aspects such as security features, supported protocols, etc. Slide 57 : The slide renders Title of contents further. Slide 58 : This slide provides the applications of virtual private network which includes elevating gaming experience, anonymous torrenting, and so on. Slide 59 : The slide also depicts Title of contents. Slide 60 : This slide contains the use of virtual private network for protection of data in healthcare and security. Slide 61 : This slide highlights the introduction and application of virtual private network in finance and banking. Slide 62 : This slide discusses the importance of virtual private network in online learning secure data transfer. Slide 63 : The slide displays Title of contents further. Slide 64 : This slide is to highlight the best approaches for virtual private network. Slide 65 : This slide showcases the checklist for implementing VPN which highlights the actions performed while utilizing virtual private network. Slide 66 : The slide displays Title of contents further. Slide 67 : This slide represents the training schedule for IT teams in an organization to efficiently implement virtual private network. Slide 68 : This slide showcases the breakdown cost for implementing virtual private network such as instructor, training cost, etc. Slide 69 : This slide continues the breakdown cost for implementing virtual private network such as hardware, software, IT staff, etc. Slide 70 : The slide represents Title of contents further. Slide 71 : This slide outlines the timeline for executing virtual private network including planning phase, requirement gathering, and so on. Slide 72 : This slide depicts the 30 60 90 days plan for virtual private network including tasks such as assessment, requirement gathering, etc. Slide 73 : This slide outlines the deployment for virtual private network along with steps including, selecting VPN technology, defining objectives, etc. Slide 74 : This slide showcases the performance tracking dashboard for virtual private network including components such as in traffic, out traffic, etc. Slide 75 : The slide renders Title of contents further. Slide 76 : This slide showcases the after VPN impact on business along with the various factors that have improved the overall performance. Slide 77 : This slide highlights the comparative analysis of the before versus after situation of an organization. Slide 78 : The slide also displays Title of contents. Slide 79 : This slide represents the virtual private network case study of softech along with problems faced, and their related solutions in the case study. Slide 80 : This slide shows all the icons included in the presentation. Slide 81 : This slide is titled as Additional Slides for moving forward. Slide 82 : This slide presents Bar chart with two products comparison. Slide 83 : This is a Timeline slide. Show data related to time intervals here. Slide 84 : This slide depicts Venn diagram with text boxes. Slide 85 : This is a Financial slide. Show your finance related stuff here. Slide 86 : This slide contains Puzzle with related icons and text. Slide 87 : This is Our Goal slide. State your firm's goals here. Slide 88 : This is an Idea Generation slide to state a new idea or highlight information, specifications etc. Slide 89 : This slide provides 30 60 90 Days Plan with text boxes. Slide 90 : This slide presents Roadmap with additional textboxes. Slide 91 : This slide shows Post It Notes. Post your important notes here. Slide 92 : This is a Thank You slide with address, contact numbers and email address.
Virtual Private Network VPN Powerpoint Presentation Slides with all 101 slides:
Use our Virtual Private Network VPN Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.

Ratings and Reviews
by Dannie Washington
March 31, 2024
by Deshawn Schmidt


- My presentations
Auth with social network:
Download presentation
We think you have liked this presentation. If you wish to download it, please recommend it to your friends in any social system. Share buttons are a little bit lower. Thank you!
Presentation is loading. Please wait.
Virtual Private Network (VPN)
Published by Theresa Fields Modified over 8 years ago
Similar presentations
Presentation on theme: "Virtual Private Network (VPN)"— Presentation transcript:

Virtual Private Networks COSC541 Project Jie Qin & Sihua Xu October 11, 2014.

1 Intel / Shiva VPN Solutions Stephen Wong System Engineer.

VPN: Virtual Private Network Presented by: Germaine Bacon Lizzi Beduya Betty Huang Jun Mitsuoka Juliet Polintan.

Setting Up a Virtual Private Network Chapter 9. Learning Objectives Understand the components and essential operations of virtual private networks (VPNs)

© 2006 Cisco Systems, Inc. All rights reserved.Cisco Public 1 Version 4.0 Prototyping the WAN Designing and Supporting Computer Networks – Chapter 8.

Virtual Private Networks. Why VPN Fast, secure and reliable communication between remote locations –Use leased lines to maintain a WAN. –Disadvantages.

SCSC 455 Computer Security Virtual Private Network (VPN)

1 Configuring Virtual Private Networks for Remote Clients and Networks.

Guide to Network Defense and Countermeasures Second Edition

Eric Kilroy. Introduction Virtual Private Network A way to connect to a private network through a public network such as the internet.

VPNs Virtual Private Networks. VPNs: Purpose Emulate a private network using shared Service Provider infrastructure Same policies as private network What.

1 IP VPN Nikolay Scarbnik. 2 Agenda Introduction………………………………………………………….3 VPN concept definition……………………………………………..4 VPN advantages……………...…………………………………….5.

In this section, we'll cover one of the foundations of network security issues, It talks about VPN (Virtual Private Networks). What..,Why..,and How….?

Goal of The Paper What exactly is a VPN? Why do you need a VPN? what are some of the technologies used in deploying a VPN? How does a VPN work?

Virtual Private Networks Globalizing LANs Timothy Hohman.

Virtual Private Networking Karlene R. Samuels COSC513.

Chapter 10 Virtual Private Networks. VPN Defined A segment of the public network made to appear part of a private network so that it can be used to.

VPN – Technologies and Solutions CS158B Network Management April 11, 2005 Alvin Tsang Eyob Solomon Wayne Tsui.
Remote Networking Architectures

Virtual Private Network (VPN) © N. Ganesan, Ph.D..
About project
© 2024 SlidePlayer.com Inc. All rights reserved.
What Is a VPN? Virtual Private Networks Explained
Understand what a VPN is, types of VPNs, VPN protection, and how to choose a VPN.
VPN Meaning: What Does VPN Stand For?
A VPN , meaning a virtual private network masks your Internet protocol (IP) address, creating a private connection from a public wi-fi connection. A VPN is one of the best tools for privacy and anonymity for a user connected to any public internet service because it establishes secure and encrypted connections.
Using a Wi-Fi network, especially one that is unsecured, means potential exposure of personal information to third parties, some of which may have malicious intentions. What is a VPN capable of? A VPN hides a lot of information, including your browsing history, your IP address , your location, your endpoint devices (whether you're on a Windows computer or an an Android smartphone), and your overall web activity. Cyber criminals often use unsecured connections to gain access to information that enables identity theft and other malicious activities. A VPN solution helps to protect against these activities by creating an encrypted tunnel for all data you send and receive, unobserved by others.
In the context of this VPN meaning, a VPN solution helps to protect against nefarious activities by creating an encrypted tunnel for all data you send and receive, unobserved by others. Data security can also be enhanced through VPN split tunneling , which enables users to route some traffic through their VPN and enable other traffic to retain direct access to the internet.
But in some cases, organizations may choose to install a VPN blocker to prevent employees from accessing sites that may hinder their productivity, such as social networking or shopping sites.
What Does a VPN Do?
VPNs use virtual connections to create a private network, keeping any device you connect to a public wi-fi safe from hackers and malware, and protecting sensitive information from unauthorized viewing or interception. A VPN routes your device’s connection through a private server rather than the ISP, so that when your data reaches the Internet, it’s not viewable as coming from your device.
A virtual network keeps your data private using encryption, which turns your information into unreadable gibberish only decipherable using a key, which is known to your device. Different VPNs use somewhat different encryption processes, but the general process includes tunneling and your data is encoded as it travels between your device and the server, which then decrypts the data and sends it on to your destination, such as a website. The encryption process prevents anyone who may intercept the data between you and the server, such as a government agency or hacker, from being able to decipher its contents.
Now that you know the answer to "What is VPN protection?" you might be curious about where it is most frequently used. Two of the best-known and most popular secure network protocols used in VPN technology are Internet Protocol Security (IPSec) and secure sockets layer (SSL). IPSec connections use pre-shared keys on clients and servers in order to encrypt and send traffic back and forth. SSL VPNs use public key cryptography to securely exchange encryption keys.
How Does a VPN Work?
Learn more on how a VPN works here .
Why Use a Virtual Private Network (VPN)?
Use of the Internet is now essential to global business, from shopping to banking to medicine to entertainment. Using Internet services involves transmitting very important information online, including credit card and social security numbers, and personal information, such as medical histories or home addresses. VPNs keep your Internet use safe from prying eyes, and, when used in a corporate setting, help keep business information from getting into the wrong hands.
For businesses who wonder "what is a VPN going to do for my company?" these provide improved security overall, improved remote access, independence from countries with strict Internet access laws, and a better total-cost-of-ownership when it comes to the aggregate costs of security and networking technologies used by corporate teams. VPNs can also provide safe and secure data sharing between employees and with individuals and groups outside of the business when necessary.
It is important to note that these do not make users completely anonymous on the Internet. Internet services requiring a login, such as Google or Facebook, know when you sign in, and websites can still leave cookies on your machine that identify your visits from particular Internet browsers. Anyone with direct access to the devices you use might also be able to view your activity. And law enforcement officials, depending on local legal authority, may be able to monitor your devices directly or require your virtual network service to give up records of your actions.
State of Zero Trust Report
Examine how organizations can be successful by using zero-trust strategies and solutions.
Types of Virtual Private Networks (VPN)
There are two main types of VPN that people can use to securely connect to corporate networks.
1. Remote Access VPN
A remote access VPN enables the user to connect their device to a network from outside their organization’s office. This device-to-network approach typically involves a user connecting their laptop, smartphone, or tablet to a network through their VPN.
Increasingly, advances in VPN technology enable security checks to be carried out to ensure the device is secure before it is granted permission to connect. Remote access VPNs include cloud VPNs , which enable users to securely access applications and data via their web browser.
2. Site-to-Site VPN
A site-to-site VPN enables connections between multiple networks. This network-to-network approach is typically used to connect multiple offices or branch locations to a central office. Site-to-site VPN encryption is useful for organizations with several offices based in various geographical locations. It enables them to share resources from a primary network, such as email servers or data storage facilities, across multiple locations. It also allows access to all users as if servers were located in the physical office.

Types of VPN Protection
There are several different types intended for different use cases. The three main categories are remote access , intranet-based site-to-site, and extranet-based site-to-site. Practically speaking, most users encounter VPNs depending on their use as individual, personal, or corporate.
1. Individual VPN
Individual VPNs refer to services meant for the personal use of individuals. Basic remote access networks, for example, allow users to connect to a secure remote server to access a private network. Reputable services include encryption to ensure the individual’s security isn’t compromised.
2. Business VPN
Business VPNs are intended for use by businesses in protecting their users and devices. Robust business networks deliver secure web connections to company devices, regardless of where employees connect to the Internet. Remote access business VPN creates a temporary VPN connection that encrypts data transmissions. After the data transmission stops, the business VPN disbands.
The limitations of remote access business VPN connections include increased lag time depending on the user's distance from the central network. A user may experience severe latency issues causing signal-quality degradation and disruptions for intensive data transmissions, such as video conference calls.
Business use cases often include site-to-site Virtual networks, which provide multiple users in various locations with the ability to securely access each other’s resources. Secure communication among business departments, including those in different countries, is critical for corporate security, business continuity, and employee productivity.
Site-to-site enterprise VPN may improve transmission speeds and reduce latency with higher bandwidth connection speeds and faster encryption.
The greater use of cloud services and applications increases the cybersecurity risk of relying solely on perimeter-based security protections. When using cloud services, enterprises using a corporate VPN also rely on cloud network security. Any unencrypted transmission or storage may cause a data breach.
Future of enterprise VPN
Corporate VPN security came under more scrutiny with the increased use by remote workers because cybercriminals take advantage of remote access vulnerabilities to gain unauthorized access to many corporate networks.
Here are some future insights into enterprise VPNs.
Enterprises need to know that VPN use continues to grow. The global VPN marketplace will reach $76.6 billion by 2030 with a 15.4% CAGR. A research study by Statista found that 41% of American and UK users use a VPN at least once per week. Another study found that 24% of VPN users use business VPNs. An additional 14% use business VPNs and personal VPNs.
What Should a Good VPN Do?
Good VPNs provide secure connections to corporate networks and are easy for people to use, all while maintaining fast, reliable browsing sessions. The key benefits of a good VPN include:
1. Encryption of IP address
A VPN service encrypts a user’s data and their IP address by bouncing network activity through secure chains connected to servers in another location. This ensures that the user’s IP address is hidden from cyber criminals even when they connect to public Wi-Fi networks. This VPN Wi-Fi feature allows the user to access the internet anonymously, safely, and securely.
2. Two-factor authentication
Relying on a VPN alone may not be enough to protect user data as it may still be vulnerable to phishing attacks . It is best to use two-factor authentication (2FA) to validate user identities whenever they log in to applications and networks. When a user logs in to an online service, they are requested to authenticate their identity through various options, such as confirming a one-time password (OTP), entering a code from an authentication app, or using their fingerprint.
2FA and multi-factor authentication (MFA) are critical to preventing unauthorized access. They add an extra layer of security and ensure that a hacker cannot access accounts even if they manage to obtain users’ login credentials.
3. Security when working remotely
The use of VPNs is particularly important as people continue to work remotely across distributed workforces. The encryption features that VPNs offer are vital to maintaining the confidentiality of data and keeping browsing activity private, no matter where users access corporate networks from. Remote workers can connect to office networks and access sensitive materials from their own devices.
Home-based workers can also enhance their security by using a VPN router , which manages connections to the VPN from various devices.
Choosing Your VPN Service
The following considerations should help guide selection of a VPN service.
Free vs paid: Free services are readily available, but often come with significantly limited functionality or a “catch” that makes up for the revenue the VPN provider isn’t making from you directly—such as tracking you online and selling your personal or browsing data to advertisers.
Secure communications protocols : The robustness of security in VPN tunnels depends on which security protocols are used. Be sure to review these protocols with your provider to ensure appropriate levels of security.
Data privacy protection : Provider privacy agreements can vary widely. Does your VPN provider keep traffic logs? Do its servers operate in countries with strict Internet governance laws and/or oppressive governments?
Capacity and scale : Some providers significantly throttle data, or impose limits on servers and other connecting devices. Consult your provider’s terms of service to ensure the right capacity for your business and that your VPN won’t be unduly limited.
Kill switch availability : A kill switch monitors your connection to the VPN’s server, so if the connection drops or fails, your device is automatically blocked from accidental exposure. Consider kill switch functionality a “last line of defense” that keeps your Internet connection blocked until the tunnel can be restored.
How Fortinet Can Help?
In today’s rapidly evolving cybersecurity environment, VPN alone may not be enough to secure sensitive data and keep your organization’s network safe. Whether users are in the office, at home, or on the road, they need consistent and secure access to applications in the cloud, data center, and SaaS platforms.
Fortinet helps organizations to secure and connect their work-from-anywhere employees and devices to critical applications and resources. Fortinet Universal ZTNA is a robust security solution that offers businesses flexibility, granular access control, and ongoing verification. It enables policies to be enforced for users regardless of location. With granular access control, access is granted to specific applications only for that session, providing better security. With the client-initiated model, the IT team has more visibility and control of the endpoint while providing users with a faster, easier experience. Universal ZTNA requires no additional licenses and is a free feature in FortiOS and FortiClient , allowing customers to shift from VPN to ZTNA at their own pace. With Fortinet’s added flexibility, you don’t need to choose exclusively between VPN or ZTNA; you can adapt to the solution that’s right for you.

Because of continual movement between on-premises, home network, and public network environments, zero trust, endpoint, and network security must be connected through a centralized security and management framework. Solutions unified by a common set of APIs and integration points ensure users can seamlessly shift from one location to another, enjoying a consistent user experience that is appropriately protected with contextual security. Fortinet is the only vendor capable of delivering this unified approach, enabling proactive, integrated, and context-aware security that automatically adapts to where users are, what device they are using, and what resources they are accessing.
Using a broad portfolio of zero trust, endpoint, and network security solutions within the Fortinet Security Fabric, Fortinet can deliver security, services, and threat intelligence that can automatically follow users across distributed networks. The Security Fabric can also adjust enforcement to the perceived risk of every interaction—whether on the road, at home, or in the office to enable consistent enterprise-grade protection and enhance productivity end-to-end.
Learn more about how Fortinet ZTNA improves secure access to applications anywhere, for remote users.
What is a VPN and what does VPN stand for?
VPN, meaning a virtual private network masks your Internet protocol (IP) address, creating a private connection from a public wi-fi connection.
What does a VPN do and how does it work?
VPNs use virtual connections to create a private network, keeping any device you connect to a public wi-fi safe from hackers and malware, and protecting sensitive information from unauthorized viewing or interception.

Why use a virtual private network (VPN)?
VPNs mask the user's IP address to keep your Internet use safe from prying eyes, and, when used in a corporate setting, help keep business information from getting into the wrong hands.
VPN Resources
- How Does VPN Work
- Proxy vs VPN
- Are VPNs Safe
- VPN Split Tunneling
- What is Site-to-Site VPN
- VPN Blocker
- Benefits of VPN
- VPN Routers
- Remote Access VPN
- ZTNA vs VPN
Quick Links
- FortiClient Downloads
- Free FortiClient Demo
- Analyst Reports
Why You Need a VPN, and How to Choose the Right One
VPNs can protect your privacy, if you use them right. We explain what VPNs do, what they don't, and how to get the most out of a VPN.

Since my start in 2008, I've covered a wide variety of topics from space missions to fax service reviews. At PCMag, much of my work has been focused on security and privacy services, as well as a video game or two. I also write the occasional security columns, focused on making information security practical for normal people. I helped organize the Ziff Davis Creators Guild union and currently serve as its Unit Chair.
I'm a senior analyst charged with testing and reviewing VPNs and other security apps for PCMag. I grew up in the heart of Silicon Valley and have been involved with technology since the 1990s. Previously at PCMag, I was a hardware analyst benchmarking and reviewing consumer gadgets and PC hardware such as desktop processors, GPUs, monitors, and internal storage. I've also worked as a freelancer for Gadget Review, VPN.com, and Digital Trends, wading through seas of hardware and software at every turn. In my free time, you’ll find me shredding the slopes on my snowboard in the Rocky Mountains where I live, or using my culinary-degree skills to whip up a dish in the kitchen for friends.

VPNs have gone from being an obscure networking utility to big business. You've probably seen the ads from your favorite YouTuber, on podcasts, and even during the Superbowl with claims about how a VPN can make you anonymous or let you access free video streaming. Do the products live up to the hype? Although VPNs can be useful tools for protecting your privacy, it's important to understand how these tools work so you can decide whether they will help you. We break down what VPNs do and what they don't do to help you understand why you'd want one and how to pick the one that's best for you.
Our Top-Rated VPN Services
- NordVPN Review
- Check Price
Surfshark VPN Review
Proton vpn review.
- TunnelBear VPN Review
Mullvad VPN Review
Ivpn review, what is a vpn.
VPN stands for virtual private network. When we talk about VPNs, we're usually talking about a commercial VPN being sold directly to consumers for use in day-to-day life, but the idea of VPNs has much broader applications than that. Corporations have long used VPN technology to let workers access digital resources no matter where they are, long before COVID-19 made work from home the norm.
When you switch on a VPN, it creates an encrypted connection (sometimes called a "tunnel") between your device and a remote server operated by the VPN service . All your internet traffic is routed through this tunnel to the server, which then sends the traffic off to the public internet as usual. Data coming back to your device makes the same trip: from the internet, to the VPN server, through the encrypted connection, and back to your machine.

Keep in mind that you don't need another company to set up a VPN. There are a few options out there to set up your own, such as Outline . Doing so is fairly straightforward, but you'll either need to maintain a server or rent one, which is less simple. While there are some efforts to make self-hosted VPNs more accessible, it's something best left to tinkerers who are eager to get their hands (digitally) dirty.
Do VPNs Make You Anonymous Online?
By encrypting your traffic and routing it through a VPN server, it is harder but not impossible for observers to identify you and track your movements online. No VPNs provide total anonymity, but they can help improve your privacy.
For example, your internet service provider (ISP) is probably the single entity with the most insight into what you do online. The FTC issued a report in 2021 outlining exactly how much your ISP knows about what you do online, and it's a lot. Worse, thanks to Congress, your ISP can sell anonymized customer data. If you don't like that a company you're already paying is profiting from your data, or if you have concerns about ISPs hoarding detailed information about your activities, a VPN will help. Not even your ISP can see your web traffic when you use a VPN.
VPNs also make it harder for advertisers and others to track you online. Normally, data is transmitted from the internet to your device using its IP address. When the VPN is active, your true IP address is hidden, and anyone watching you can only see the IP address of the VPN server. By hiding your real IP address, VPNs deny snoops one tool used to identify and track you online.
Despite that, VPNs do not make you fully anonymous online. Advertisers, for instance, have numerous ways to identify and track you as you move across the web. Trackers and cookies in websites try to uniquely identify you and then watch for where you appear next.
Sites and advertisers can also identify you by noting several unique characteristics, such as browser version, screen size, and so on. This information is harmless on its own, but when companies compile enough of these identifiers, they form a unique signature—so much so that the process is called browser fingerprinting .
That's not to mention the privacy we give up in exchange for services. Amazon, Google, and Meta (formerly Facebook) have become pillars of the modern internet infrastructure and are impossible to avoid completely. Even if you deleted all your accounts and never used them again, they'd still probably be able to harvest data on you.
These privacy threats require tools other than VPNs. Ad and tracker blockers , like those found in some browsers or as standalone tools like the EFF's Privacy Badger , address some of these concerns.
Using Tor can guard your privacy even better than a VPN and grant you access to the Dark Web. Unlike a VPN, Tor bounces your traffic through several volunteer server nodes, making it much harder to trace. It's also managed by a nonprofit organization and distributed for free. Some VPN services will even connect to Tor via VPN, making this arcane system easier to access. The cost of your internet connection is high, however, as using Tor will degrade your connection much more than a VPN. Tor isn't perfect either, and it, too, has plenty of weaknesses to consider.
Keep in mind that law enforcement and government agencies have access to more advanced and invasive techniques. Given enough time, a determined, well-funded adversary can usually get what it's after.
Do VPNs Protect Against Malware?
Several VPNs say they include some protection against malicious files. Sometimes, this is basic protection against known malicious sites and files. Some VPN services include dedicated antivirus tools as well, and some antivirus companies now offer VPNs.
We don't typically test the malware-detecting abilities of VPNs since we view VPNs primarily as a privacy service. To address the threat of malware, we believe standalone anti-malware software—whether it's one you buy or the one that ships with your computer—does a better job. We believe VPNs should pay as little attention to your web traffic as possible.
Do VPNs Keep You Safe Online?
A VPN will hide the contents of your web traffic from some observers and can make it harder for you to be tracked online. But a VPN can, at best, provide only limited protection against the threats you're most likely to encounter on the web: malware, social engineering scams, and phishing sites.
There are better ways to address these threats. Your browser has built-in tools for detecting phishing sites , and so do most antivirus apps, so pay attention when you see a warning. Use common sense if you see a suspicious pop-up window or receive an unusual email prompting you to take some action. Many people reuse passwords and use weak passwords, so get a password manager to generate and store unique and complex passwords for each site and service you use. Finally, protect your online accounts and enable multi-factor authentication wherever it's available.

Do VPNs Hide Your Torrenting and Online Activity?
When a VPN is active, all your traffic is encrypted. This means your ISP can't see the sites you're visiting or the files you're moving.
But while your ISP maybe can't see you're Torrenting the entire run of Great British Bake Off , they can surmise you're using a lot of bandwidth. This alone may be a violation of your terms and conditions. Pirating content may also violate your VPN's terms and conditions, so be sure to check carefully.
Can VPNs Bypass Censorship?
With a VPN, it's possible to connect to a VPN server in another country and browse the web as if you were physically where the VPN server is. This can, in some cases, get around local content restrictions and other kinds of censorship. It's easily the noblest use of a VPN, and VPN companies will often play up their role in protecting internet freedom.
Although it should work, it's important to know that a VPN doesn't make your traffic invisible. Observers can see encrypted traffic, but they shouldn't be able to see the contents of the traffic. However, the encrypted traffic alone might attract unwanted attention. Some VPNs include modes that aim to disguise VPN traffic as more common HTTPS traffic.
We don't test the ability of VPNs to bypass censorship and have grave concerns endorsing a VPN service for this ability could put people's lives at risk if we got it wrong. Simply using a VPN may get you into legal hot water, depending on where you are, so know the risks before you try. Remember, no tool can provide total protection, particularly against a well-funded and capable adversary—a nation-state, for example.
Can VPNs Spoof Your Location?
With a VPN, you can connect to a server in a different country and spoof your location . One of the ways to determine where an internet-connected machine is located is to look at its IP address. These addresses are distributed geographically and can sometimes be quite close to your true location. By hiding your true IP address behind the IP address of a VPN server, your true location can be obscured.
Recommended by Our Editors
But remember that sites and services sometimes have other means of determining your location. Also, many sites are sensitive to changes in expected behavior. If your bank sees someone claiming to be you connecting from Latvia, it may require them to do some additional security checks before granting access. That's generally a good thing, but it can be daunting when it's you using the VPN and not a scammer.
Can VPNs Unblock Streaming Content?
Streaming services sometimes offer different content to different countries. Until recently, UK residents could watch Star Trek: Discovery on Netflix, while US residents had to use Paramount+ . From the comfort of your home, you can pop over to a far-away VPN server, perhaps to access streaming video unavailable in the US .
Just like government censorship, streaming services know many people use VPNs to access their content and actively work to prevent it. So, while you can use a VPN to stream video online, and we are sure most of you reading this are, it may work, but it may also stop working tomorrow.
Can You Trust a VPN?
The biggest problem with VPNs isn't an issue of technology but one of trust. Because all your traffic is passing through its systems, a VPN company is in the same position as an ISP. It could, if it wished, see everything you do online and sell that data. It could inject ads into the websites you view. It could keep unnecessary amounts of data it could then be compelled to hand over to law enforcement.
VPNs are eager to receive that trust, but proving they deserve that trust is difficult. When we review a VPN, we pore over its privacy policy and send out a questionnaire to get a sense of what efforts each company makes to protect customers' privacy. We know they could lie to us, but our goal is to put them on record.
We want to see VPNs taking every possible measure to protect their customers, but we also need to see transparency. Even when we don't agree with all their choices, we prefer companies that are upfront about their operations. A VPN should also issue a transparency report outlining what requests the company has received from law enforcement and how the company responded.
We also like to see third-party audits of VPN services that validate policies and the security of the company's infrastructure. We have to acknowledge that audits are imperfect tools . Audits are commissioned by the VPN company, and the company also outlines the scope of the audit. Still, it's a valuable way to demonstrate a company's commitment to transparency.
Do I Need a VPN?
A few years ago, VPNs had a better-defined place in your privacy and security toolbox. Back then, most traffic traveled via HTTP, sometimes without any encryption whatsoever. Nowadays, most web traffic is sent via HTTPS, which encrypts your connection. Looking at HTTPS traffic, an ISP or someone spying on your network can only see the highest level of your traffic's destination. That's like seeing PCMag.com and not PCMag.com/max-is-great.
Advertisers have also become more sophisticated in their tracking efforts. Browser fingerprinting and other techniques mean a VPN's anonymizing abilities are curbed somewhat. Even a VPN’s lauded ability to spoof locations, bypass censorship, and unblock streaming is less certain as companies and governments have become increasingly aggressive in detecting and blocking VPN traffic.
The rise of sophisticated tracking methods and HTTPS are often cited as reasons VPNs aren't worth the money. But it depends on why you need a VPN. If, for whatever reason, you want your traffic to appear to be coming from another country, a VPN will do that. If you want to make it a little harder for advertisers and others to track you as you move across the web, a VPN can help do that, too. And if you want to ensure your ISP knows as little about your online activity as possible, a VPN can help there, too.
A VPN will not make you invincible online, but it can help protect your privacy. It's a valuable part of your security and privacy toolbox, and like every tool, a VPN works best when you use it for the right job.
Like What You're Reading?
Sign up for SecurityWatch newsletter for our top privacy and security stories delivered right to your inbox.
This newsletter may contain advertising, deals, or affiliate links. Subscribing to a newsletter indicates your consent to our Terms of Use and Privacy Policy . You may unsubscribe from the newsletters at any time.
Your subscription has been confirmed. Keep an eye on your inbox!
About Max Eddy
Lead security analyst.

Read Max's full bio
Read the latest from Max Eddy
- How to Set Up and Use a VPN
- The 28 Most Niche Simulation PC Games We Could Find
- VPN vs. Proxy: What's the Difference?
- Credit Card Skimmers and Shimmers: Everything You Need to Know to Stay Safe
- More from Max Eddy
About Chris Stobing
Senior analyst, security.

Read Chris's full bio
Read the latest from Chris Stobing
- The Best VPNs for Brazil in 2024
- The Best VPN Services for 2024
- Norton Ultra VPN Plus Review
- The Best VPN Extensions for Chrome in 2024
- More from Chris Stobing
Table of Contents
Further reading.
How-To Geek
What is a vpn, and why would i need one.

Your changes have been saved
Email is sent
Email has already been sent
Please verify your email address.
You’ve reached your account maximum for followed topics.
Quick Links
What is a vpn, what is a vpn used for, what else does a vpn do, how does a vpn work, what is p2p specialty service for a vpn, how do you get a vpn, and which one should you choose, using a vpn in windows, how to use a vpn on iphone, how to use a vpn on android, our vpn recommendations, key takeaways.
A virtual private network (VPN) encrypts your internet traffic and then routes it through your VPN provider's server before you connect to a website or another online service. This helps disguise your identity and activity on the internet. VPNs can be used to bypass geographic restrictions, shield your activity on public Wi-Fi, and hide your real IP address when browsing and using software like BitTorrent.
A VPN, or Virtual Private Network, allows you to create a secure connection to another network over the Internet. VPNs can be used to access region-restricted websites, shield your browsing activity from prying eyes on public Wi-Fi, and more.
In very simple terms, a VPN connects your PC, smartphone, or tablet to another computer (called a server) somewhere on the internet, and allows you to browse the internet using that computer's internet connection. So if that server is in a different country, it will appear as if you are coming from that country, and you can potentially access things that you couldn't normally.
VPNs essentially forward all your network traffic to the virtual network, which is where the benefits -- like accessing local network resources remotely and bypassing Internet censorship -- all come from. Most operating systems have integrated VPN support.
VPNs originally were just a way to connect business networks together securely over the internet or allow you to access a business network from home, but their uses have grown well beyond that.
So how does this help you? Good question! You can use a VPN to:
- Bypass geographic restrictions on websites or streaming audio and video.
- Watch streaming media like Netflix and Hulu.
- Protect yourself from snooping on untrustworthy Wi-Fi hotspots.
- Gain at least some anonymity online by hiding your true location.
- Protect yourself from being logged while torrenting.
Many people these days are using a VPN for torrenting or bypassing geographic restrictions to watch content in a different country. They are still very useful for protecting yourself while working at a coffee shop, but that's hardly the only use anymore.
Everything You Need to Know About VPNs | ||
|---|---|---|
Which Is the Best VPN? | | | | | |
Additional VPN Guides | | | | | | | | | | |
VPN Reviews | | | | | | | |
VPNs are a fairly simple tool, but they can be used to do a wide variety of things:
- Access a Business Network While Traveling : VPNs are frequently used by business travelers to access their business network, including all its local network resources, while on the road. The local resources don't have to be exposed directly to the Internet, which increases security.
- Access Your Home Network While Traveling : You can also set up your own VPN to access your own network while traveling. This will allow you to access a Windows Remote Desktop over the Internet , use local file shares, and play games over the Internet as if you were on the same LAN (local area network).
- Hide Your Browsing Activity From Your Local Network and ISP : If you're using a public Wi-Fi connection , your browsing activity on non-HTTPS websites is visible to everyone nearby, if they know how to look. If you want to hide your browsing activity for a bit more privacy, you can connect to a VPN. The local network will only see a single, secure VPN connection. All the other traffic will travel over the VPN connection. While this can be used to bypass connection-monitoring by your Internet service provider, bear in mind that VPN providers may opt to log the traffic on their ends.
- Access Geo-Blocked Websites : Whether you're an American trying to access your Netflix account while traveling out of the country or you wish you could use American media sites like Netflix, Pandora, and Hulu, you'll be able to access these region-restricted services if you connect to a VPN located in the USA.
- Bypass Internet Censorship : Many Chinese people use VPNs to get around the Great Firewall of China and gain access to the entire Internet. (However, the Great Firewall has apparently started interfering with VPNs recently.)
- Downloading Files : Yes, let's be honest -- many people use VPN connections to download files via BitTorrent . This can actually be useful even if you're downloading completely legal torrents -- if your ISP is throttling BitTorrent and making it extremely slow, you can use BitTorrent on a VPN to get faster speeds. The same is true for other types of traffic your ISP might interfere with (unless they interfere with VPN traffic itself.)
Related: Do You Really Need to Have Your VPN On All the Time?
When you connect your computer (or another device, such as a smartphone or tablet) to a VPN, the computer acts as if it's on the same local network as the VPN. All your network traffic is sent over a secure connection to the VPN. Because your computer behaves as if it's on the network, this allows you to securely access local network resources even when you're on the other side of the world. You'll also be able to use the Internet as if you were present at the VPN's location, which has some benefits if you're using public Wi-Fi or want to access geo-blocked websites .
When you browse the web while connected to a VPN, your computer contacts the website through the encrypted VPN connection. The VPN forwards the request for you and forwards the response from the website back through the secure connection. If you're using a USA-based VPN to access Netflix , Netflix will see your connection as coming from within the USA.
Some VPNs offer special servers that are optimized to function with peer-to-peer (P2P) services. Common examples of P2P services include:
- BitTorrent (and other torrent programs)
- Some multiplayer gaming services
- Some voice chat services
- Plenty of messaging apps
Because of how they work --- and how they're often used --- P2P services are sometimes blocked by VPN providers. Using a dedicated P2P server may improve performance and reduce your chances of running into technical difficulties. You may even find that your VPN provider will switch you to connect to a special P2P VPN server if you're doing something like torrenting.
P2P VPN servers aren't inherently less secure than any other VPN server you might use, so there really isn't any downside to using one, and there are some potential benefits.
Related: What Is a SeedBox, and Why Would You Want One?
Depending on your needs, you can either use a VPN from your workplace, create a VPN server yourself, or sometimes host one out of your house -- but realistically, the vast majority of people are just looking for something to protect them while torrenting or help them watch some media online that they can't seem to access from their country. Not all VPNs provide exactly the same functionality, and you might have specific requirements for a VPN.
The easiest thing to do is pick one of the best VPNs , sign up, and download the VPN client for your Windows PC, Mac, Android, iPhone, or iPad. It's as easy as that.
These are some of our favorite VPNs:
- ExpressVPN : This VPN service has the best combination of ease of use, speedy servers, and support for streaming media and torrenting---all for a reasonable price. It has apps for every major platform as well as routers , streaming devices, and more.
- Private Internet Access (PIA) : PIA works well, with lots of fast servers available, and is a bargain at a low price. Unlike some services, it stays at that low price, even after the introductory period.
- NordVPN : NordVPN is a great all-around VPN that's easy to set up and use. NordVPN has a great Windows application particular, making it a great pick for Windows users.
If you have absolutely no idea which VPN you should use, pick ExpressVPN . It is a great all-around VPN and will meet the needs of most people.
Connecting to a VPN on Windows is fairly simple. If you've chosen a VPN service, you should generally use that VPN service's app for an easy connection experience. You can also configure a VPN connection manually, which is particularly useful for VPNs provided to you by your employer or other organization.
In Windows 10 or Windows 11, press the Windows key, type VPN, and click the "Add a VPN Connection" option, then select "Add a VPN Connection."
You can access the VPN window by navigating to Settings > Network & Internet > VPN on Windows 10 and Windows 11.
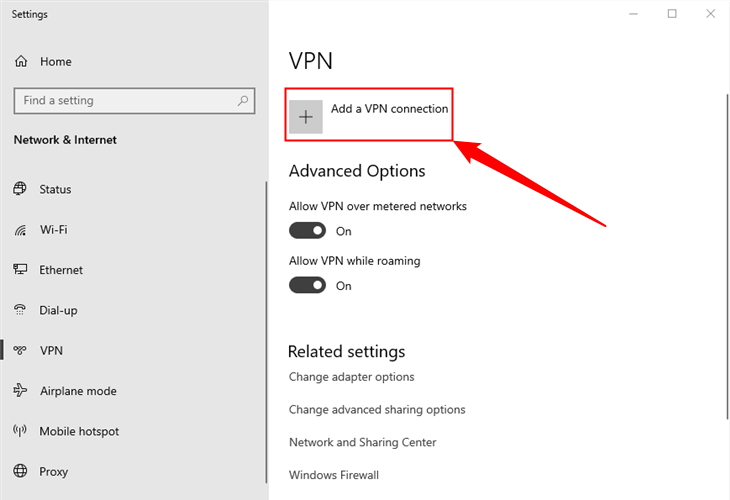
Use the wizard to enter the address and login credentials of the VPN service you want to use. You can then connect to and disconnect from VPNs using the network icon in the system tray -- the same one where you manage the Wi-Fi networks you're connected to.
Related: How to Connect to a VPN in Windows
Most of the best VPNs also have apps you can install on your phone, and we'd generally recommend you use the app if you want to connect to a VPN on your iPhone . You can add a VPN manually, but it requires entering a ton of details about the VPN --- a task best avoided if possible.
You must first launch the app and give it permission to run before you can activate it through the VPN menu. Then open the Settings app and navigate to General > VPN & Device Management to toggle the VPN on and off.
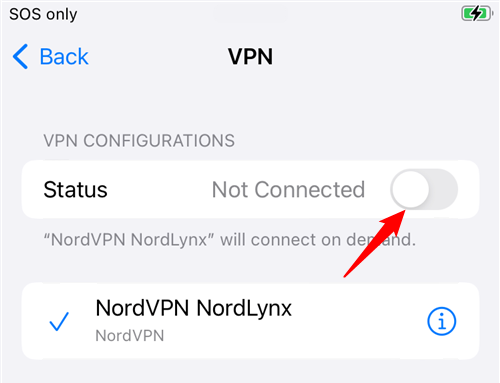
When the VPN is active, the toggle will turn green, the status will read "Connected," and "VPN" will be displayed at the top of your screen.
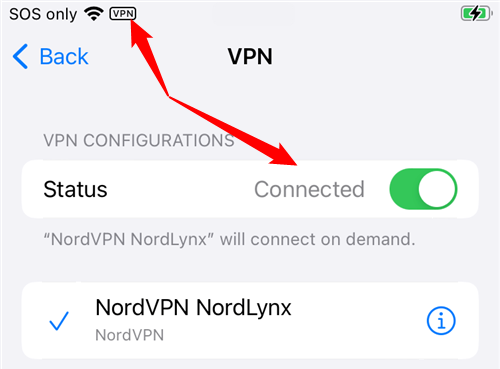
If you must add a VPN manually, click "Add VPN Configuration," listed under the VPNs you have installed and fill in the required details.
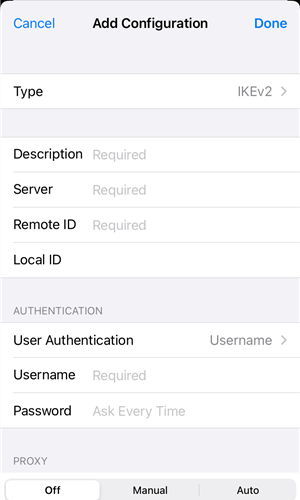
Related: How to Connect to a VPN From Your iPhone or iPad
Android devices --- just like iPhones or PCs --- can connect to a VPN using an installed app, or manually, using Android's built-in options.
These instructions are for "Pure Android," and things will be different on customized versions of Android, like what you find on Samsung's devices.
Open the Settings app, navigate to Network and Internet > VPN, then tap the VPN you'd like to activate if you installed a VPN app. You can also tap the gear to adjust the settings.
Tap the plus icon in the upper-right corner of the screen to manually add a new VPN.

You must fill out all of the details for the VPN you want to connect to. It is a bit annoying, so you're better off.
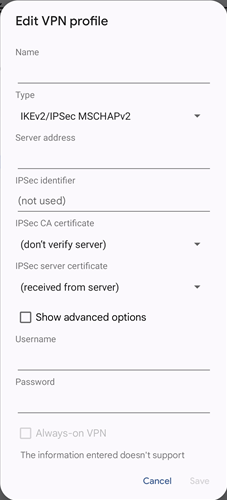
When a VPN is active, you'll see a small key icon at the top of your screen.
Related: How to Use a VPN on Android
If you're just getting started with VPNs and want the best VPN for using on public Wi-Fi hotspots or accessing region-restricted websites, there are a few great, simple options. Keep an eye out for deals, too, as most VPNs frequently offer great bargains for two- or three-year subscriptions.
You may also be interested in setting up a VPN on your own server , which you can do with Wireguard, OpenVPN , OpenWRT , on Windows , or on Linux . Of course, this won't allow you to access geo-blocked websites --- unless you're traveling outside the country and accessing your own network remotely.
- Collections
- VPN PPT Template
VPN PowerPoint Presentation Template and Google Slides
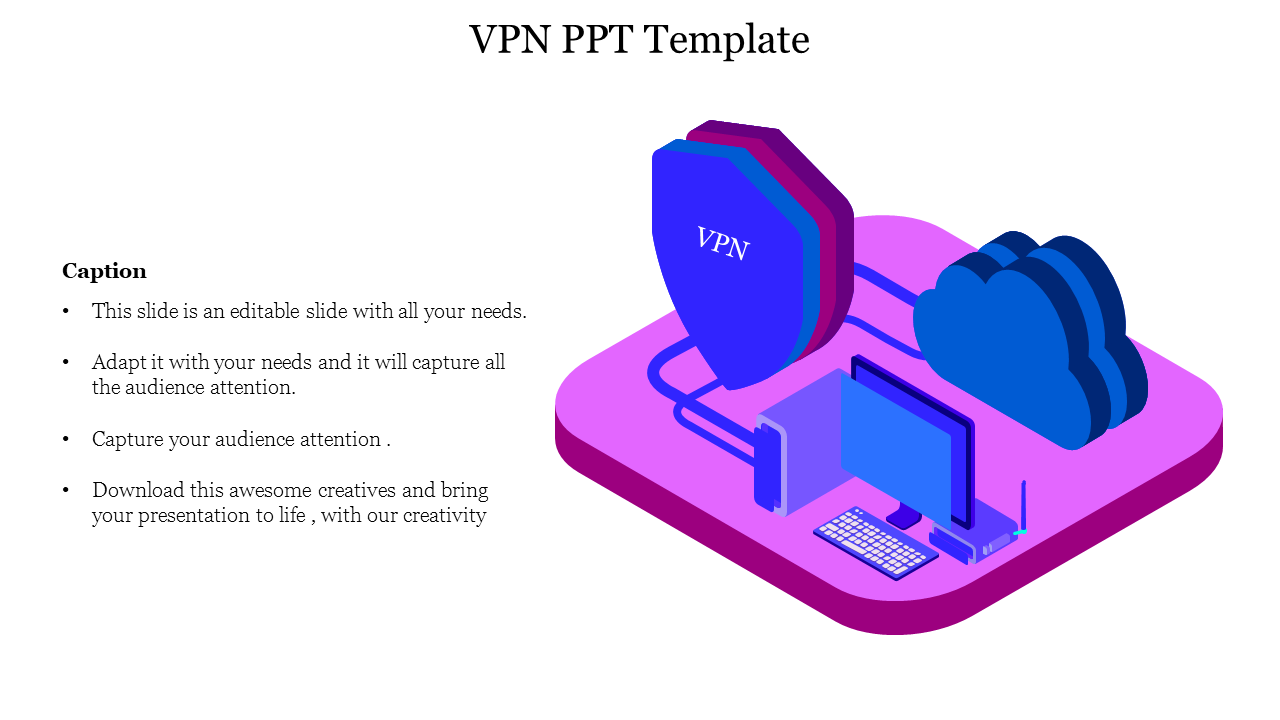
VPN Presentation Slide
Features of the template:.
- 100% customizable slides and easy to download.
- The template contains 16:9 and 4:3 format.
- Easy to change the slide's colors.
- Highly compatible with PowerPoint.
- Highly compatible with PowerPoint, Google Slides and Canva template.
- Virtual Private Networks
- VPN Security
- VPN Security System
- VPN Security Model
- Google Slides
324+ Templates

1614+ Templates
Artificial Intelligence
219+ Templates
136+ Templates

47+ Templates
Cloud computing
185+ Templates
Cyber security
261+ Templates
Mobile Phones
221+ Templates
26+ Templates
66+ Templates
You May Also Like These PowerPoint Templates

Strengthen your online privacy
Download Norton Secure VPN to encrypt your connection to help access content, hide your browsing activity, and safeguard the data you share.
Install Norton Secure VPN to encrypt your connection to help access content and hide your browsing activity.
Go to Account to download services
- Account info
- Preferences
- Billing info
- Order history
- Enter your Product Key
What is a VPN and what does it do?
A VPN is a service that establishes a secure, encrypted connection for your internet traffic, keeping your online activity hidden and protecting your privacy. The best VPNs have a no-log policy, bank-grade encryption, and a variety of servers around the world to help you browse anonymously.

- Written by Luis Corrons
- Updated: April 09, 2024 8 min read
Ever check your bank account or type in your credit card number to buy something online or while running errands? If you've done this without connecting to a virtual private network (VPN), you could have exposed your private information and browsing habits to cybercriminals or other snoops lurking on the same network.
Keep reading to learn how to stay securely connected on the go and how different types of VPNs can help keep your online sessions safe.
What is the definition of a VPN?
VPN stands for virtual private network—it’s technology that encrypts your data when you use the internet, scrambling it so that strangers on the same network can’t read it. A VPN creates a secure tunnel between your device and the internet to protect data during transmission. This secure tunnel helps VPNs disguise your IP address, mask your online activity (including links you click and files you download), and hide your physical location to help you access your favorite content.
A VPN gets its name because it embodies the following characteristics:
- Virtual: Functions without physical cables and instead relies on digital pathways.
- Private: Enhances online privacy by shielding data and browsing activity from snoops.
- Networked: Establishes and maintains a connection between a device and a VPN server.
How do VPNs work?
VPNs encrypt the connection between your device and network, which helps strengthen online privacy and security. This is the process a VPN follows after you connect and begin your search:
- You enter a search query, visit a website, etc.
- The request passes through the VPN client on your device.
- The VPN client establishes a secure tunnel to the server, encrypting the data in transit.
- The VPN server forwards the request to the internet.
- The internet processes the request.
- The internet sends a result back to the VPN server through the secure tunnel.
- The VPN server responds to your device through the VPN client.
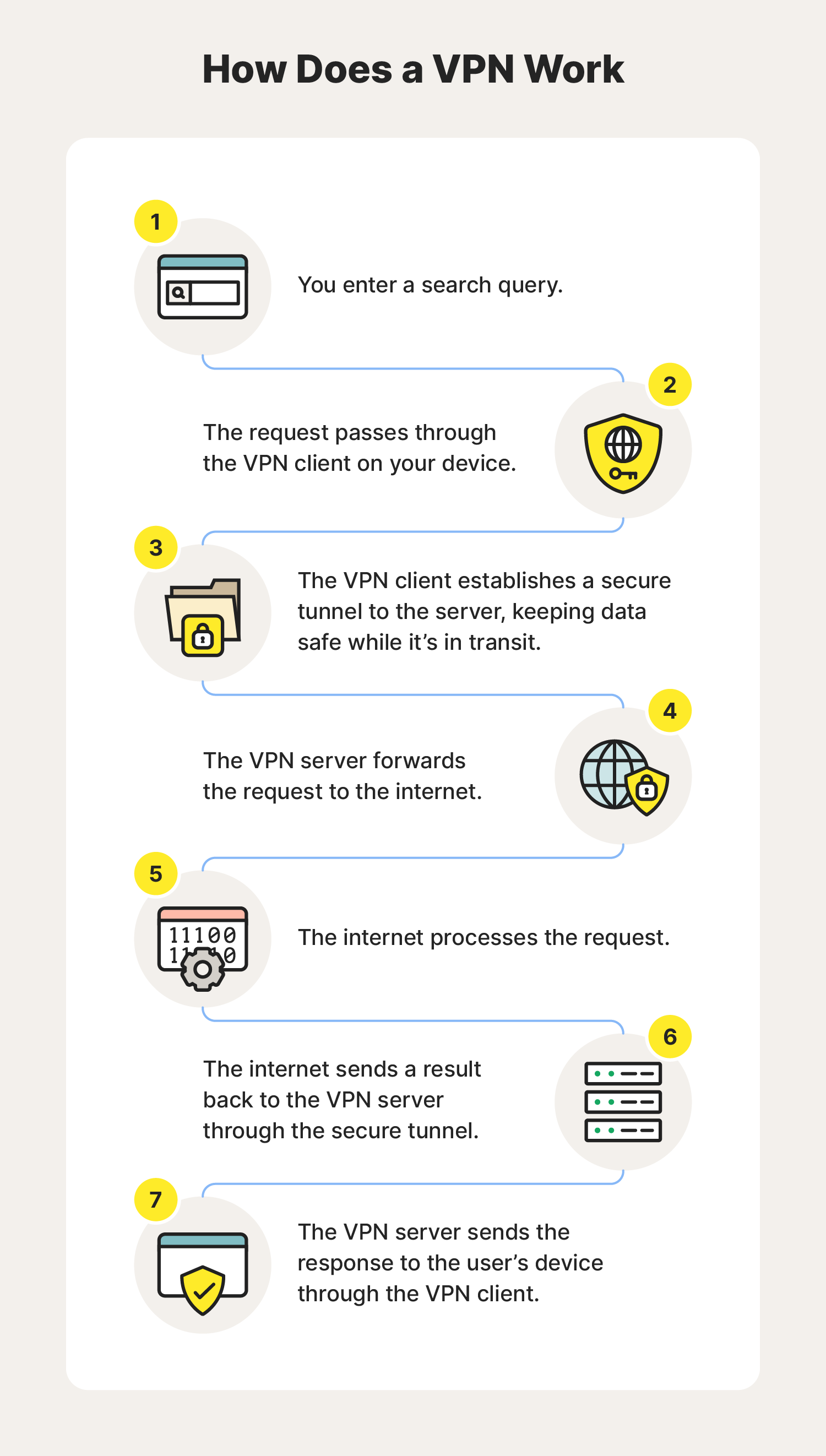
What does a VPN do and what are the benefits of using one?
VPN encryption capabilities help you browse anonymously, access content more freely, protect in-transit data, stop websites from tracking you, and protect your private information. Here are some more details about these VPN benefits :
- Anonymous browsing: A no-log VPN can help hide your IP address from websites, cybercriminals, the government, and even your internet service provider (ISP).
- Access content freely: VPNs are useful resources for journalists and travelers. They can help you access content that may be otherwise unavailable in your location.
- Data protection: VPNs encrypt your internet traffic, making it safer to access financial accounts, private data, and other sensitive information online without others eavesdropping.
- Less online tracking: Advertisers track much of your online activity using computer cookies . VPNs can help make it harder for them to track and monitor your activity by obscuring your IP address.
- Protection on public Wi-Fi: Unsecured public Wi-Fi networks are notorious places for hackers to steal information; a VPN can help stop this by hiding your internet session activity so cybercriminals can’t see what you’re doing.
Who needs a VPN service and why?
A VPN can help provide an additional layer of online privacy, protection when sending and receiving data, and anonymity while browsing online. By disguising IP addresses and encrypting in-transit data, VPNs are useful tools for online banking, journalism, activism, accessing content while traveling, accessing the dark web, and more.
Here are some of the different types of people who use VPNs and why:
- General Users: Using a VPN helps enhance privacy and hide online activity. These benefits are especially helpful when using public Wi-Fi networks, ensuring that data while in transit is encrypted.
- Businesses: Using a VPN offers businesses secure remote access for employees, helping to protect company data when employees are accessing networks remotely.
- Journalists, activists, and whistleblowers: Using a VPN helps ensure anonymity when accessing and sharing sensitive information online.
- Travelers: Using a VPN gives people a secure connection to access content when traveling, and it protects web traffic when using public Wi-Fi.
- Students: Using a VPN can help students access academic resources more easily.
- Gaming Enthusiasts: Using a VPN provides gamers access to global gaming servers and helps reduce the chances of an in-game interruption caused by a DDoS or other hacking attack.
People in different countries around the world can use a VPN to access content and social media platforms more freely. Beyond that, anyone can use a VPN to enhance their privacy when using public or airplane Wi-Fi , playing video games, browsing the dark web , working remotely, exchanging sensitive information online, or trying to avoid government surveillance.
4 types of VPNs (+ what they’re used for)
There are several types of virtual private networks—all with different strengths and weaknesses. Some work well for staying connected on your travels , and others enable remote employees to access a company’s internal resources securely. And that’s just the start.
Learn more about the best VPNs, their architecture and protocols, and when you should use them.
| Protocol(s) | OpenVPN, WireGuard, L2TP/IPsec, PPTP, and SSTP | SSL/TLS | IPsec | SSL/TLS |
| Architecture | Client-server | Client-server | Gateway-to-gateway or router-to-router | Web-based |
| Use case | Encrypt internet traffic and mask IP addresses | Secure communication between multiple office locations | Secure access to a company’s internal network | Secure access to web-based applications and browsers |
Personal VPN
A personal VPN service allows everyday users to secure their internet connection at home and out in the world. These are the traditional VPNs you’re probably familiar with that mask your IP address and encrypt data you send and receive online to guard against cyber snoopers.
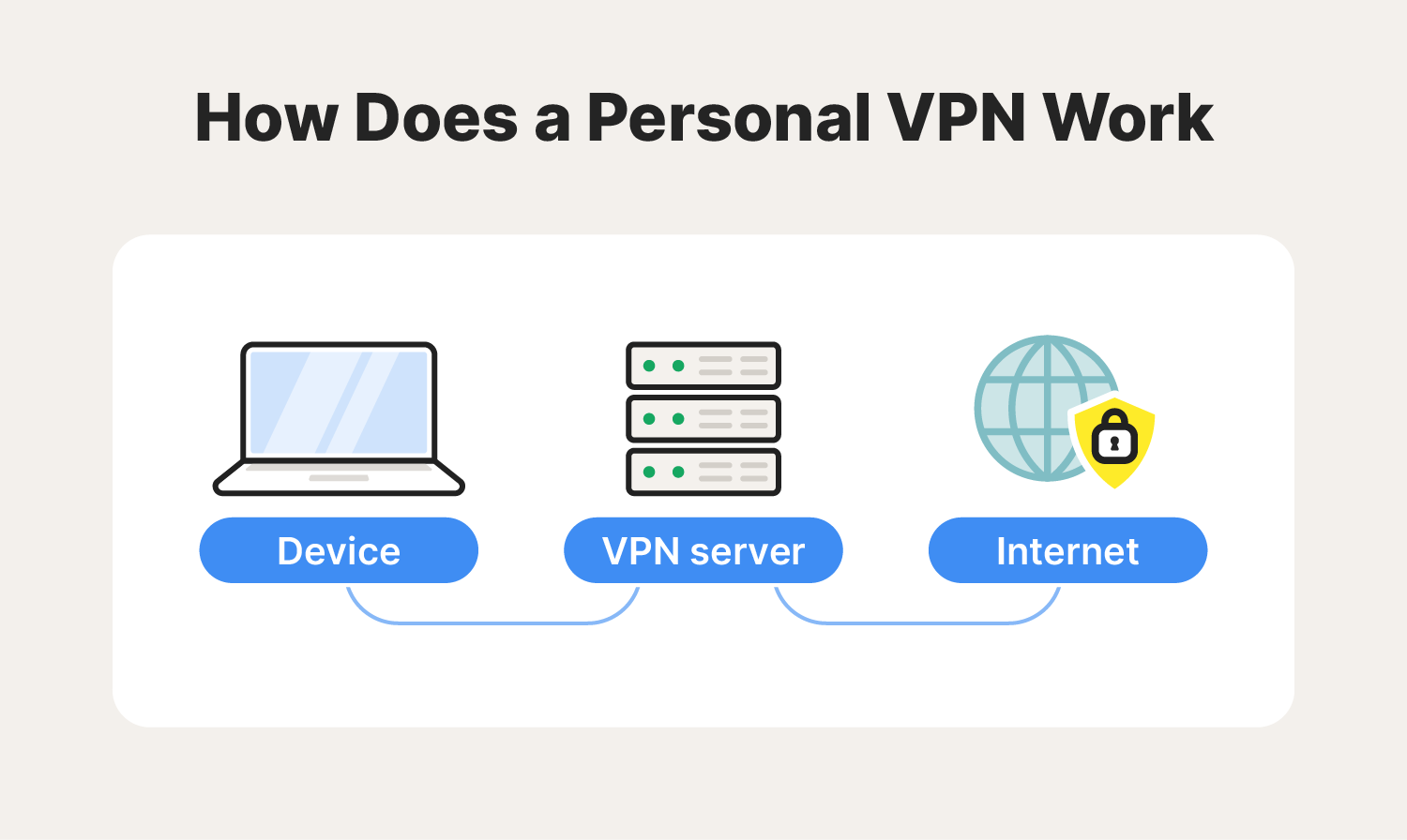
- Most common protocol(s): OpenVPN, WireGuard, L2TP (Layer2 Tunneling Protocol), PPTP (Point-to-Point Tunneling Protocol), and SSTP (Secure Socket Tunneling Protocol)
- Architecture: Client-server
- Used for: Individual privacy, encrypting internet traffic, and masking IP address
Remote access VPN
Remote access VPNs empower users to connect to private networks from different countries around the world, making them valuable to hybrid and work-from-home (WFH) employees. You can use this type of VPN to remotely access private resources, files, applications, data, and more securely.
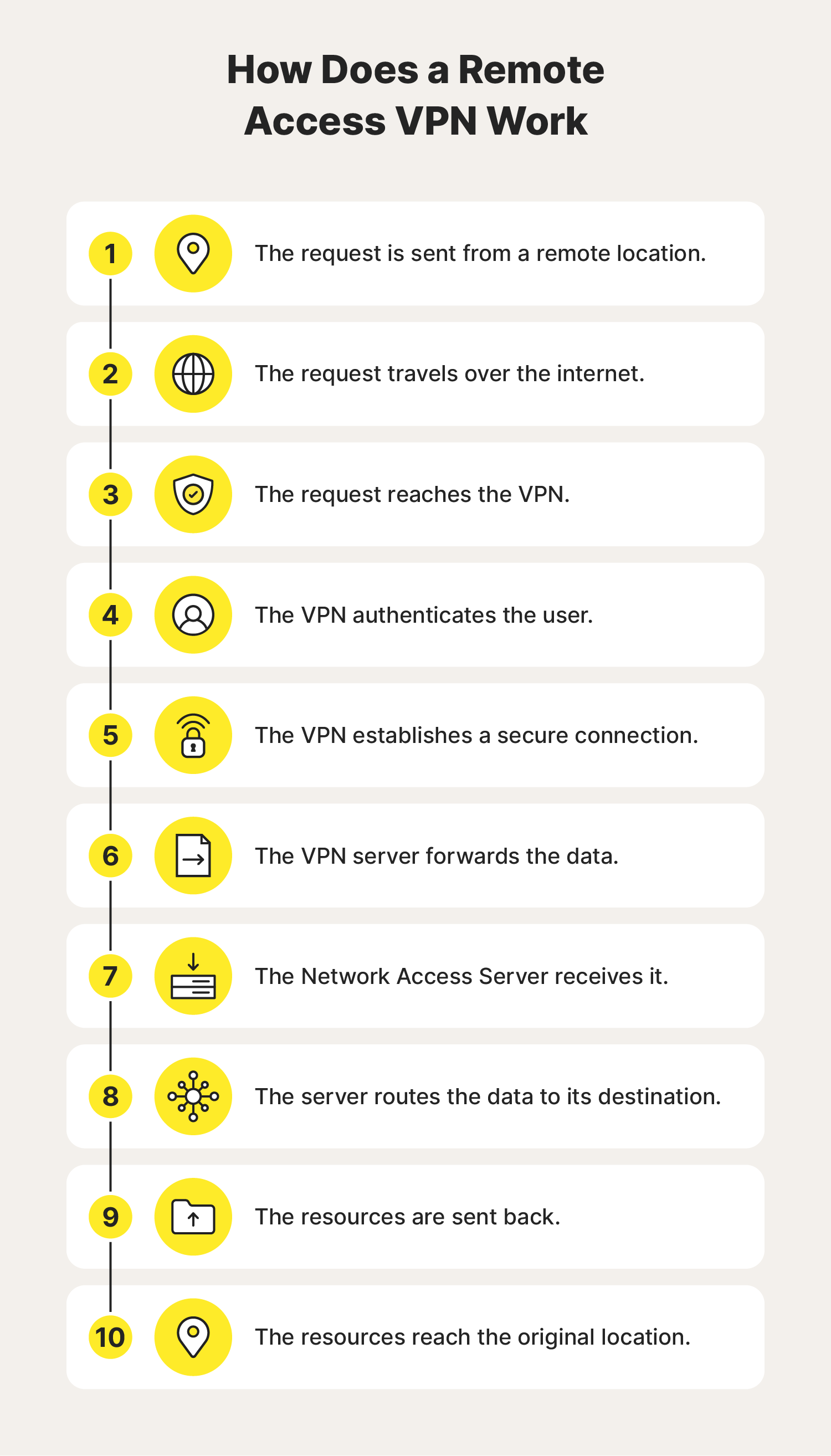
- Most common protocol(s): SSL/TLS (Secure Sockets Layer Transport Layer Security)
- Used for: Secure communication between networks and connecting multiple office locations
Site-to-site VPN
Site-to-site VPNs enable workers to communicate and collaborate securely with people at geographically separated business branches. This is a common way for businesses to maintain a unified and private network as they expand and add more brick-and-mortar locations.
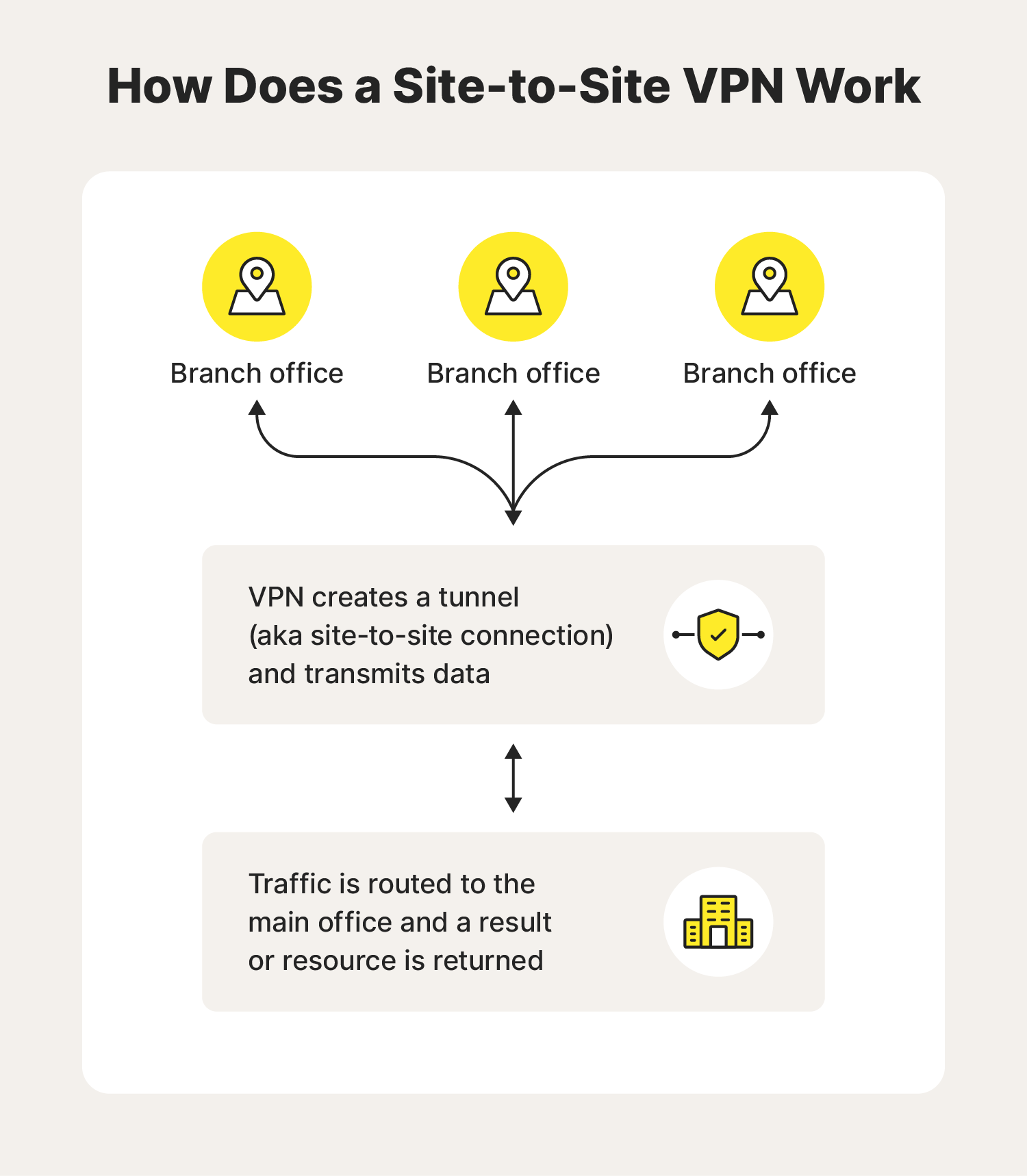
- Most common protocol(s): IPsec (Internet Protocol Security)
- Architecture: Gateway-to-gateway or router-to-router
- Used for: Secure access to a company’s internal network for remote employees and users
An SSL VPN (Secure Sockets Layer VPN) enables users to securely access web-based applications like file-sharing services and internal directories. Ultimately, this helps people protect their calendars, emails, and documents from prying eyes.
- Architecture: Web-based
- Used for: Enabling secure access to web-based applications and browsers
How to choose a VPN
Choosing a VPN depends on your (or your organization’s) unique privacy needs. Some factors to consider are server locations, provider log policies, subscription costs, architecture, protocols, and kill switch capabilities. Here’s a closer look at the factors you should consider when looking for a VPN:
- Architecture: Choose the VPN network structure based on whether you intend to use the VPN for personal or business reasons or content access.
- Servers: Consider the quantity and locations of a VPN’s servers since this can impact connection speed, performance, and your ability to access content freely.
- Log policy: Find a VPN service with a no-log policy to help ensure your provider doesn’t store your activity data and possibly misuse or compromise sensitive information.
- Cost : Consider all associated fees and read reviews to find a VPN with the right cost-to-quality ratio.
- Protocol: Choose a VPN that follows the set of rules and procedures for data encryption that you need without sacrificing device compatibility or security features.
- Kill switch: Pick a VPN solution with a kill switch to help prevent potential data leaks and ensure security continuity.
Protect your digital privacy with a VPN
Connect with Norton Secure VPN to enhance your online privacy, obscure your location, and help access the content you love. Plus, Norton’s VPN has a no-log policy, meaning we don’t track or store your online activities. Gen on-the-go access and more anonymous browsing today.
FAQs about VPNs
Still have questions about VPNs? Here’s what you need to know.
What does a VPN protect you from?
A VPN can help protect you from eavesdropping on public Wi-Fi , identity theft , government surveillance, account takeovers, and unauthorized access to sensitive accounts.
Do VPNs make you anonymous?
VPNs help enhance your anonymity but can’t make you 100% untraceable. For starters, your internet service provider can’t see your activity when you use a VPN, but it can see the VPN’s IP address . And if there’s a DNS leak (security vulnerabilities that happen when your DNS request isn’t adequately concealed), any queries you enter online can get sent to the ISP’s servers.
Should I leave my VPN on all the time?
It’s up to you. You should turn your VPN on whenever you connect to public Wi-Fi. Beyond that, it’s your decision if you want to leave your VPN on all the time for continuous online security coverage. Just note that constant VPN use can slow down your internet.
What is a VPN on a phone?
A VPN on an iPhone or an Android phone is a mobile application that encrypts internet traffic, masks the device's IP address, and provides more secure and private online browsing through a virtual private network.
What is a VPN number?
A VPN number is a set of identifying numbers that maintain the VPN tunnel encryption and reroute traffic anonymously. Typically, a VPN number can refer to the following three possibilities:
- A specific server ID identification number that a VPN connection is associated with.
- A virtual phone number given by the VPN provider to the user.
- An internal IP address that is allocated to a mobile device when connected via VPN.
How do I install a VPN?
To install a VPN, download your provider’s VPN application, launch it, and log in. From there, you can connect to the server of your choice to secure your internet connection. If you have any issues, check to make sure your VPN is working properly.
- Luis Corrons
Editorial note: Our articles provide educational information for you. Our offerings may not cover or protect against every type of crime, fraud, or threat we write about. Our goal is to increase awareness about Cyber Safety. Please review complete Terms during enrollment or setup. Remember that no one can prevent all identity theft or cybercrime, and that LifeLock does not monitor all transactions at all businesses. The Norton and LifeLock brands are part of Gen Digital Inc.
Related articles

Follow us for all the latest news, tips and updates.
- Norton AntiVirus Plus
- Norton 360 Deluxe
- Norton 360 for Gamers
- Norton 360 with LifeLock Select
- Norton 360 with LifeLock Ultimate Plus
- Norton Ultra VPN
- Norton AntiTrack
- Norton Family
- Norton Mobile Security for Android
- Norton Mobile Security for iOS
- Norton Utilities Ultimate
- Norton Driver Updater
- Norton Small Business
- Norton Genie
- Norton Private Browser
Product features
- Norton 360 Comparison
- Windows 10 Antivirus
- Windows 11 Antivirus
- Mac Antivirus
- Virus removal
- Malware protection
- Cloud Backup
- Safe Search
- Windows 10 VPN
- Smart Firewall
- Password Manager
- Parental Control
- Privacy Monitor
- Dark Web Monitoring
- Identity Lock
Services & Support
- Norton Premium Services
- Norton Computer Tune Up
- Norton Ultimate Help Desk
- Spyware & Virus Removal
- Norton Device Care
- Norton Support
- Norton Update Center
- How to renew
- About Norton
- Free trials
- Partner with us
- LifeLock by Norton
- ReputationDefender by Norton
- Get Started
Home » Blog » Network Engineering
What is a VPN? An Introduction to Virtual Private Networks
How does a Virtual Private Network work? What are the different types of VPN? What are the advantages and disadvantages? Continue reading to learn all about this.

Whether you’re growing a company, streaming your favorite shows or simply trying to keep your data safe online, there’s a good chance you’d benefit from using a virtual private network ( VPN ) service.
A virtual private network is a service that provides you with a secure and private internet connection wherever you are in the world. A VPN creates an encrypted tunnel to keep your data safe, hides your IP address to facilitate anonymous browsing and allows you to remotely access your organization’s network.
VPNs have many applications, from companies scaling their networks to individual users implementing security while connected to public Wi-Fi hotspots.
In this article, we introduce what VPN is and how it works. We also explain some of the more important uses and weigh the advantages and disadvantages of using a VPN.
How does a VPN work?
Without a VPN, when you’re browsing the internet, your requests are received by your internet service provider (ISP), who then returns the data you need. For example, by loading a website.
When you use a VPN, things are a little more complicated. Instead of your ISP directing your internet traffic directly to your destination, the traffic first moves through a VPN server.
From your point of view, your public IP address changes to that of the VPN server, and your data is encrypted. However, there’s more going on:
- When connecting to a VPN service, the server authenticates your client .
- An encryption protocol is applied to make all data you send and receive private.
- A secure VPN tunnel is created to transmit data between you and the desired destination.
- Data packets are wrapped in an outer packet by the VPN to ensure a safe transfer .
- The outer packet is decrypted once it arrives at its intended destination.
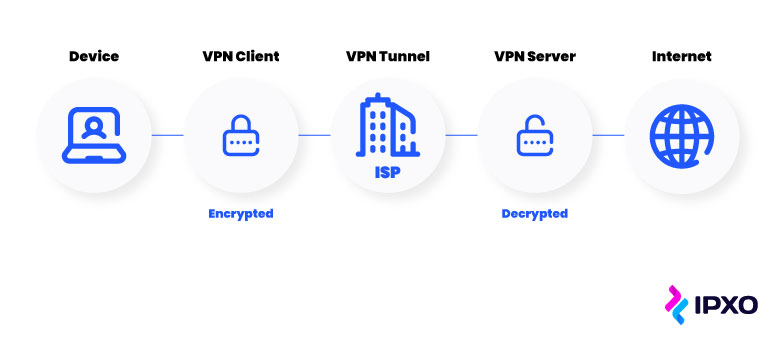
Types of VPN
While we generally just use the term VPN, there are two different kinds of VPN – remote access and site-to-site access – used on the internet, each with a unique purpose and characteristics.
Remote access
Most of the time, when people refer to VPN, they are talking about a remote access VPN . This kind of VPN is designed to allow users to remotely connect to a computer network securely.
A remote access VPN allows employees to connect to their office network and access files or applications stored in the organization’s servers from anywhere in the world.
For private VPN users, this kind of VPN access generally gives them access to servers operated by their VPN service provider, which allows them to hide their IP address, change their location and browse more securely.
You might also know this version as a virtual private dial-up network (VPDN).
Site-to-site access
A site-to-site VPN is designed for multiple fixed locations to share a single private network.
For example, offices run by the same organization can set up a secure connection over the internet, so that their internal network behaves as if it were one local network. This allows everyone within the organization to access digital resources stored at any location.
This is the less commonly known kind of VPN, especially because it tends to be corporate rather than private. Nevertheless, it is widely used.
VPN encryption explained
One of the biggest appeals of using a VPN is that your data is encrypted and thus safe from the prying eyes of hackers. But how, exactly, does an encrypted VPN connection work?
We briefly mentioned the concept of a VPN tunnel before. While different VPN providers offer different data encryption, the idea of the tunnel and the basics of encryption are relatively universal.
You need to download a VPN app on your computer or mobile device to use the service. This means that the VPN provider has software at both ends of the tunnel – on the server and your device.
When your device requests data, the server fetches the unencrypted data from the internet. However, before relaying it to your device, the server wraps the packet of data in a special layer of encryption.
When the packet reaches your device, the VPN app on your device has the correct key to decrypt the layer of encryption around the packet. Even if the packet was intercepted between the server and your device, without the correct decryption key, it would look like a meaningless string of letters and numbers.
What does VPN secure?
Because VPN protocols create a secure tunnel between the VPN server and your device, a VPN helps keep you secure online in the following ways:
- Encrypts data sent and received by your device, keeping it safe from third parties
- Hides your internet activity from internet service providers, government agencies and hackers
- Hides your IP address , which could be used to compromise your device
- Conceals your real geographical location
- Creates a secure connection on shared or public Wi-Fi networks
Be mindful, however, that even the most reliable VPN provider can’t promise you complete online anonymity and security.

Generally, VPNs aren’t effective against cookies, which companies can use to track your browsing history. And remember, if you’re using a free or cheap VPN, the VPN provider might be collecting data on you themselves.
Moreover, if someone targets you specifically, they could get around your VPN by planting malware on your device or even use traffic patterns from the VPN server to track your traffic.
Undoubtedly, understanding the shortcomings of a VPN can help you figure out which other security steps to take.
Should you use VPN?
A secure connection and private internet access may sound like something you’d want all the time, but VPN protocols aren’t suitable for all users all of the time. Whether you choose to use a VPN depends entirely on your needs.
For instance, if you want to change your IP geolocation , or you’re worried about your personal data privacy on public Wi-Fi networks, using a VPN is a great idea. But you should understand that, as with pretty much every kind of service, there are also some drawbacks to running your internet traffic through a VPN.
To understand whether a VPN service is right for you, you must weigh the advantages and disadvantages of using it.
Advantages of VPN
Before we introduce you to the drawbacks of using your own VPN, let’s explore some of the wonderful and extremely helpful reasons why a virtual private network might be right for you.
This is not a complete list of advantages; however, these are among the top reasons people use VPN software:
Network security
Private data protection
Network expansion
Access to geo-blocked services
Network security is important for everyone, from the most humble social media scroller to huge companies with thousands of connected devices.
For example, websites and web apps tracking your activity while using the internet may pose a risk. At best, your internet data can be harvested by advertisers to personalize ads. At worst, an insecure network could threaten your organization’s security.
To avoid annoying pop-ups or, more importantly, security incidents, you can connect to the internet via a VPN server. Because the VPN encrypts your traffic, you gain a secure connection that, hopefully, no one else can snoop on.
The obvious next question is: why do I need a secure connection? Surely, unless you’re running a company or doing something illegal, there’s no reason to hide your internet connection from everyone else? Unfortunately, we live in a world where hackers are out to gain access to your personal information while you surf the internet.
Think about the online banking, credit card, login credentials and other private details you use online every day. Without an encrypted connection securing your online data, all this personal information is at risk. However, if you use a VPN connection, it hides IP addresses from bad actors and protects all your communication online.
The vast majority of companies and organizations use a private network in their offices and official buildings. This ensures that the network traffic of employees and associates is secure and allows access to specialized virtual workspaces and applications.
However, the problem with running a local network like this is scalability. The cost of growing a network is beyond the budget of many organizations. A virtual private network can save the day. Using a corporate VPN server allows anyone with the correct credentials to access the network remotely, provided they have an internet connection.
This kind of remote access VPN keeps all traffic on the same secure network and provides an encrypted tunnel for employees to access applications not available on their own machines. This could be anything from company emails to payroll systems that need to be handled with the utmost sensitivity.
Have you ever gone on holiday only to discover your favorite show is no longer on Netflix? Or perhaps you happen to know that flight tickets are cheaper if you buy them from a different country?
While the internet feels free and global, online services use your IP address to determine where you are in the world geographically. They then use that information to show or hide geo-specific content or services.
You’ve probably guessed by now that this is another way in which VPN servers can come in handy. Your VPN connection can use an IP address associated with an entirely different location, so you can choose where in the world you want to be seen accessing the internet from.
This leaves you free to access all the content and services you need.
Disadvantages of VPN
A VPN protects your data, encrypts your connection and gives you access to more content and services. It’s a win-win situation, right? Well, unfortunately, it’s not.
As with all things in life, there are some drawbacks to using VPNs online. Here are some of the most compelling reasons not to use a VPN connection all the time:
Decreased internet speed
Blocked VPN connections
VPN disadvantages
The elephant in the room is that using a VPN service has speed issues associated with it. Because a VPN works by rerouting and encrypting your internet connection, it can slow it down.
That said, for the average user with average internet traffic, VPN-related connection slowdowns will be negligible. In most cases, users might not even notice it. Moreover, premium VPN services slow traffic down minimally.
However, suppose you’re streaming, gaming or doing some other kind of bandwidth-intensive activity online. In that case, you may find that your VPN restricts speeds to the point where it can become inconvenient and annoying.
This is the biggest complaint that many VPN providers receive from their customers.
A good VPN offers freedom and security; however, not every service provider is a fan.
For example, take big streaming platforms like Netflix , Hulu or HBO . VPN users utilize their VPN client software to access geo-blocked content on these platforms, and the companies know it.
Streaming platforms are incentivized to block VPN internet traffic to protect their licensing and intellectual property. While the best premium VPNs will usually allow you to access these services from another location, the majority of cheap and free ones are now blocked.
VPNs also disable ISP tracking, which stops your internet service provider from collecting data about your online activities. That said, your internet provider can see when you’re using a VPN.
And it’s not just private companies that are unhappy with VPN providers. Believe it or not, some countries have made using VPN illegal , while others have taken steps to restrict the use.
This kind of internet censorship isn’t an issue unless you plan to use a VPN client somewhere like Belarus, China or Iraq. However, it’s worth remembering that the online identity protection and security offered by the technology are not available to all.
Premium VPN services are premium because they can cost a fair amount of money. You can get a decent VPN for personal use for a few dollars per month, but if you’re running a business, a VPN subscription for all your employees can start to run up to a significant amount of money.
Naturally, the more you’re willing to spend on VPN services, the better, more dependable, faster and more secure they are going to be. Sure, free VPNs exist, but you need to ask yourself why anyone would give you anything for free. Perhaps, the free VPN service you’ve chosen either doesn’t work or poses a security risk?
Due to data collection, advertisements and download restrictions, you might find that using cheap or free VPNs is worse than not using them at all.
A VPN allows a user to connect securely to a remote computer network. Most commonly, it is used by companies to enable employees to access company servers remotely. Individual internet users often use VPNs to increase their security while using the internet or to bypass restrictions.
A VPN encrypts data that your computer sends and receives, and it also hides your IP address. This can help you browse privately, enhance the security of your personal data and enable you to access services and content not available in your physical location.
Although VPNs have some downsides – most notably, the decreased traffic speeds – using a VPN is advantageous in many ways and can offer security that outweighs any drawbacks.
About the author

Beatričė Raščiūtė
Technical Content Writer
Please leave this field empty.
I agree with IPXO's Privacy Policy
Table of contents
Related reading.

Email Service Provider: What You Should Know About ESPs in 2024
Discover the differences between email service providers and webmail clients. Learn the importance of ESPs for successful email marketing campaigns in 2024.

A Comprehensive Guide to Network Routing
What is networking and how does it work? What is a routing table and the main routing protocols? We've got the answers.

What is a PPTP VPN and why it’s the wrong choice
Point-to-Point Tunneling Protocol (PPTP) is one of many remote network connection implementation methods for VPNs . A PPTP VPN receives data, encrypts it, and transmits it over the internet. Easy to set up, PPTP is one of the oldest VPN protocols used by more advanced users in very niche cases. Then again, due to its age, PPTP encryption is terrible at fulfilling its essential security function – protecting user information. But let’s elaborate on that.
Table of contents
How a pptp vpn works.
At a glance, PPTP carries out the same basic operations as most other VPN protocols – authentication, tunnel establishment , data encryption/encapsulation, and transportation.
Simply put, PPTP security is creating a tunnel between two points, usually the user’s device and a remote network. It’s all done using a set of predetermined rules and procedures called a protocol.
This link is then used to transfer encrypted information back and forth between the two points, which in theory should make a safe VPN connection. However, PPTP VPN’s authentication and encryption methods are extremely outdated and have severe security flaws.
Why a PPTP connection is considered obsolete

PPTP is a direct predecessor of PPP, an even older Point-to-Point Protocol, and is built on its outdated framework. It can use three authentication protocols, two out of which (PAP and CHAP) are known to have been breached and exploited before, and only supports MPPE (Microsoft Point-to-Point Encryption) encryption keys of up to 128 bits.
128-bit keys are usually not that easy to crack, but MPPE is infamous for being extra vulnerable to bit-flipping attacks. In fact, the NSA was allegedly able to crack and bypass it , which allowed them to monitor PPTP users’ online activity.
Aside from its lack of security, the protocol also struggles to bypass firewalls and can have compatibility issues with routers.
A PPTP VPN benefits
Ironically, however, PPTP’s downfalls are also its only saving grace – bad encryption means small overhead, which directly increases speed. So because of its abysmal security, a PPTP VPN remains, by a small margin , one of the faster VPN protocols to date.
It is also easy to set up, which, when paired with its speed, might make it seem like a viable VPN protocol.
PPTP in a nutshell:

What is PPTP Passthrough?
PPTP Passthrough is a router feature that allows PPTP to bypass router restrictions by adding a unique call ID, which acts as a substitute for NAT ( Network Address Translation ) ports.
Most routers connect to the internet using the NAT protocol, which requires ports to function properly, making PPTP incompatible with NAT.
However, the Passthrough feature is only required for ancient routers and outdated VPN protocols like PPTP. Its newer and more secure counterparts like OpenVPN, IKEv2, and WireGuard VPN connections come pre-equipped to deal with NAT if necessary – or you can just set up a VPN on a router .
How does a PPTP connection fare against other protocols?
As mentioned previously, PPTP’s authentication and encryption methods are insecure and outdated – but is it really that bad? Spoiler alert – it is, especially when you compare it to other, more up-to-date protocols.
With that in mind, let’s look at the top three most widely used VPN protocols and how a PPTP VPN connection fares against them.
PPTP vs. IKEv2
Compared to a PPTP VPN connection, IKEv2 is a much safer and more reliable choice. It’s compatible with the industry-standard AES 256-bit cipher the US government and the NSA use to protect sensitive information.
This makes the IKEv2 naturally slower, but the difference in speed is negligible.
The IKEv2 VPN protocol is also better at switching and establishing connections from data to Wi-Fi, making it popular among mobile users.
PPTP vs. OpenVPN
Like IKEv2, OpenVPN has PPTP beat on every level of security but is slower because of it.
However, unlike IKEv2, OpenVPN is faster and more stable over long-distance connections, so the two are often used interchangeably by many VPN providers. The combination of both offers a well-rounded VPN service – not as fast as PPTP, but preferable on every other level.
OpenVPN is an open-source project under constant development, which keeps it transparent, easy to audit, and consistently improving.
PPTP vs. WireGuard
WireGuard is the newest open-source addition to the VPN protocol family and comes as separate standalone software.
It was developed on Linux Kernel and only has 4,000 lines of code compared to OpenVPN and IKEv2 codebases that are in the hundreds of thousands.
Because of this, WireGuard can establish faster and more stable connections while providing top-tier security.
Suffice to say, it would be unfair to compare it to PPTP because WireGuard is essentially superior on every level.
Bottom line: It’s all about security
PPTP VPN is fast and easy to set up, but it’s not worth compromising your security. To be blunt, I cannot recommend PPTP as a protocol as there are better alternatives like IKEv2, OpenVPN, and WireGuard. All are more secure, some just as fast, and all available on Surfshark!

What is a PPTP VPN server?
Essentially, there’s no such thing as a PPTP VPN server. Terms like “PPTP server” or “PPTP VPN server” usually refer to a function to set up a PPTP protocol connection on a router.
How does a PPTP VPN work?
A PPTP VPN works by establishing a connection through a VPN application using PPTP. Most VPN providers offer PPTP as one of their available protocols.
Why is PPTP not secure?
Its encryption framework ( read: security) is obsolete. PPTP and its several authentication methods were known to be exploited by agencies like the NSA.
Should I use a PPTP VPN protocol?
No. Protocols like IKEv2, OpenVPN, and WireGuard are much safer and sometimes just as fast as PPTP VPN connections.
Which is better: OpenVPN or PPTP?
OpenVPN. It offers higher levels of security and encryption standards while also being fast (although not quite as fast as PPTP).
Rate and share this article
Hand picked related articles

How to block ads on Android, iOS, and other platforms

What are the best DNS servers for gaming?

iCloud Private Relay vs. VPN: which is better for your online privacy?
Your comment is awaiting moderation.
Grab this exclusive Surfshark deal:

IMAGES
VIDEO
COMMENTS
A VPN presentation explains how a VPN (Virtual Private Network) permits safe communication over a public network, and it uses tunnelling protocols and encryption to shield users. As a result, a user's browsing activities, location, and identity remain under wraps, and the person can enjoy their anonymity and greater privacy. ...
VPN is a mechanism of employing encryption, authentication, and integrity protection so that we can use a public network as if it is a private network. It offers a high amount of security and allows users to remotely access private networks. In this article, we will cover every point about virtual private networks.
A VPN protects your data using encryption and tunneling. It also requires authentication at both sides of the tunnel. Encryption: Encryption in simple words, as you may know, is the act of scrambling data so that only the intended recipient can view or understand what you have sent and that it looks worthless and gibberish to other parties who may happen to view it.
VPN Connection in XP. Summary • A virtual private network (VPN) is a network that uses public means of transmission (Internet) as its WAN link, connecting clients who are geographically separated through secure tunneling methods • Main VPN protocols include PPTP, L2TP, and IPsec • VPN Tunneling supports two types: voluntary tunneling and ...
Slide 1: The slide introduces Virtual Private Network (VPN).State Your Company Name. Slide 2: This is an Agenda slide.State your agendas here. Slide 3: The slide displays Table of contents for the presentation. Slide 4: The slide continues Title of contents. Slide 5: This slide discusses the overview of virtual private network used for secure transfer of data through tunnelling protocols.
A VPN is A network that uses Internet or other network service to transmit data. A VPN includes authentication and encryption to protect data integrity and confidentiality. 4 Types of VPNs Remote Access VPN. Provides access to internal corporate network over the Internet. Reduces long distance, modem bank, and technical support costs.
VPNs use virtual connections to create a private network, keeping any device you connect to a public wi-fi safe from hackers and malware, and protecting sensitive information from unauthorized viewing or interception. A VPN routes your device's connection through a private server rather than the ISP, so that when your data reaches the ...
A VPN will hide the contents of your web traffic from some observers and can make it harder for you to be tracked online. But a VPN can, at best, provide only limited protection against the ...
This document summarizes a seminar presentation on virtual private networks (VPN). It defines a VPN as using public networks like the Internet to connect private networks securely through virtual tunnels. There are three main types of VPNs: remote-access VPNs for individual users, intranet site-to-site VPNs connecting company locations, and extranet site-to-site VPNs for partner organizations ...
Virtual private network (VPN) is a network architecture for virtually extending a private network (i.e. any computer network which is not the public Internet) across one or multiple other networks which are either untrusted (as they are not controlled by the entity aiming to implement the VPN) or need to be isolated (thus making the lower network invisible or not directly usable).
VPNs can be used to bypass geographic restrictions, shield your activity on public Wi-Fi, and hide your real IP address when browsing and using software like BitTorrent. A VPN, or Virtual Private Network, allows you to create a secure connection to another network over the Internet. VPNs can be used to access region-restricted websites, shield ...
VPN Presentation Slide. Did you know that there are over 400 million active VPN users worldwide? VPN, or Virtual Private Network, is a powerful tool that can provide a secure and private connection to the internet. By encrypting your online activity, VPNs can protect your sensitive data from hackers, surveillance, and censorship. With this VPN ...
A VPN gateway/concentrator acts as the endpoint of a VPN tunnel, especially in a remote access VPN or CE-based site-to-site VPN. See Figure 1-5 later in the chapter for an illustration of the role performed by a VPN gateway/concentrator. Depending on the remote access VPN protocol in use, the VPN gateway/concentrator may,
VPN stands for virtual private network—it's technology that encrypts your data when you use the internet, scrambling it so that strangers on the same network can't read it. A VPN creates a secure tunnel between your device and the internet to protect data during transmission. This secure tunnel helps VPNs disguise your IP address, mask ...
A VPN creates an encrypted tunnel to keep your data safe, hides your IP address to facilitate anonymous browsing and allows you to remotely access your organization's network. VPNs have many applications, from companies scaling their networks to individual users implementing security while connected to public Wi-Fi hotspots.
Dialup usage low, Internet used as primary access at home and on the road. Broadband at home. ~16,000 global employees using Cisco Virtual Office. Global, secure, scalable IP VPN connectivity over Internet. Average user gains 2.75 productive work hours per week from reduced commuting time. Secure and simplified access for PDA devices.
2022, August 16 · 9 min read. Point-to-Point Tunneling Protocol (PPTP) is one of many remote network connection implementation methods for VPNs. A PPTP VPN receives data, encrypts it, and transmits it over the internet. Easy to set up, PPTP is one of the oldest VPN protocols used by more advanced users in very niche cases.