Criminal Justice Sciences
- Recommended Databases
- Recommended Journals
- Recommended Books
- Reference Resources
- Open and Accessible Materials
- Faculty Resources
- Statistical Sources
- Law Enforcement Exam Practice Materials
- Use Criminal Justice Abstracts
- Use Nexis Uni
- Use HeinOnline
- Navigate Westlaw
- Evaluate Articles
- Find CJS textbooks
- Source Management Tools
- Annotated Bibliography
- Literature Review
- Useful Links

What's on this Page
This page is meant to help you create a literature review for academic projects and publications. Each tab outlines a different aspect of what a literature review is and how to build one. If you need help finding sources for your literature reviews, check out How To pages.
How to Build a Literature Review
- What is a Lit Review?
- Why Write a Lit Review?
- Building a Lit Review
- Prepping for a Lit Review
- Basic Example
- Other Resources/Examples
What is a Literature Review?
A literature review is a comprehensive summary and analysis of previously published research on a particular topic. Literature reviews should give the reader an overview of the important theories and themes that have previously been discussed on the topic, as well as any important researchers who have contributed to the discourse. This review should connect the established conclusions to the hypothesis being presented in the rest of the paper.
What a Literature Review Is Not:
- Annotated Bibliography: An annotated bibliography summarizes and assesses each resource individually and separately. A literature review explores the connections between different articles to illustrate important themes/theories/research trends within a larger research area.
- Timeline: While a literature review can be organized chronologically, they are not simple timelines of previous events. They should not be a list of any kind. Individual examples or events should be combined to illustrate larger ideas or concepts.
- Argumentative Paper: Literature reviews are not meant to be making an argument. They are explorations of a concept to give the audience an understanding of what has already been written and researched about an idea. As many perspectives as possible should be included in a literature review in order to give the reader as comprehensive understanding of a topic as possible.
Why Write a Literature Review?
After reading the literature review, the reader should have a basic understanding of the topic. A reader should be able to come into your paper without really knowing anything about an idea, and after reading the literature, feel more confident about the important points.
A literature review should also help the reader understand the focus the rest of the paper will take within the larger topic. If the reader knows what has already been studied, they will be better prepared for the novel argument that is about to be made.
A literature review should help the reader understand the important history, themes, events, and ideas about a particular topic. Connections between ideas/themes should also explored. Part of the importance of a literature review is to prove to experts who do read your paper that you are knowledgeable enough to contribute to the academic discussion. You have to have done your homework.
A literature review should also identify the gaps in research to show the reader what hasn't yet been explored. Your thesis should ideally address one of the gaps identified in the research. Scholarly articles are meant to push academic conversations forward with new ideas and arguments. Before knowing where the gaps are in a topic, you need to have read what others have written.
What does a literature review look like?
As mentioned in other tabs, literature reviews should discuss the big ideas that make up a topic. Each literature review should be broken up into different subtopics. Each subtopic should use groups of articles as evidence to support the ideas. There are several different ways of organizing a literature review. It will depend on the patterns one sees in the groups of articles as to which strategy should be used. Here are a few examples of how to organize your review:
Chronological
If there are clear trends that change over time, a chronological approach could be used to organize a literature review. For example, one might argue that in the 1970s, the predominant theories and themes argued something. However, in the 1980s, the theories evolved to something else. Then, in the 1990s, theories evolved further. Each decade is a subtopic, and articles should be used as examples.
Themes/Theories
There may also be clear distinctions between schools of thought within a topic, a theoretical breakdown may be most appropriate. Each theory could be a subtopic, and articles supporting the theme should be included as evidence for each one.
If researchers mainly differ in the way they went about conducting research, literature reviews can be organized by methodology. Each type of method could be a subtopic, and articles using the method should be included as evidence for each one.
Preliminary Steps for Literature Review
- Define your research question
- Compile a list of initial keywords to use for searching based on question
- Search for literature that discusses the topics surrounding your research question
- Assess and organize your literature into logical groups
- Identify gaps in research and conduct secondary searches (if necessary)
- Reassess and reorganize literature again (if necessary)
- Write review
Here is an example of a literature review, taken from the beginning of a research article. You can find other examples within most scholarly research articles. The majority of published scholarship includes a literature review section, and you can use those to become more familiar with these reviews.
Source: Perceptions of the Police by LGBT Communities

- ISU Writing Assistance The Julia N. Visor Academic Center provides one-on-one writing assistance for any course or need. By focusing on the writing process instead of merely on grammar and editing, we are committed to making you a better writer.
- University of Toronto: The Literature Review Written by Dena Taylor, Health Sciences Writing Centre
- Purdue OWL - Writing a Lit Review Goes over the basic steps
- UW Madison Writing Center - Review of Literature A description of what each piece of a literature review should entail.
- USC Libraries - Literature Reviews Offers detailed guidance on how to develop, organize, and write a college-level research paper in the social and behavioral sciences.
- Creating the literature review: integrating research questions and arguments Blog post with very helpful overview for how to organize and build/integrate arguments in a literature review
- Understanding, Selecting, and Integrating a Theoretical Framework in Dissertation Research: Creating the Blueprint for Your “House” Article focusing on constructing a literature review for a dissertation. Still very relevant for literature reviews in other types of content.
A note that many of these examples will be far longer and in-depth than what's required for your assignment. However, they will give you an idea of the general structure and components of a literature review. Additionally, most scholarly articles will include a literature review section. Looking over the articles you have been assigned in classes will also help you.
- Sample Literature Review (Univ. of Florida) This guide will provide research and writing tips to help students complete a literature review assignment.
- Sociology Literature Review (Univ. of Hawaii) Written in ASA citation style - don't follow this format.
- Sample Lit Review - Univ. of Vermont Includes an example with tips in the footnotes.
- << Previous: Annotated Bibliography
- Next: Useful Links >>
- Last Updated: Aug 22, 2024 12:38 PM
- URL: https://guides.library.illinoisstate.edu/cjs
Additional Links
- Directions and Parking
- Accessibility Services
- Library Spaces
- Staff Directory
Thank you for visiting nature.com. You are using a browser version with limited support for CSS. To obtain the best experience, we recommend you use a more up to date browser (or turn off compatibility mode in Internet Explorer). In the meantime, to ensure continued support, we are displaying the site without styles and JavaScript.
- View all journals
- Explore content
- About the journal
- Publish with us
- Sign up for alerts
- Open access
- Published: 21 January 2021
Why do inequality and deprivation produce high crime and low trust?
- Benoît De Courson 1 , 2 &
- Daniel Nettle 2
Scientific Reports volume 11 , Article number: 1937 ( 2021 ) Cite this article
65k Accesses
26 Citations
371 Altmetric
Metrics details
- Human behaviour
Humans sometimes cooperate to mutual advantage, and sometimes exploit one another. In industrialised societies, the prevalence of exploitation, in the form of crime, is related to the distribution of economic resources: more unequal societies tend to have higher crime, as well as lower social trust. We created a model of cooperation and exploitation to explore why this should be. Distinctively, our model features a desperation threshold, a level of resources below which it is extremely damaging to fall. Agents do not belong to fixed types, but condition their behaviour on their current resource level and the behaviour in the population around them. We show that the optimal action for individuals who are close to the desperation threshold is to exploit others. This remains true even in the presence of severe and probable punishment for exploitation, since successful exploitation is the quickest route out of desperation, whereas being punished does not make already desperate states much worse. Simulated populations with a sufficiently unequal distribution of resources rapidly evolve an equilibrium of low trust and zero cooperation: desperate individuals try to exploit, and non-desperate individuals avoid interaction altogether. Making the distribution of resources more equal or increasing social mobility is generally effective in producing a high cooperation, high trust equilibrium; increasing punishment severity is not.
Similar content being viewed by others
Inequality and cooperation in social networks

Segregating socioeconomic classes leads to an unequal redistribution of wealth
Social goods dilemmas in heterogeneous societies
Introduction.
Humans are often described as an unusually cooperative or ‘ultrasocial’ species 1 . The truth is more complex: humans from the same society can cooperate for mutual benefit; or they can simply co-exist; or they can actively exploit one another, as in, for example, crime. A theory of human sociality should ideally predict what mix of these alternatives will emerge under which circumstances. Comparing across industrialised societies, higher inequality—greater dispersion in the distribution of economic resources across individuals—is associated with higher crime and lower social trust 2 , 3 , 4 , 5 , 6 , 7 . These associations appear empirically robust, and meet epidemiological criteria for being considered causal 8 . However, the nature of the causal mechanisms is still debated. The effects of inequality are macroscopic phenomena, seen most clearly by comparing aggregates such as countries or states. It is their micro-foundations in individual psychology and behaviour that still require clarification.
There are, broadly, two classes of explanation for how inequality, a population-level phenomenon, could influence individual-level outcomes like crime or trust. The first class of explanation is compositional: in more unequal societies, the least fortunate individuals are absolutely worse off than in more equal societies of the same average wealth, exactly because the dispersion either side of the average is greater. Some individuals are also better off too, at the other end of the distribution, but if there is any non-linearity in the function relating individual resources to outcomes—if for example the poor becoming absolutely poorer has a larger effect on their propensity to offend than the rich becoming absolutely richer has on theirs—this can still change outcome prevalence in the population 9 , 10 , 11 . In line with compositional explanations, across US counties, the association between inequality and rate of property crime is fully mediated by the prevalence of poverty, which is higher in more unequal counties 2 . Moreover, changes in rates over time track changes in the economic prospects of people at the bottom end of the socioeconomic distribution 12 , 13 . The second class of explanation is psychosocial: individuals perceive the magnitude of social differentials in the society around them, and this affects their state of mind, increasing competitiveness, anxiety and self-serving individualism 8 , 14 . In this paper, we develop an explanatory model for why greater inequality should produce higher crime and lower social trust. Our model provides a bridge between compositional and psychosocial explanations. Its explanation for the inequality-crime association is compositional: individuals offend when their own absolute level of resources is desperately low, and the effect of increasing inequality is to make such desperation more prevalent. On the other hand, the model’s explanation for the inequality-trust association is more psychosocial: all individuals in high-inequality populations end up trusting less, regardless of their personal resource levels.
To provide a micro-foundation in individual behaviour for the macro-level effects of inequality on crime, we must start from explanations for why individuals commit crimes. Economic 15 , 16 and behavioural-ecological 17 approaches see offending as a strategic response to specific patterns of incentive. Economic models predict that offending should be more attractive when the payoffs from legitimate activity are low. This principle successfully explains variation in offending behaviour both within and between societies 12 , 16 . It can also explain the relationship between crime levels and inequality, in compositional manner, because unequal societies produce poorer legitimate opportunities for people at the lower end of the socioeconomic spectrum 2 . However, these models are generally taken to predict that making punishments for crime more severe should reduce the prevalence of offending, because harsher punishment should reduce the expected utility associated with the criminal option. Empirical evidence, though, does not clearly support the hypothesis that increasing punishment severity reduces offending 18 , 19 . There is more evidence for a deterrent effect of increased probability of punishment, though even this effect may be modest 18 , 19 .
Becker 15 pointed out that the puzzle of the weak deterrent effect of punishment severity would be solved if offenders were risk-preferring. The decision to offend is risky in that it has either a large positive payoff (if not caught) or a large negative one (if caught and punished). An individual who prefers risk might thus choose to offend even if the expected utility of offending is negative due to a possible severe punishment. Thus, the question becomes: why would some people—those who commit crime—prefer risk, when people are usually averse to it? To address this question, our model incorporates features of classic risk-sensitive foraging theory from behavioural ecology 20 (for a review in the context of human behaviour, see Ref. 21 ). Risk-sensitive foraging models incorporate a desperation threshold: a level of resources below which it is disastrous to fall, in the foraging case because of starvation. The models show that individuals in sufficient imminent danger of falling below this threshold ought to become risk-preferring. If a risky option is successful, it will allow them to leap back over the threshold; and if not, their prospects will be no more dire than they were anyway. Our model is novel in explicitly incorporating a desperation threshold into decisions about whether to cooperate (analogous in our model to participating in legitimate economic activity) or exploit others (analogous to committing an acquisitive crime).
The desperation threshold is the major theoretical innovation of our model. We justify its inclusion on multiple grounds. First, the ultimate currency in our model is fitness, a quantity with a natural biological interpretation that must necessarily be zero if the individual lacks the minimal resources to subsist and function socially. Thus, it is reasonable that expected fitness should be related to resource levels, but not linearly: there should be a point where, as resources deplete, expected fitness rapidly declines to zero. Our threshold assumption produces exactly this type of function (see Supplementary Sect. 2.1 , Supplementary Fig. S1 ). Second, in experimental games where gaining a payoff is subject to a threshold, people do switch to risk-proneness when in danger of falling below the threshold, as risk-sensitive foraging theory predicts 22 . Although this does not show that such thresholds are widespread or important in real life, it does show that people intuitively understand their implications when they are faced with them, and respond accordingly. Third, there are ethnographic descriptions of ‘disaster levels’, ‘crisis levels’, or ‘edges’ that affect the risk attitudes of people facing poverty 23 , 24 . For example, writing on Southeast Asia, Scott 23 describes the spectre of a “subsistence crisis level—perhaps a ‘danger zone’ rather than a ‘level’ would be more accurate…a threshold below which the qualitative deterioration in subsistence, security and status is massive and painful” (p. 17), as an ever-present factor in people’s decisions. Thus, including a desperation threshold is a simple but potentially powerful innovation into models of cooperation and exploitation, with potential to generate new insights.
In our model, agents repeatedly decide between three actions: foraging alone, foraging cooperatively, or exploiting a cooperative group. Foraging cooperatively is analogous to legitimate economic activity, and exploitation is analgous to acquisitive crime. Agents have variable levels of resources, and their behaviour is state-dependent. That is, rather than having a fixed strategy of always cooperating or always exploiting, each agent, at each interaction, selects a behaviour based on their current level of resources, the behaviour of others in the surrounding population, and background parameters such as the probability and severity of punishment, and the likelihood of resources improving through other means. Agents seek to maximize fitness. We assume that fitness is positively related to resource levels, but that there is a threshold, a critically low level of resources below which there is an immediate fitness penalty for falling. Our investigation of the model has two stages. We first compute the optimal action policy an individual should follow; that is, the optimal action to select for every possible combination of the situational variables. Second, we simulate populations of individuals all following the optimal action policies, to predict population-level outcomes for different initial resource distributions.
To explain the model in more detail, at each time point t in an indefinitely long sequence of time steps (where one time step is one economic interaction), agents have a current level of resources s. They can take one of three actions. Foraging alone costs x units of resources and is also guaranteed to return x. Thus, foraging alone is sufficient to maintain the agent but creates no increase in resources. It is also safe from exploitation, as we conceptualise it as involving minimal interaction with others. Alternatively, agents can team up with n-1 others to cooperate . As long as no other group member exploits, cooperation is mutually beneficial, costing x units but producing a payoff of \(\alpha x \left( {\alpha > 1} \right)\) to each group member. Finally, agents can exploit : join a cooperating group and try to selfishly divert the resources produced therein. If this exploitation is successful, they obtain a large reward β, but if they fail, they receive a punishment π. The probability of being punished is γ. The punishment is not administered by peers: we assume that there is a central punitive institution in place, and both the size and probability of punishment are exogenous. In our default case, the expected payoff for exploitation is zero (i.e. \(\left( {1 - \gamma } \right)\beta = \gamma \pi\) ), making exploitation no better than foraging alone on average, and worse than cooperating. However, the reward for a successful exploitation, β, is the largest payoff available to the agent in any single time step.
At every time step, each agent’s resource level is updated according to the outcomes of their action. In addition, resource levels change by a disturbance term controlled by a parameter r , such that the mean and variance of population resources are unchanged, but the temporal autocorrelation of agents’ resource levels is only 1 − r . If r is high, individuals whose current resources are low can expect they will be higher in the future and vice versa, because of regression to the mean. If \(r = 0\) , resources will never change other than by the agent’s actions. We consider r a measure of social mobility due to causes other than choice of actions.
In the first stage, we use stochastic dynamic programming 25 , 26 to compute the optimal action policy. Fitness is a positive linear function of expected resource level s in the future. However, in computing the fitness payoffs of each action, we also penalize, by a fixed amount, any action that leaves the agent below a desperation threshold in the next time step (arbitrarily, we set this threshold at s = 0). The optimal action policy identifies which one of the three actions is favoured for every possible combination of the factors that impinge on the agent. These include both their own current resource state s , and features of their social world, such as the severity of punishment π, the probability of punishment γ, and the level of social mobility r. A critical variable that enters into the computation of the optimal action is the probability that any cooperating group in the population will contain someone who exploits. We denote this probability p . We can think of 1 − p as an index of the trustworthiness of the surrounding population. Computing the optimal policy effectively allows us to ask: under what circumstances should an individual forage alone, cooperate, or exploit?
In the second stage, we simulate populations of agents all following the optimal policies computed in the first stage. We can vary the starting distributions of resources (their mean and dispersion), as well as other parameters such as social mobility and the probability and severity of punishment. During the simulation stage, each agent forms an estimate of 1 − p , the trustworthiness of others, through observing the behaviour of a randomly-selected subset of other individuals. We refer to these estimates as the agents’ social trust, since social trust is defined as the generalized expectation that others will behave well 27 . Social trust updates at the end of each time step. Agents’ social trust values are unbiased estimates of the current trustworthiness of the surrounding population, but they are not precise, because they are based on only a finite sample of other population members. The simulation stage, allows us to ask: what are the predicted temporal dynamics of behaviour, and of social trust, in populations with different starting distributions of resources, different levels of social mobility, and different punishments for exploitation?
Each of the three actions is optimal in a different region of the space formed by current resources s and the trustworthiness of others 1 − p (Fig. 1 a). Below a critical value of s , agents should always exploit, regardless of trustworthiness . In the default case, this critical value is in the vicinity of the desperation threshold, though it can be lower or higher depending on the value of other parameters. With our default values, exploitation will not, on average, make the agent’s resource state any better in subsequent time steps. However, there is a large advantage to getting above the threshold in the next time step, and there is a region of the resource continuum where exploitation is the only action that can achieve this in one go (intuitively, it is the quickest way to ‘get one’s head above water’). Where s is above the critical value, cooperation is optimal as long as the trustworthiness of the surrounding population is sufficiently high. However, if trustworthiness is too low, the likelihood of getting exploited makes cooperation worse than foraging alone. The shape of the frontier between cooperation and foraging alone is complex when resources are close to the desperation threshold. This is because cooperation and foraging alone also differ in riskiness; foraging alone is risk-free, but cooperation carries a risk of being exploited that depends on trustworthiness. Just above the exploitation zone, there is a small region where cooperation is favoured even at low trustworthiness, since one successful cooperation would be enough to hurdle back over the threshold, but foraging alone would not. Just above this is a zone where foraging alone is favoured even at high trustworthiness; here the agent will be above the threshold in the next time period unless they are a victim of exploitation, which makes them averse to taking the risk of cooperating.
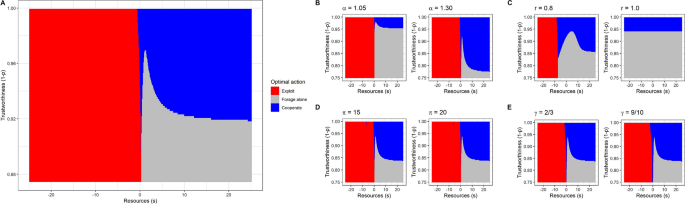
Optimal actions as a function of the individual’s current resources s and the trustworthiness of the surrounding population, 1 − p . ( A ) All parameters at their default values. This includes: α = 1.2, r = 0.1, π = 10, and γ = 1/3 (see Table 1 for a full list). ( B ) Effect of altering the efficiency of cooperation α to be either lower (1.05) or higher (1.30) than ( A ). Other parameter values are as for ( A ). ( C ) Effects of varying social mobility, to be either high (r = 0.8), or complete (r = 1.0; i.e. resource levels in this time period have no continuity at all into the next). Other parameter values are as for ( A ). ( D ) Effect of increasing the severity of punishment for exploiters to π = 15 and π = 20. Other parameter values are as for ( A ). ( E ). Effects of altering the probability of punishment for exploiters to γ = 2/3 and γ = 9/10. Other parameter values are as for ( A ).
We explored the sensitivity of the optimal policy to changes in parameter values. Increasing the profitability of cooperation (α) decreases the level of trustworthiness that is required for cooperation to be worthwhile (Fig. 1 B; analytically, the cooperation/foraging alone frontier for \(s \gg 0\) is at \(\left( {1 - p} \right) = 1/\alpha\) ; see Supplementary Sect. 2.2 ). A very high level of social mobility r moves the critical value for exploitation far to the left (i.e. individuals have to be in an even more dire state before they start to exploit; Fig. 1 C). This is because with high social mobility, badly-off individuals can expect that their level of resources will regress towards the mean over time anyway, lessening the need for risky action when faced with a small immediate shortfall.
The optimality of exploitation below the critical level of resources is generally insensitive to increasing the severity of punishment, π (Fig. 1 D), even where the expected value of exploitation is thereby rendered negative. This is because a desperate agent will be below the threshold in the next time step anyway if they forage alone, cooperate, or receive a punishment of any size. They are so badly off that it is relatively unimportant how much worse things get, but important to take any small chance of ‘jumping over’ the threshold. The exploitation boundary is slightly more sensitive to the probability of punishment, γ, though even this sensitivity is modest (Fig. 1 E). When γ is very high, it is optimal for agents very close to the boundary of desperation to take a gamble on cooperating, even where trustworthiness is rather low. Although this is risky, it offers a better chance of getting back above the threshold than exploitation that is almost bound to fail. Nonetheless, it is striking that even where exploitation is almost bound to fail and attracts a heavy penalty, it is still the best option for an individual whose current resource level is desperately low.
We also explored the effect of setting either the probability γ or the severity π of punishment so low that the expected payoff from exploitation is positive. This produces a pattern where exploitation is optimal if an agent’s resources are either desperately low, or comfortably high (see Supplementary Fig. S2 ). Only in the middle—currently above the threshold, but not by far enough that a punishment would not pull them down below it–should agents cooperate or forage alone.
We simulated populations of N = 500 individuals each following the optimal policy, with the distribution of initial resources s drawn from a distribution with mean μ and standard deviation σ. Populations fall into one of two absorbing equilibria. In the first, the poverty trap (Fig. 2 A), there is no cooperation after the first few time periods. Instead, there is a balance of attempted exploitation and foraging alone, with the proportions of these determined by the initial resource distribution and the values of π and γ. The way this equilibrium develops is as follows: there is a sufficiently high frequency of exploitation in the first round (about 10% of the population or more is required) that subsequent social trust estimates are mostly very low. With trust low, those with the higher resource levels switch to foraging alone, whilst those whose resources are desperately low continue to try to exploit. Since foraging alone produces no surplus, the population mean resources never increases, and both exploiters and lone foragers are stuck where they were.
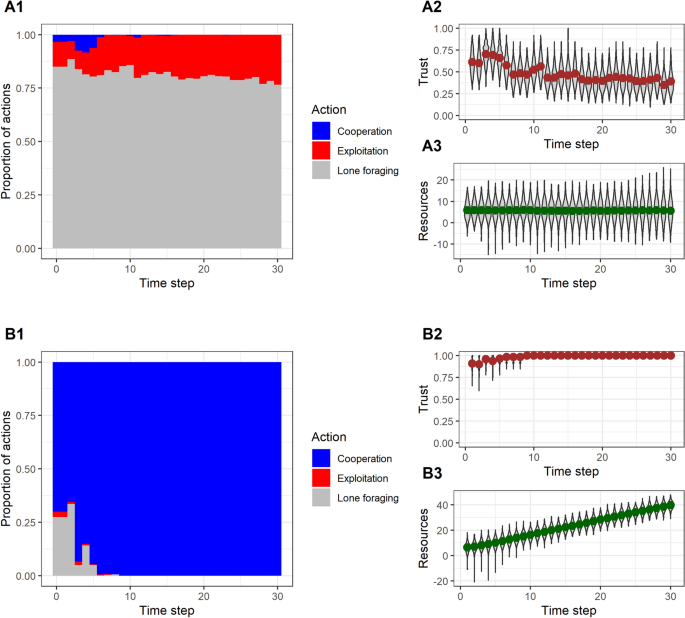
The two equilibria in simulated populations. ( A ) The poverty trap. There is sufficient exploitation in the first time step ( A1 ) that social trust is low ( A2 ). Consequently, potential cooperators switch to lone foraging, resources never increase ( A3 ), and a subgroup of the population is left below the threshold seeking to exploit. Simulation initialised with μ = 5.5, σ = 4 and all other parameters at their default values. ( B ) The virtuous circle. Exploitation is sufficiently rare from the outset ( B1 ) that trust is high ( B2 ) and individuals switch from lone foraging to cooperation. This drives an increase in resources, eventually lifting almost all individuals above the threshold. Simulation initialised with μ = 5.5, σ = 3 and all other parameters at their default values.
In the second equilibrium, the virtuous circle (Fig. 2 B), the frequency of exploitation is lower at the outset. Individuals whose resources are high form high assessments of social trust, and hence choose cooperation over foraging alone. Since cooperation creates a surplus, the mean level of resources in the population increases. This benefits the few exploiters, both through the upward drift of social mobility, and because they sometimes exploit successfully. This resolves the problem of exploitation, since in so doing they move above the critical value to the point where it is no longer in their interests to exploit, and since they are in such a high-trust population, they then start to cooperate. Thus, over time, trust becomes universally high, resources grow, and cooperation becomes almost universal.
Each of the two equilibria has a basin of attraction in the space of initial population characteristics. The poverty trap is reached if the fraction of individuals whose resource levels fall below the level that triggers exploitation is sufficiently large at any point. With the desperation threshold at s = 0, his fraction is affected by both the mean resources μ, and inequality σ. For a given μ, increasing σ (i.e. greater inequality) makes it more likely that the poverty trap will result, because, by broadening the resource distribution, the tail that protrudes into the desperation zone is necessarily made larger.
The boundaries of the basin of attraction of the poverty trap are also affected by severity of punishment, probability of punishment, and the level of social mobility (Fig. 3 ). If the severity of punishment π is close to zero, there is no disincentive to exploit, and the poverty trap always results. As long as a minimum size of punishment is met, further increases in punishment severity have no benefit in preventing the poverty trap (Fig. 3 A). Indeed, there are circumstances where more severe punishment can make things worse. When the population has a degree of initial inequality that puts it close to the boundary between the two equilibria, very severe punishment (π = 20 or π = 25) pushes it into the poverty trap. This is because any individual that once tries exploitation because they are close to threshold (and is unsuccessful) is pushed so far down in resources by the punishment that they must then continue to exploit forever. Increasing the probability of punishment γ does not have this negative effect (Fig. 3 B). Instead, a very high probability of punishment can forestall the poverty trap at levels of inequality where it would otherwise occur, because it causes some of the worst-off individuals to try cooperating instead, as shown in Fig. 1 E. Finally, very high levels of social mobility r can rescue populations from the poverty trap even at high levels of inequality (Fig. 3 C). This is because of its dramatic effect on the critical value at which individuals start to exploit, as shown in Fig. 1 C.
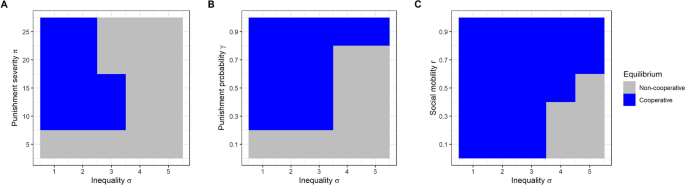
Equilibrium population states by starting parameters. ( A ) Varying the initial inequality in resources σ and the severity of punishment π, whilst holding constant the probability of punishment γ at 1/3 and social mobility r at 0.1. ( B ) Varying the initial inequality in resources σ and the probability of punishment γ whilst holding the severity of punishment constant at π = 10 and social mobility r at 0.1. ( C ) Varying the initial inequality in resources σ and the level of social mobility r whilst holding constant the probability of punishment γ at 1/3 and the severity of punishment π at 10.
Though the equilibria are self-perpetuating without exogenous forces, the system is highly responsive to shocks. For example, exogenously changing the level of inequality in the population (via imposing a reduction in σ after 16 time steps) produces a phase transition from the poverty trap to the virtuous circle (Supplementary Fig. S3 ). This change is not instantaneous. First, a few individuals cross the threshold and change from exploitation to foraging alone; this produces a consequent change in social trust; which then leads to a mass switch to cooperation, and growth in mean wealth.
Results so far are all based on cooperation occurring in groups of size n = 5. Reducing n enlarges the basin of attraction of the virtuous circle (Supplementary Sect. 2.5 , Supplementary Fig. S4 ). This is because, for any given population prevalence of exploitation, there is more likely to be at least one exploiter in a group of five than a group of three. Reducing the interaction group size changes the trustworthiness boundary between the region where it is optimal to cooperate and the region where it is better to forage alone. Thus, there are parameter values in our model where populations would succumb to the poverty trap by attempting to mount large cooperation groups, but avoid it by restricting cooperation groups to a smaller size.
In our model, exploiting others can be an individual’s optimal strategy under certain circumstances, namely when their resource levels are very low, and cannot be expected to spontaneously improve. We extend previous models by showing that it can be optimal to exploit even when the punishment for doing so and being caught is large enough to make the expected utility of exploitation negative. Two conditions combine to make this the case. First, exploitation produces a large variance in payoffs: it is costly to exploit and be caught, but there is a chance of securing a large positive payoff. Second, there is a threshold of desperation below which it is extremely costly to fall. It is precisely when at risk of falling below this threshold that exploitation becomes worthwhile: if it succeeds, one hurdles the threshold, and if it fails, one is scarcely worse off than one would have been anyway. In effect, due to the threshold, there is a point where agents have little left to lose, and this makes them risk-preferring. Thus, our model results connect classic economic models of crime 15 , 16 to risk-sensitive foraging theory from behavioural ecology 20 . In the process, it provides a simple answer to the question that has puzzled a number of authors 18 , 19 : why aren’t increases in the severity of punishments as deterrent as simple expected utility considerations imply they ought to be? Our model suggests that, beyond a minimum required level of punishment, not only might increasing severity be ineffective at reducing exploitation. It could under some circumstances make exploitation worse, by pushing punishees into such a low resource state that they have no reasonable option but to continue exploiting. Our findings also have implications for the literature on the evolution of cooperation. This has shown that punishment can be an effective mechanism for stabilising cooperation 28 , 29 , but have not considered that the deterrent effects of punishment may be different for different individuals, due to variation in their states. Our findings could be relevant to understanding why some level of exploitation persists in practice even when punishment is deterrent overall.
Within criminology, our prediction of risky exploitative behaviour when in danger of falling below a threshold of desperation is reminiscent of Merton’s strain theory of deviance 30 , 31 . Under this theory, deviance results when individuals have a goal (remaining constantly above the threshold of participation in society), but the available legitimate means are insufficient to get them there (neither foraging alone nor cooperation has a large enough one-time payoff). They thus turn to risky alternatives, despite the drawbacks of these (see also Ref. 32 for similar arguments). This explanation is not reducible to desperation making individuals discount the future more steeply, which is often invoked as an explanation for criminality 33 . Agents in our model do not face choices between smaller-sooner and larger-later rewards; the payoff for exploitation is immediate, whether successful or unsuccessful. Also note the philosophical differences between our approach and ‘self-control’ styles of explanation 34 . Those approaches see offending as deficient decision-making: it would be in people’s interests not to offend, but some can’t manage it (see Ref. 35 for a critical review). Like economic 15 , 16 and behavioural-ecological 17 theories of crime more generally, ours assumes instead that there are certain situations or states where offending is the best of a bad set of available options.
As well as a large class of circumstances where only individuals in a poor resource state will choose to exploit, we also identify some—where the expected payoff for exploitation is positive—where individuals with both very low and very high resources exploit, whilst those in the middle avoid doing so. Such cases have been anticipated in theories of human risk-sensitivity 21 . These distinguish risk-preference through need (e.g. to get back above the threshold immediately) from risk-preference through ability (e.g. to absorb a punishment with no ill effects), predicting that both can occur under some circumstances 32 . This dual form of risk-taking is best analogised to a situation where punishments take the form of fines: those who are desperate have to run the risk of incurring them, even though they can ill afford it; whilst those who are extremely well off can simply afford to pay them if caught. When we simulate populations of agents all following the optimal strategies identified by the model, population-level characteristics (inequality of resources, level of social mobility) affect the prevalence of exploitation and the level of trust. Specifically, holding constant the average level of resources, greater inequality makes frequent exploitation and low trust a more likely outcome. Thus, we capture the widely-observed associations between inequality, trust and crime levels that were our starting point 2 , 3 , 4 , 5 , 6 . Note that our explanation for the inequality-crime nexus is basically compositional rather than psychosocial. Decisions to offend are based primarily on agents’ own levels of resources; these are just more likely to be desperately low in more unequal populations. Turning these simulation findings into empirical predictions, we would expect the association between inequality and crime rates to be driven by more unequal societies producing worse prospects for people at the bottom end of the resources distribution, who would be the ones who turn to property crime. Inequality effects at the aggregate level should be largely mediated by individual-level poverty. There is evidence compatible with these claims for property crime 2 , 12 , 13 . This is the type of crime most similar to our modelled situation. Non-acquisitive crimes of violence, though related to inequality, do not appear so strongly mediated by individual-level poverty, and may thus require different but related explanations 2 , 36 .
However, the other major result of our population simulations—that more unequal populations are more likely to produce low trust—is not compositional. In our unequal simulated populations, every agent has low trust, not just the ones at the bottom of the resource distribution. This is compatible with empirical evidence: the association between inequality and social trust survives controlling for individual poverty 6 . Thus, our model generates a genuinely ecological effect of inequality on social relationships that fits the available evidence and links it to the psychosocial tradition of explanation 37 . Indeed, the model suggests a reason why psychosocial effects should arise. For agents above the threshold, the optimal decision between cooperation and foraging alone depends on inferences about whether anyone else in the population will exploit. To know that, you have to attend to the behaviour of everyone else, not just your own state. Thus, the model naturally generates a reason for agents to be sensitive to the distribution of others’ states in the population (or at the very least their behaviour), and to condition their social engagement with others on it.
In as much as our model provides a compositional explanation for the inequality-crime relationship, it might seem to imply that high levels of inequality would not lead to high crime as long as the mean wealth of the population was sufficiently high. This is because, with high mean wealth, even those in the bottom tail of the distribution would have sufficient levels of resources to be above the threshold of desperation. However, this implication would only follow if the location of the desperation threshold is considered exogenous and fixed. If, instead, the location of the desperation threshold moves upwards with mean wealth of the population, then more inequality will always produce more acquisitive crime, regardless of the mean level of population wealth. Assuming that the threshold moves in this way is a reasonable move: definitions of poverty for developed countries are expressed in terms of the resources required to live a life seen as acceptable or normal within that society, not an absolute dollar value (see Ref. 36 , pp. 64–6). Moreover, there is clear evidence that people compare themselves to relevant others in assessing the adequacy of their resources 38 . Thus, we would expect inequality to remain important for crime regardless of overall economic growth.
In addition to the results concerning inequality, we found that social mobility should, other things being equal, reduce the prevalence of exploitation, although social mobility has to be very high for the effect to be substantial. The pattern can again be interpreted as consistent with Merton’s strain theory of deviance 31 : very high levels of social mobility provide legitimate routes for those whose state is poor to improve it, thus reducing the zone where deviance is required. Economists have noted that those places within the USA with higher levels of intergenerational social mobility also have lower crime rates 39 , 40 . Their account of the causality in this association is the reverse of ours: the presence of crime, particularly violent crime, inhibits upward mobility 39 . However, it is possible that social mobility and crime are mutually causative.
Like any model, ours simplifies social situations to very bare elements. Interaction groups are drawn randomly at every time step from the whole population. Thus, there are no ongoing personal relationships, no reputation, no social networks, no kinship, no segregation or assortment of sub-groups. The model best captures social groups with frequent new interactions between strangers, which is appropriate since the phenomena under investigated are documented for commercial and industrial societies. A problem in mapping our findings onto empirical reality is that our population simulations generate two discrete equilibria: zero trust, economic stagnation and zero cooperation, or almost perfect trust, unlimited economic growth and zero exploitation. Although we show that the distribution of resources determines which equilibrium is reached, our model as presented here does generate the continuous relationships between inequality, crime, and trust (or indeed inequality and economic growth 41 ) that have been observed in reality. Even the most unequal real society features some social cooperation, and even the most equal features some property crime; the effects of inequality are graded. We make two points to try to bridge the disconnect between the black and white world of the simulations and the shades of grey seen in reality. First, our model does predict a continuous relationship between the level of inequality and the maximum size of cooperating groups. A highly unequal population, containing many individuals with an incentive to exploit, might only be able to sustain collective actions at the level of a few individuals, whereas a more equal population where almost no-one has an incentive to exploit could sustain far larger ones. Second, we appeal to all the richness of real social processes that our model excludes. In unequal countries, although social trust is relatively low, people can draw more heavily on their established social networks and reputational information; more homogenous sub-groups can segregate themselves; people can use defensive security measures, to keep cooperative relationships ongoing and protected; and so forth. Investment in these kinds of measures may vary proportionately with inequality and trust, thus maintaining outcomes intermediate between the stark equilibria of our simulations. Our key findings also depend entirely on accepting the notion that there is a threshold of desperation, a substantial non-linearity in the value of having resources. As we outlined in the Introduction, we believe there are good grounds for exploring the implications of such an assumption. However, that is very different from claiming that the widespread existence of such thresholds has been demonstrated. We hope our findings might generate empirical investigation into both the objective reality and psychological appraisal of such thresholds for people in poverty.
Limitations and simplifications duly noted, our model does have some clear implications. Large population-scale reductions in crime and exploitation should not be expected to follow from increasing the severity of punishments, and these could conceivably be counterproductive. Addressing basic distributional issues that leave large numbers of people in desperate circumstances and without legitimate means to improve them will have a much greater effect. Natural-experimental evidence supports this. The Eastern Cherokee, a Native American group with a high rate of poverty, distributed casino royalties through an unconditional income scheme. Rates of minor offending amongst young people in recipient households decline markedly, with no changes to the judicial regime 42 . Improving the distribution of resources would also be expected to increase social trust, and with it, the quality of human relationships; and this, for everyone, not just those in desperate circumstances.
The model was written in Python and implemented via a Jupyter notebook. For a fuller description of the model, see Supplementary Sect. 1 and Supplementary Table S1 .
Computing optimal policies
We used a stochastic dynamic programming algorithm 25 , 26 . Agents choose among a set of possible actions, defined by (probabilistic) consequences for the agent’s level of resources s . We seek, for every possible value of s and of p the agent might face, and given the values of other parameters, the action that maximises expected fitness. Maximization is achieved through backward induction: we begin with a ‘last time step’ ( T ) where terminal fitness is defined, as an increasing linear function of resource level s . Then in the period T − 1 we compute for each combination of state variables and action the expected fitness at T , and thus choose for the optimal action for every combination of states. This allows us define expected fitness for every value of the state variables at T − 1, repeat the maximization for time step T − 2, and so on iteratively. The desperation threshold is implemented as a fixed fitness penalty ω that is applied whenever the individual’s resources are below the threshold level s = 0. As the calculation moves backwards away from T , the resulting mapping of state variables to optimal actions converges to a long term optimal policy.
Actions and payoffs
Agents choose among three actions:
Cooperate The agent invests x units of resource and is rewarded α · x with probability 1 − p ( p is the probability of cooperation being exploited, and 1 − p is therefore the trustworthiness of the surrounding population), and 0 with probability p . The net payoff is therefore x · ( α − 1) if there is no exploitation and − x if there is. We assume that α > 1 (by default α = 1 . 2), which means that cooperation is more efficient than foraging alone. For the computation of optimal policies, we treat p as an exogenous variable. In the population simulations, it becomes endogenous.
Exploit An agent joins a cooperating group, but does not invest x, and instead tries to steal their partners’ investments, leading to a reward of β if the exploitation succeeds and a cost π if it fails. The probability of exploitation failing (i.e. being punished) is γ .
Forage alone The agent forages alone, investing x units of resource, receiving x in return, and suffering no risk of exploitation.
Payoffs are also affected by a random perturbation, so the above-mentioned payoffs are just the expected values. A simple form such as the addition of \(\varepsilon \sim N\left( {0, \sigma^{2} } \right)\) would be unsuitable when used in population simulations. As the variance of independent random variables is additive, it would lead to an ever increasing dispersion of resource levels in the population. To avoid this issue, we adopted a perturbation in the form of a first-order autoregressive process that does not change either the mean or the variance of resources in the population 43 :
Here, µ is the current mean resources in the population and σ 2 the population variance. The term \(\left( {1 - r} \right) \in \left[ {0, 1} \right]\) represents the desired correlation between an agent’s current and subsequent resources, which leads to us describing r as the ‘social mobility’ of the population. The perturbation can be seen as a ‘shuffle’. Each agent’s resource level is attracted to µ with a strength depending on r , but this regression to the mean is exactly offset at the population level by the variance added by the perturbation, so that the overall distribution of resources is roughly unchanged. If r = 1, current resources are not informative about future resources.
The dynamic programming equation
Let I be the set of actions ( cooperate , exploit and alone ), which we shorten as I = { C,H,A }. For i ∈ I , we denote as \(\phi_{t}^{i} \left( {s, .} \right)\) the probability density of resources in in time step t if, in time step t − 1, the resource level is s and the chosen action i . The expressions of these functions were obtained through the law of total probability, conditioning on the possible outcomes of the actions (e.g. success or failure of exploitation and cooperation), and with the Gaussian density of the random variable.
We can now write the dynamic programming equation, which gives the backward recurrence relation to compute the payoff values (and the decisions) at the period t from the ones at the period t + 1.
Here, \(E_{i}\) is the conditional expectation if action i is played. The optimal action for the time step t is \({\text{argmax}}_{i \in I} E_{i} (f_{t} )\) . The resource variable s was bounded in the interval [− 50, 50], and discretized with 1001 steps of size 0 . 1.
For any given set of parameters (summarised in Table 1 ), we can therefore compute the optimal decision rule. Note that we can distinguish two types of parameters:
‘Structural parameters’, i.e. those defining the ‘rules’ of the game (the payoffs for the actions and the level of social mobility r , for example). In the subsequent simulation phase, these parameters will be fixed for any run of the simulations.
‘Input parameters’, such as p and s . In the simulation phase, these will evolve endogenously.
Optimal policies rapidly stabilize as the computation moves away from T . We report optimal actions at t = 1 as the globally optimal actions.
Population simulations
We begin each simulation by initializing a population of N = 500 individuals, whose resource levels are randomly drawn from a Gaussian distribution with a given mean µ and variance σ 2 . At each time step, interaction groups of n = 5 individuals are formed at random, and re-formed at each time step to avoid effects of assortment. There is no spatial structure in the populations. Each individual always follows the optimal policy for its resources s and its estimate of p (see below). Varying N has no effect as long as N > n and 500 is simply chosen for computational convenience.
To deal with the case where several members of the same interaction group choose to exploit, we choose one at random that exploits, and the others are deemed to forage alone (in effect, there is nothing left for them to take). Also, when there is no cooperator in the group, all exploiters are deemed to forage alone.
Rather than providing each individual with perfect knowledge of the trustworthiness of the rest of the population 1 − p , we allow individuals to form an estimate (their social trust ) from their experience. Social trust is derived in the following way. Each agent observes the decision of a sample of K individuals in the population, counts the number k of exploiters and infers an (unbiased) estimate of the prevalence of exploiters in the population: \(k^{\prime} = \frac{k}{K}N\) (rounded). The size of the sample can be varied to alter the precision with which agents can estimate trustworthiness. Unless otherwise stated we used K = 50. Since p is the probability that there will be at least one exploiter in an interaction group, it is one minus the probability that there will be zero exploiters. Each agent computes this from their k’ by combinatorics.
An intentional consequence of social trust being estimated through sampling is that there is some population heterogeneity in social trust, and therefore in decisions about which action to take, even for agents with the same resources s . Note also that agents infer trustworthiness not from observing the particular individuals in their current interaction group, but rather, from a cross-section of the entire population. Thus, the estimate is genuinely social trust (the perception that people in society generally do or do not behave well).
Code availability
The Jupyter notebook for running the model is available at: https://github.com/regicid/Deprivation-antisociality . This repository also contains R code and datafiles used to make the figures in the paper.
Tomasello, M. The ultra-social animal. Eur. J. Soc. Psychol. 44 , 187–194 (2014).
Article Google Scholar
Kelly, M. Inequality and crime. Rev. Econ. Stat. 82 , 530–569 (2000).
Rufrancos, H. & Power, M. Income inequality and crime: A review and explanation of the time-series evidence. Sociol. Criminol. 1 , 1–9 (2013).
Google Scholar
Krohn, M. D. Inequality, unemployment and crime: A cross-national analysis. Sociol. Q. 17 , 303–313 (1976).
Barone, G. & Mocetti, S. Inequality and trust: New evidence from panel data. Econ. Inq. 54 , 794–809 (2016).
Kennedy, B. P., Kawachi, I., Prothrow-Stith, D., Lochner, K. & Gupta, V. Social capital, income inequality, and firearm violent crime. Soc. Sci. Med. 47 , 7–17 (1998).
Article CAS Google Scholar
Oishi, S., Kesebir, S. & Diener, E. Income inequality and happiness. Psychol. Sci. 22 , 1095–1100 (2011).
Pickett, K. E. & Wilkinson, R. G. Income inequality and health: A causal review. Soc. Sci. Med. 128 , 316–326 (2015).
Ecob, R. & Davey Smith, G. Income and health: What is the nature of the relationship?. Soc. Sci. Med. 48 , 693–705 (1999).
Nettle, D. Why inequality is bad. In Hanging on to the Edges: Essays on Science, Society and the Academic Lifeg 111–128 (OpenBook Publishers, 2018).
Pridemore, W. A. A methodological addition to the cross-national empirical literature on social structure and homicide: A first test of the poverty-homicide thesis. Criminology 46 , 133–154 (2008).
Machin, S. & Meghir, C. Crime and economic incentives. J. Hum. Resour. 39 , 958–979 (2004).
Raphael, S. & Winter-Ebner, R. Identifying the effect of unemployment on crime. J. Law Econ. 44 , 259–283 (2001).
Wilkinson, R. G. & Pickett, K. E. The Spirit Level: Why Equal Societies Almost Always Do Better . (Allen Lane, 2009).
Becker, G. S. Crime and punishment: An economic approach. J. Polit. Econ. 76 , 169–217 (1968).
Ehrlich, I. Participation in illegitimate activities: A theoretical and empirical investigation. J. Polit. Econ. 81 , 521–565 (1973).
Cohen, L. E. & Machalek, R. A general theory of expropriative crime: An evolutionary ecological approach. Am. J. Sociol. 94 , 465–501 (1988).
Dölling, D., Entorf, H., Hermann, D. & Rupp, T. Is deterrence effective? Results of a meta-analysis of punishment. Eur. J. Crim. Policy Res. 15 , 201–224 (2009).
Nagin, D. S. Deterrence: A review of the evidence by a criminologist for economists. Annu. Rev. Econ. 5 , 83–105 (2013).
Stephens, D. W. The logic of risk-sensitive foraging preferences. Anim. Behav. 29 , 628–629 (1981).
Mishra, S., Barclay, P. & Sparks, A. The relative state model: Integrating need-based and ability-based pathways to risk-taking. Personal. Soc. Psychol. Rev. 21 , 176–198 (2017).
Mishra, S. & Lalumière, M. L. You can’t always get what you want: The motivational effect of need on risk-sensitive decision-making. J. Exp. Soc. Psychol. 46 , 605–611 (2010).
Scott, J. C. The Moral Economy of the Peasant: Rebellion and Subsistence in Southeast Asia . (Yale University Press, London, 1976).
Nettle, D. Tyneside Neighbourhoods: Deprivation, Social Life and Social Behaviour in One British City . (OpenBook Publishers, 2015).
Houston, A. I. & McNamara, J. M. Models of Adaptive Behaviour: An Approach Based on State . (Cambridge University Press, Cambridge, 1999).
Mangel, M. & Clark, C. W. Dynamic Modeling in Behavioral Ecology . (Princeton University Press, Princeton, 1988).
Verducci, S. & Schröer, A. Social Trust. In International Encyclopedia of Civil Society (eds. Anheier, H. K. & Toepler, S.) 1453–1458 (Springer US, 2010). https://doi.org/10.1007/978-0-387-93996-4_68 .
Boyd, R. & Richerson, P. J. Punishment allows the evolution of cooperation (or anything else) in sizable groups. Ethol. Sociobiol. 13 , 171–195 (1992).
García, J. & Traulsen, A. Evolution of coordinated punishment to enforce cooperation from an unbiased strategy space. J. R. Soc. Interface 16 , 20190127 (2019).
Baumer, E. P. & Gustafson, R. Social organization and instrumental crime: Assessing the empirical validity of classic and contemporary anomie theories. Criminology 45 , 617–663 (2007).
Merton, R. K. Social structure and anomie. Am. Sociol. Rev. 3 , 672–682 (1938).
Barclay, P., Mishra, S. & Sparks, A. M. State-dependent risk-taking. Proc. R. Soc. B Biol. Sci. 285 , 20180180 (2018).
Lee, C. A., Derefinko, K. J., Milich, R., Lynam, D. R. & DeWall, C. N. Longitudinal and reciprocal relations between delay discounting and crime. Pers. Individ. Dif. 111 , 193–198 (2017).
Gottfredson, M. R. & Hirshi, T. A General Theory of Crime . (Stanford University Press, Stanford, 1990).
Burt, C. H. Self-control and crime: Beyond Gottfredson & Hirschi’s theory. Annu. Rev. Criminol. 3 , 43–73 (2020).
Daly, M. Killing the Competition: Economic Inequality and Homicide . (Transaction, 2016).
Wilkinson, R. G. & Pickett, K. E. The enemy between us: The psychological and social costs of inequality. Eur. J. Soc. Psychol. 47 , 11–24 (2017).
Payne, B. K., Brown-Iannuzzi, J. L. & Hannay, J. W. Economic inequality increases risk taking. Proc. Natl. Acad. Sci. U. S. A. 114 , 4643–4648 (2017).
Sharkey, P. & Torrats-Espinosa, G. The effect of violent crime on economic mobility. J. Urban Econ. 102 , 22–33 (2017).
Chetty, R., Hendren, N., Kline, P. & Saez, E. Where is the land of opportunity? The geography of intergenerational mobility in the United States. Q. J. Econ. 129 , 1553–1623 (2014).
Alesina, A. & Rodrik, D. Distributive politics and economic growth. Q. J. Econ. 109 , 465–490 (1994).
Akee, K. Q. R., Copeland, W., Keeler, G., Angold, A. & Costello, E. J. Parents’ incomes and childrens’ outcomes: A quasi-experiment. Am. Econ. J. Appl. Econ. 2 , 86–115 (2010).
Bateson, M. & Nettle, D. The telomere lengthening conundrum—it could be biology. Aging Cell 16 , 312–319 (2017).
Download references
Acknowledgements
This project has received funding from the European Research Council (ERC) under the European Union’s Horizon 2020 research and innovation programme (Grant agreement No AdG 666669, COMSTAR). The funders had no role in study design, data collection and analysis, decision to publish or preparation of the manuscript. The authors thank Melissa Bateson, Juliette Dronne, Ulysse Klatzmann, Daniel Krupp, Kate Pickett, and Rebecca Saxe for their input.
Author information
Authors and affiliations.
Institut Jean Nicod, Département d’études cognitives, ENS, EHESS, PSL Research University, CNRS, Paris, France
Benoît De Courson
Population Health Sciences Institute, Newcastle University, Newcastle, UK
Benoît De Courson & Daniel Nettle
You can also search for this author in PubMed Google Scholar
Contributions
The project was conceived jointly by B.C. and D.N. The model was developed and programmed by B.C. with feedback from D.N. B.C. wrote the first draft of the paper. The two authors revised and refined it collaboratively.
Corresponding author
Correspondence to Daniel Nettle .
Ethics declarations
Competing interests.
The authors declare no competing interests.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Supplementary information., rights and permissions.
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ .
Reprints and permissions
About this article
Cite this article.
De Courson, B., Nettle, D. Why do inequality and deprivation produce high crime and low trust?. Sci Rep 11 , 1937 (2021). https://doi.org/10.1038/s41598-020-80897-8
Download citation
Received : 02 November 2020
Accepted : 23 December 2020
Published : 21 January 2021
DOI : https://doi.org/10.1038/s41598-020-80897-8
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
This article is cited by
Leveraging social cognition to promote effective climate change mitigation.
- Mélusine Boon-Falleur
- Aurore Grandin
- Coralie Chevallier
Nature Climate Change (2022)
By submitting a comment you agree to abide by our Terms and Community Guidelines . If you find something abusive or that does not comply with our terms or guidelines please flag it as inappropriate.
Quick links
- Explore articles by subject
- Guide to authors
- Editorial policies
Sign up for the Nature Briefing newsletter — what matters in science, free to your inbox daily.
- Systematic Review
- Open access
- Published: 18 December 2022
Weather and crime: a systematic review of the empirical literature
- Jonathan Corcoran ORCID: orcid.org/0000-0003-3565-6061 1 &
- Renee Zahnow 2
Crime Science volume 11 , Article number: 16 ( 2022 ) Cite this article
12k Accesses
7 Citations
15 Altmetric
Metrics details
The weather-crime association has intrigued scholars for more than 150 years. While there is a long-standing history of scholarly interest in the weather-crime association, the last decade has evidenced a marked increase in the volume and diversity of empirical studies concerned with weather and its social implications including crime. In this paper we conduct a review of the empirical literature on weather and crime. This is the first review on the topic for more than 30 years. We highlight the theoretic and empirical challenges that persist and act to impede our understanding and chart four interrelated thematic areas that require concerted attention. These are to: (1) strengthen and integrate theoretical explanations of the weather-crime association; (2) model multi-dimensional processes of the weather-crime association; (3) broaden the situational, climatic, and cultural contexts of study; and (4) to translate research into policy and practice. We conclude by advocating for scholarship to advance the four thematic areas such that we progress towards a more complete and robust understanding of the weather-crime association.
Weather plays an intrinsic and ever-present role in our everyday lives. From the daily commute to our recreational pursuits, the weather shapes and structures activities and behavioural choices that we make (Cohn & Rotton, 2000 ; De Freitas, 1990 ). Through its capacity to influence where, when, and how daily activities take place, weather also has implications for crime (Cohn, 1993 ; Cohn & Rotton, 2000 ; LeBeau & Corcoran, 1990 ). Empirical research demonstrates a consistent link between higher temperatures and increased rates of violent crime (Anderson & Anderson, 1996 ; Butke & Sheridan, 2010 ; Cohn, 1993 ; Cook et al., 2012 ; Field, 1992 ; Hipp et al., 2004 ; LeBeau & Corcoran, 1990 ; Mapou et al., 2017 ; Michael & Zumpe, 1983 ; Michel et al., 2016 ; Ranson, 2014 ; Rotton & Cohn, 2003 ; Schinasi & Hamra, 2017 ). Yet, some discrepancies emerge between studies regarding operational definitions of weather phenomena; crime type; temporality and spatial unit of analysis. Inconsistencies also emerge between studies regarding the proposed pathway through which the weather-crime association operates.
Several theoretical perspectives have been applied, across disciplines, to explain the link between weather and crime. Most predominantly, recent scholarship adopts a framework based on routine activity theory or the generalised temperature aggression hypothesis. In the context of the weather-crime association, routine activity theory, posits that weather shapes individuals’ behavioural decisions and mobility over various granularities of time and in doing so conditions the location and timing of crime opportunities (Cohen & Felson, 1979 ; Cohn & Rotton, 2000 ; LeBeau & Coulson, 1996 ). The generalised temperature-aggression hypothesis, is grounded in human physiology and social psychology (Anderson, 1989 ) and suggests that high levels of heat and humidity induce physiological discomfort and psychological intolerance which exacerbate aggressive tendencies leading to impulsive offending (Anderson, 1989 , Anderson & Anderson, 1996 ; Baron & Lawton, 1972 ). Contemporary weather-crime studies suggest these two pathways may be complementary and can be applied in conjunction with one another to explain the way in which weather conditions can (a) shape opportunities for physical encounters and social interactions between potential victims or targets and offenders; and (b) effect emotional responses and behavioural decisions during physical encounters and social interactions (Afon & Badiora, 2018 ; Hu et al., 2017 ; Schinasi & Hamra, 2017 ).
The weather-crime connection was first noted in the 1800s when Belgian astronomer Adophe Quetelet identified seasonal trends and summer peaks in violent crime in France (Quetelet, 1842 , see also Dexter, 1899 ; Hill, 1884 ). Scholarly development on the association between weather and crime has continued over the ensuing decades with a notable peak in psychological and criminological studies in the 1990s. Since 2008, research interest in the weather-crime nexus has again increased with studies emerging from a range of disciplinary perspectives. Driven by data availability, ease of access to requisite weather and crime data and most importantly increasing concern over extreme weather events and the effects of climate change, there is currently a renewed focus on understanding the social consequences of weather to inform preparedness strategies.
In a systematic review of weather-crime research conducted in 1990s, Cohn ( 1990 ) noted most studies found evidence to support a positive, linear association between temperature and rates of violent crime. However, research on property and non-aggressive crimes was limited and there was no evidence of an association between heat and higher rates of these crime types. In concluding the review, Cohn ( 1990 ) highlighted four important considerations for future research on the relationship between weather and crime: (1) theoretical grounding; (2) operational measures of crime and weather (3) temporal granularity, and; (4) statistical techniques. Thirty years on from this study, and in the context of a renewed focus on weather and its social consequences in this paper we provide a systematic review of the weather-crime literature focusing on the four themes presented in Cohn’s 1990s review. Through concentrating on these themes, we provide insight into the primary developments in the field over the last three decades, explore the extent to which research has addressed these considerations and identify the gaps in current knowledge.
As humanity begins to realise the immediacy of climate change consequences to include the increased frequency and severity of prevailing weather conditions, a comprehensive understanding of the weather-crime association is required to inform practical policing, planning and place management policies. Fortunately, data availability and access to weather and crime data at fine temporal and spatial granularities has never been greater, alongside consideration of some of the theoretical weather-crime pathways that climate change might activate (Miles-Novelo & Anderson, 2019 , 2022 ). Here we synthesise the current state of the weather-crime literature and explore the extent to which research has addressed needs first identified by Cohn ( 1990 ), to inform an agenda for future weather-crime research.
Methods: protocol and capture
Our review follows the principles laid out in the PRISMA Statement for Reporting Systematic Reviews (Moher et al., 2009 ). See Additional file 1 : Table S1. We draw on this “mixed-method review” methodology (Gough, 2015 ) to build an understanding of both empirical results and theoretical developments in the field. Adopting this approach permits us to integrate the standard methods of a systematic review (e.g., selection of keywords and sources and eligibility criteria) alongside the openness and flexibility of traditional literature reviews. No review protocol was used in this study.
The articles that constituted the review were captured via a search of three databases; (1) Google Scholar; (2) Web of Science; and (3) Scopus. A complementary suite of keywords that together incorporate the range of terms associated with weather-crime studies were employed. Search terms were derived from a combination of the authors’ knowledge of the research space alongside terms that arose through the course of the systematic review process. The primary search term was “weather AND crime” alongside substituting ‘crime’ with specific crime types that included: ‘assault’; ‘homicide’; ‘murder’; ‘rape’; ‘robbery’; and ‘domestic violence’. In addition, the term ‘weather’ was also substituted with the following terms: ‘temperature’; ‘heat’; ‘photoperiod’; ‘season’ and ‘precipitation’. Furthermore, the reference lists of included studies were closely inspected such that we ensured a full coverage of all published articles in the weather-crime space. Searches were initially undertaken on 28th June 2021. The final intake of studies into the review was completed on 24th January 2022. To enhance the currency and coverage of the articles captured principles of the living systematic review methodology were adopted (Elliott et al., 2014 ).
In addition to our search terms (noted above) a set of inclusion and exclusion criteria were used. These criteria were:
Studies were included if they adopted an empirical approach to examine the weather-crime association.
Book reviews and magazines were excluded.
Only studies published in English were included.
The three criteria above were used to ensure we captured studies that offered a detailed empirical analysis of weather-crime associations. Further to these criteria we imposed no restrictions on when the study was published or the outlet in which the piece was published.
There are two limitations of the current review that require noting. First relates to the fragmentary nature of the weather-crime scholarship; that is to say that weather-crime scholarship is published across a suite of academic domains. This is highlighted by the fact that 11% (41 studies) of the included studies were identified from reference lists of studies captured in the systematic literature search. The range of keywords that were employed to locate the weather-crime literature generated a large volume of false-positive results. Second, there were a total of 7 studies that were not able to be progressed to a full screening as access to the full text was not possible. Each of these studies are listed in Additional file 1 : Table S3.
Results and discussion: weather-crime scholarship
Publication timelines, weather parameters and crime types.
Collectively, our search strategy initially returned approximately 6600 candidate documents (Fig. 1 ). After removing duplicates, titles and abstracts were screened for eligibility resulting in a reduction to 407 articles. The final stage involved a screening of full texts resulting in the removal of a further 224 articles and a total of 7 articles that were not able to be accessed. An additional 24 articles were manually Footnote 1 identified from other sources, resulting in a total of 200 studies being selected for analysis.
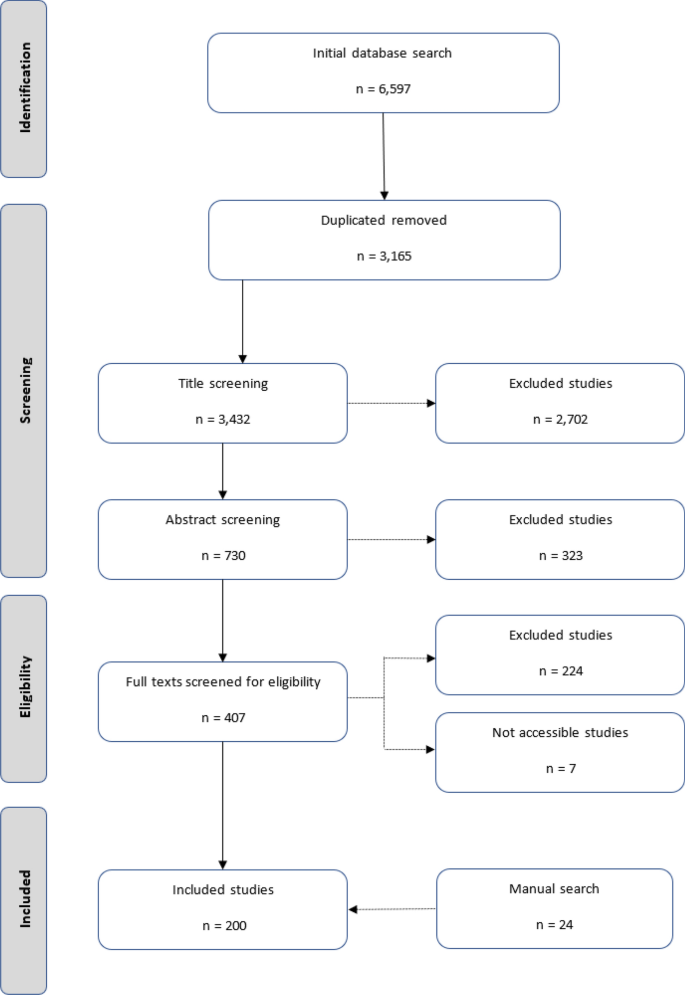
PRISMA flow diagram
A total of 200 studies were published between 1842 and 2021(Table 1 ). Fifty percent of the included studies were published between 2004 and 2021, reflecting sustained interest in weather and its social consequences since the rise of the climate change agenda (see Additional file 1 : Table S2). A total of 94.0% were published as journal articles, followed by 2.5% as books/book chapters and the remaining 3.5%, as conference papers, reports or theses.
Most frequently, studies (23.4%) examined the role of temperature followed by 19.2% that investigated the way in which season impacts crime. Figure 2 reports the total of thirteen weather parameters that have been investigated across all 200 studies. Over time, there has been a general increase in the variety of weather parameters explored.
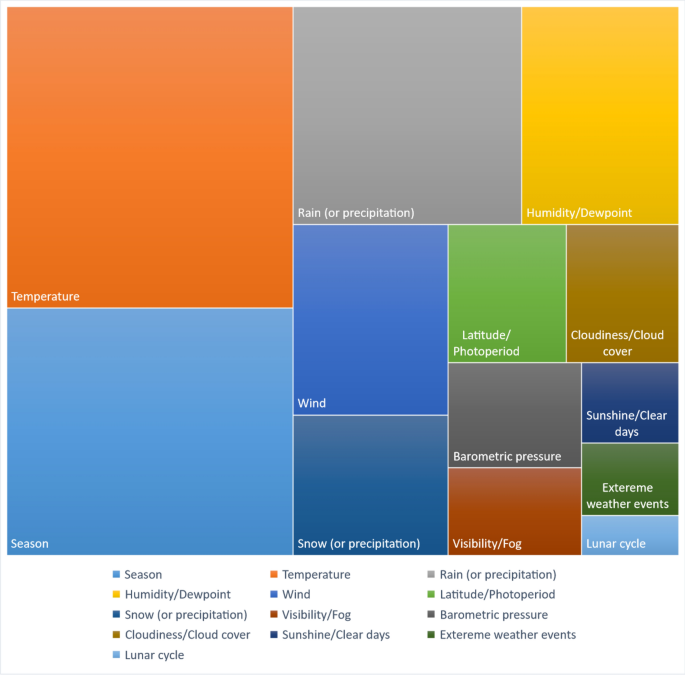
Weather parameters investigated
The overwhelming majority of studies (72.9%) examined the effect of weather on violent crime (a category that includes rape and sexual assault, robbery, assault, crimes against the person and murder), with 27.1% investigating non-violent crime types (includes, auto theft, burglary, and other property crimes). Studies examining weather and violent crime were predominantly focused on: homicide (25%), assault (24%) and crimes against the person (15%). Studies examining weather and non-violent crimes most frequently focused on: property crimes Footnote 2 (43%); burglary (34%) and auto theft (23%).
Geographic and climatic contexts
Most frequently, studies (56.9%) examined the weather-crime association in a North American context that broadly represents the temperate bio-climatic zone. The next largest group of studies were focussed on Europe (17.2%), again largely representing study contexts situated in temperate climatic zones. Other climatic zones (including tropical, sub-tropical and cold climates) were underrepresented in the sampled weather-crime studies as were countries with economies other than ‘high income’ (For more details see Additional file 1 : Table S3). Less studied parts of the world include Africa (n = 9) and South America (n = 5). In the case of both settings, all research dated post-2000 except for a single study in Johannesburg, South Africa conducted in 1980.
A small number of studies (n = 5) adopted a cross-national comparative frame of analysis. The first such study was conducted in 1986, the remaining four since 1999.
Geographical and temporal units of analysis
The most frequently adopted spatial unit is citywide accounting for 42.8% of all included studies (Fig. 3 ). Footnote 3 Studies focussed on a district scale account for the second most popular scale of analysis (13.9%) closely followed by those at an institutional scale (13.0%) examining the weather-crime relationship within health-related, educational, and correctional institutions. Notable is the emergence and growth of studies focussed on finer geographical units to include neighbourhoods and below. Rural settlements are the focus on only 1 study and have remained an under investigated spatial unit in weather-crime scholarship. (For more details see Additional file 1 : Table S3).
Spatial unit of analysis
The two temporal unit most employed is daily and monthly. Studies conducted using weather and crime data at the daily unit account for 30.9%, that is the same proportion of studies using a monthly unit of analysis (30.9%) (Fig. 4 ). Footnote 4 Fewer studies employed yearly (12.3%), quarterly (10.3%), weekly (3.7%) and sub daily (11.9%) temporal units. A notable number of studies (n = 47, 23.5%) examine the weather-crime association using multiple temporal units, the most typical combination of units being year and month (n = 8), followed by studies using three temporal units, specifically month, day, and sub-daily intervals (n = 7). There is evidence of a shift towards greater use of finer temporal units over the last two decades with daily and below daily units of analysis emerging as most common by 2010 and representing 44.3% of included studies in the years since 2010. (See Additional file 1 : Table S3 for more details).
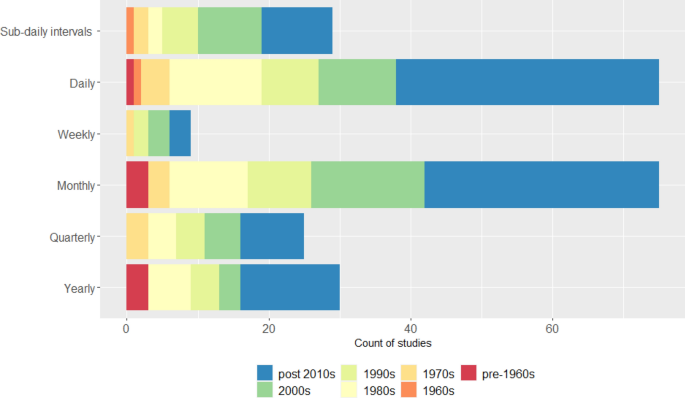
Temporal unit of analysis
Empirical methods
Typically, studies on weather and crime use descriptive analysis. This strategy is employed by 41.7% of studies. Other approaches include analytic modelling Footnote 5 (34.8%), correlation (21.7%), and experimental methods (laboratory-based) (1.9%). Many of the included studies (n = 152 or 77.6%) contained multiple empirical elements the most typical combination being a descriptive analysis followed by a modelling component (n = 62). (See Additional file 1 : Table S3 for more details).
Theoretical frameworks
One quarter of studies do not explicitly employ theoretic framing (25.0%) to explain study findings. Situational theories of crime appear most frequently as the primary theoretic framework (37.5%) followed by psychological (27.0%), physiological (5.0%), biological (3.0%), economic (1.5%) and finally social theories (1.0%). Footnote 6 A total of 28.4% of studies employ two and 3.4% use three theoretic frameworks to explain their findings, with the most used combination being Psychological and Physiological (accounting for 45.8% of the studies using two theoretic frameworks). In sum, situational studies predominantly cite Routine Activity Theory while psychological studies most commonly refer to the generalised temperature-aggression hypothesis. (For more details see Additional file 1 : Table S3).
Exploring the findings for the most examined relationship in the weather-crime scholarship, namely temperature and season on property crime and violent crime reveals a varied picture. Of the 200 studies, 52.5% examined temperature and violent crimes, 39.5% season and violent crime, 29.5% temperature and property crime, and 26.5% season and property crime. By classifying the empirical relationship reported in each study into positive; negative; curvilinear or no correlation Fig. 5 A reveals the relationships between season, temperature, and property crime and violent crime.
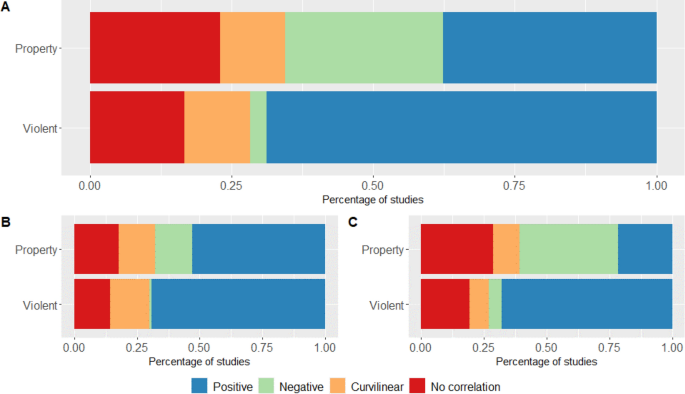
Associations between heat and crime measured through season and temperature. A Both season and temperature. B Season only. C Temperature only
Of note is the dominance of a significant positive linear association particularly so for violent crimes (accounting for 69% of all relationships). The picture for property crimes is less clear with 38% of studies reporting significant positive relationships, 28% a negative relationship, 11% a curvilinear relationship and 23% reporting no statistical significance.
Figure 5 B and C unpack the relationships specifically for the relationship between season (Fig. 5 B) and temperature (Fig. 5 C) on property crimes and violent crimes. The dominant linear relationship with violent crimes remains consistent between studies looking at temperature (69%) and season (68%), with larger differences existing for property crimes where 53% of studies found a linear relationship between temperature and property crime and only 21% between season and property crimes. (For more details on the data used to generate Fig. 5 see Additional file 1 : Table S4).
We note that studies in the sample (used to generate Fig. 5 ) measure temperature at various temporal scales including average hourly temperature (Anderson & Anderson, 1984 ), mean daily temperature (Sivarajasingam et al., 2004 ), maximum daily temperature (Gates et al., 2019 ) and mean monthly temperature (Linning et al., 2017 ), which could account some of the variation in findings.
Theoretically these findings underline the complexities of the weather-crime relationship. There is moderate agreement among studies that temperature is positively associated with violence. This may be due to changes in routine activities during warmer weather that facilitate greater opportunities for interaction, particularly after dark. However, these changes in activities cannot be disentangled from the psychological impacts of temperature increases on individuals. Thus, contemporary literature moves towards the application of two or more theories to interpret these associations (with 59 or 29.5% of studies adopting two or more theoretical frameworks) more fully. The overwhelming focus in the weather-crime scholarship has been on the role of warmer temperatures on crime, however there are some studies that have also pointed to important relationships between colder temperature and crime (Ranson, 2014 ; Stevens et al., 2021 ).
Although testing for non-linearity in statistics generally represents a more recent phenomena, the first detected non-linear relationship in the weather-crime scholarship was very early. In fact, the first appearance was in the Dexter study of 1899 in examining the relationship between temperature and violence. However, it was not until the 1970s when the empirical exploration of non-linearity in the context of temperature and crime emerged through exploration of the temperature aggression hypothesis (Quetelet, 1842 ) and the negative affect escape (NAE) model (Baron, 1972 ; Baron & Bell, 1976 ). The NAE model proposed that there exists a non-linear relationship between physical aggressions in which violence rises alongside temperature up to a certain point beyond which the relationship shifts becoming negative. A total of 60 (33%) of all included studies have tested for non-linearity in exploring the association between temperature and crime with a particular focus on violent crime. Of the 60 studies that specifically test for non-linearity 26% drew on the temperature aggression hypothesis, 24% on Routine Activity Theory (RAT) (Cohen & Felson, 1979 ), and 16% both the temperature aggression hypothesis alongside RAT as the more fitting theoretical explanation. A total of 34% of studies did not explicitly employ a theoretical explanation. Overall, 37% of studies (of those explicitly testing for non-linearity Footnote 7 ) found empirical support for non-linearity. Interestingly 3% of studies (of those explicitly testing for non-linearity) found empirical support for both linear and non-linear relationships between temperature and crime.
Conclusions
The aim of the present study was to systematically review the empirical literature on the weather-crime association to characterise the contemporary state of the scholarship. We revealed a longstanding scholarly interest in examining how weather shapes crime that extends more than 150 years. The last 15 years has been defined by a marked growth in the number and diversity of studies on the topic of weather and crime. The increased breadth and depth of studies has been enabled, at least in part, by improved availability of crime and weather data at finer temporal and spatial granularities allied with improved computational capacities. When we consider the first study by Adophe Quetelet ( 1842 ) involved measuring temperature with a handheld thermometer, access to modern barometric instruments, many of which are now readily accessible and some connected into the Internet of Things (IoT), offers unprecedented new capacities to measure, map and monitor different elements of weather at scale (Chapman & Bell, 2018 ). This set alongside the growing repositories of accessible geolocated crime data, often available at the incident level highlights the fruitful opportunities that currently exist for weather-crime studies (see for example, Federal Bureau of Investigation, 2022 ; Tompson et al., 2015 ; Police.uk, 2022 ; Queensland Police Service, 2022 ).
The recent increase in scholarship on weather and crime is also driven, at least in part, by international social and political agendas recognising the widespread implications of climate change and increased frequency and severity of extreme weather events. Given the urgent need to respond to- and prepare for- the social consequences of climate change such as temperature increases, it is likely that the current increasing trend in scholarly attention is set to continue.
Taken together, findings of the weather-crime scholarship demonstrate, on the one hand contextual homogeneity and a need for greater exploration of the weather-crime relationship in cultural and climatic contexts outside the United States and the United Kingdom. Development in this space has started with fervour in the last three to five years and more work in this area is encouraged. On the other hand, current weather-crime scholarship is characterised by empirical inconsistencies and divergence in relation to metrics and definitions. This makes the task of defining a clear narrative about the relationship between temperature and crime a complex one.
The most consistent finding is that warmer temperature is positively associated with violent crime. While 15% (n = 16) of studies on temperature and violence reported a significant curvilinear relationship and thus found support for the Negative Affect Escape (NAE) model, studies do not consistently control for offence time of day. One of the major complexities when examining the association between temperature and violence is accounting for naturally cooler night-time temperature that co-occur when biological and social structures engender the majority of the population to be asleep and therefore not engaged in criminal activity. Thus, studies that do not control for time of day may inadvertently suggest support for the NAE.
All evidence suggests that the weather-crime scholarship will continue to grow however this is set against several important ongoing challenges. Reflecting on Cohn’s ( 1990 ) considerations for weather-crime research namely: (1) theoretical grounding; (2) operational measures of crime and weather (3) temporal granularity, and; (4) statistical techniques, it is clear a number of these issues persist some 30 years later. Reflecting on these four challenges in light of the weather-crime research captured in the current study we propose four contemporary challenges currently impeding weather-crime scholarship. Tackling these four challenges will help advance and coalesce knowledge of the processes the link weather and crime to inform prevention and response strategies. The first two reiterate Cohn’s concerns, the second two identify new challenges that require concerted attention.
Strengthen and integrate theoretical explanations of the weather-crime association
Despite addressing some of the considerations noted by Cohn in her 1990 review of the weather-crime scholarship, theoretical debates about the mechanisms that operate to link weather and crime remain unresolved. This is in part due to lack of consistent empirical evidence that considers the contributory role of weather in crime alongside other key contextual and situational factors including, land use, social-demographic and economic characteristics (Corcoran & Zahnow, 2021 ). Additionally, there is a need to broaden recent theoretic (Miles-Novelo & Anderson, 2019 , 2022 ) and empirical work (Bartlett et al., 2020 ) considering the pathways that might be activated in a changing climate in relation to violence and aggression. To this end, there is unexplored opportunity for an inter-disciplinary fusion of theories to form a Meta theory. To this end future it would be fruitful for future research to consider a dynamic mechanism-based theory of crime and its causes that explicitly accounts for person-environment interactions. Situational action theory (Wikström, 2017 ) represents a step in the right direction given the way in which it integrates multiple factors that operate across a variety of levels and scales [space-time; person-environment].
Modelling multi-dimensional processes of the weather-crime association
Empirically, there are two principal challenges that call for concerted effort to address the units of analyses used in weather-crime analyses and how these are connected to and explained by theory. Much of the early weather-crime studies have tended to employ relatively coarse spatial and temporal units of analyses (Anderson, 1989 ; Bell, 1992, 2005; Bushman et al., 2005 ; Cohn & Rotton, 2000 ; Rotton, 1993)—arguably a product of data availability—and as such are unable to capture the role of individual level factors. Closely aligned with the need to strengthen and integrate theoretical explanations of the weather-crime association [challenge 1] there is an empirical need for the research community to systematically test for the way in which threshold or lags of a particular type or combinations of weather phenomena contribute to elevating criminogenic risk factors. To this end, there is utility in future research considering how certain weather phenomena (with a given tempo, timing, intensity, and duration) that are conditioned by climatic and cultural norms implicate crime opportunity structures. At the individual level rain in certain contexts might have no implications for crime whilst for others it might impact daily routines and impart important implication for crime opportunity structures. To this end we need empirical approaches that more comprehensively measure the social outcomes (as a result of physiological and physiological responses by individuals) from multiple weather phenomena (e.g., rain and heat and humidity) alongside specific extreme types of weather event (e.g. a heat wave or a cold snap) to better understand how meteorological parameters interact with one another and how these are experienced based on individual characteristics.
Broaden the situational, climatic, and cultural contexts of study
There has been a tendency for the weather-crime research to focus on Western contexts that experience temperate climates. Although this situation has begun to shift with more studies appearing in the past five years examining the weather-crime association in less developed nations as well as from contexts located in tropical and sub-tropical climates, much more work is needed to broaden our understanding of the association in different situational, climatic, and cultural contexts. It is only with this broadening of knowledge that the research will be able to talk to the way in which cultural and climatic norms reshape the contours of the weather-crime relationship. To achieve this, future research should build upon the small number of cross-national studies alongside establishing a data sharing platform for crime and weather data to create new opportunities in this space.
Research translation into policy and practice
Despite growing recognition of the importance of evidence-based criminal justice, the translation of research into policy and practice remains poor (Laub & Frisch, 2016 ; Pesta et al., 2019 ). Developing a more complete understanding of the various processes through which practitioners and policy makers draw on research findings to inform policy and practice is essential (Pesta et al., 2019 ).
As we progress our theoretical and empirical understanding of how weather impacts crime across a suite of temporal and spatial scales, situational and cultural context it is essential that this knowledge translates into smart policy and practical outcomes. Practical implications of weather-crime research include informing planners on requirements for built forms that accommodate temperature control due to the impact of heat on human psychological and social disposition and consequent behaviours; or informing city resourcing and policing about how climate change might exacerbate crime in poorer areas that are generally less able to moderate indoor temperatures/weather effects (Browning et al., 2006 ).
Understanding the social implications (such as crime) of weather and weather events, has never been more urgent. As the full impacts of climate change come into fruition, experts predict greater frequency and intensification of extreme weather events such as floods, rain bombs and heat waves set against rises in average daily temperature and sea levels. These weather changes will likely shift crime opportunities and incur strain for individuals and communities by exerting more extreme impacts on citizens’ physiological and psychological discomfort and increasing economic strain (Agnew 2012 ). Coordinated research efforts that seek to advance the four challenges outlined above are required to progress a robust understanding of the weather-crime association that is transferable to practical prevention and response policy outcomes. While not the panacea to solving the weather-crime puzzle, the four challenges offer a starting point to help guide a body of research grounded in social science theory that considers relevant cross-disciplinary influences and is tested through robust comparable approaches to data measurement and modelling. This co-ordinated response will support practical policy responses to help ameliorate negative social outcomes associated with intensifying weather patterns.
Availability of data and materials
All information on which the manuscript is based is contained in the supplementary materials.
This manual process of inclusion involved an examination of the reference lists of the 407 studies included in the full text screening. Additional studies not included in this list were identified and screened for eligibility of which 24 studies were entered in the final set and taken forward for analysis.
As an all-encompassing category.
A total of 4 studies did not clearly specify their spatial unit of analysis.
A total of 31 studies did not explicitly specify their temporal unit of analysis.
The term modelling is employed to capture both times series analyses alongside all forms of regression.
Physiological: Excitation/misattribution of arousal model.
Biological: individual explanations based on capacity for neurological and genetic factors to predispose individuals to crime by influencing impulsivity, inhibition, and susceptibility to physical and environmental stresses e.g., heat/discomfort/changes in routine.
Psychological: Generalised temperature-aggression hypothesis; Negative affect/escape model.
Social: social learning and social control explanations incorporating cultural variations in normalised weather-based activity. For example, socially learned appropriate responses to rain is to reduce outdoor activity. Social control/bonds—individuals with greater stake in conformity will be more likely to comply with social-cultural norms such as not stealing belonging from beach on hot days when individuals are swimming in the ocean.
Situational: Routine activity theory, rational choice, opportunities theories.
Economic: Some cross-over with rational choice theory but rationalisation completely economic based.
This number is derived from a detailed assessment the empirical strategy for each of the included studies.
Afon, A. O., & Badiora, A. I. (2018). The dynamics of crime opportunities: Evidences from weather conditions and spatial pattern of residential neighborhood in Ibadan, Nigeria. Papers in Applied Geography, 4 (1), 1–20. https://doi.org/10.1080/23754931.2017.1346520
Article Google Scholar
Agnew, R. (2012). Dire forecast: A theoretical model of the impact of climate change on crime. Theoretical Criminology, 16(1), 21–42. https://doi.org/10.1177/1362480611416843
Anderson, C. A. (1989). Temperature and aggression: Ubiquitous effects of heat on occurrence of human violence. Psychological Bulletin, 106 (1), 74.
Anderson, C. A., & Anderson, D. C. (1984). Ambient temperature and violent crime: Tests of the linear and curvilinear hypotheses. Journal of Personality and Social Psychology, 46 (1), 91–97. https://doi.org/10.1037/0022-3514.46.1.91
Anderson, C. A., & Anderson, K. B. (1996). Violent crime rate studies in philosophical context: A destructive testing approach to heat and southern culture of violence effects. Journal of Personality and Social Psychology, 70 (4), 740.
Barlett, C. P., DeWitt, C. C., Madison, C. S., Heath, J. B., Maronna, B., & Kirkpatrick, S. M. (2020). Hot temperatures and even hotter tempers: Sociological mediators in the relationship between global climate change and homicide. Psychology of Violence, 10 (1), 1.
Baron, R. A. (1972). Aggression as a function of ambient temperatures and prior anger arousal. Journal of Personality and Social Psychology, 21 , 183–189.
Baron, R. A., & Bell, P. A. (1976). Aggression and heat: The influence of ambient temperature, negative affect, and a cooling drink on physical aggression. Journal of Personality and Social Psychology, 33 , 245–255.
Baron, R. A., & Lawton, S. F. (1972). Environmental influences on aggression: The facilitation of modeling effects by high ambient temperatures. Psychonomic Science, 26 (2), 80–81.
Browning, C. R., Wallace, D., Feinberg, S. L., & Cagney, K. A. (2006). Neighborhood social processes, physical conditions, and disaster-related mortality: The case of the 1995 Chicago heat wave. American Sociological Review, 71 (4), 661–678.
Bushman, B. J., Wang, M. C., & Anderson, C. A. (2005). Is the curve relating temperature to aggression linear or curvilinear? Assaults and temperature in Minneapolis reexamined. Journal of Personality and Social Psychology, 89 (1), 62–66.
Butke, P., & Sheridan, S. C. (2010). An analysis of the relationship between weather and aggressive crime in Cleveland, Ohio. Weather, Climate, and Society, 2 (2), 127–139.
Chapman, L., & Bell, S. J. (2018). High-resolution monitoring of weather impacts on infrastructure networks using the Internet of Things. Bulletin of the American Meteorological Society, 99 (6), 1147–1154.
Cohen, L. E., & Felson, M. (1979). Social change and crime rate trends: A routine activity approach. American Sociological Review., 4 , 588–608.
Cohn, E. G. (1990). Weather and crime. The British Journal of Criminology, 30 (1), 51–64.
Cohn, E. G. (1993). The prediction of police calls for service: The influence of weather and temporal variables on rape and domestic violence. Journal of Environmental Psychology, 13 (1), 71–83.
Cohn, E. G., & Rotton, J. (2000). Weather, seasonal trends and property crimes in Minneapolis, 1987–1988. A moderator-variable time-series analysis of routine activities. Journal of Environmental Psychology, 20 , 257–272.
Cook, M. R., Dawn Emick, M. D., MR, C. F., McCormick, C., & Shapiro, M. (2012). Daily temperature predicts assault and may allow more efficient policing. The American Surgeon, 78 (4), 194.
Corcoran, J., & Zahnow, R. (2021). The Effect of Weather on Assault. Environment and Behavior . https://doi.org/10.1177/00139165211014629
De Freitas, C. R. (1990). Recreation climate assessment. International Journal of Climatology, 10 (1), 89–103.
Dexter, E. G. (1899). Conduct and the weather–an inductive study of the mental effects of definite meterological conditions. Psychological Review, 6 (5), 539–540.
Elliott, J. H., Turner, T., Clavisi, O., et al. (2014). Living systematic reviews: An emerging opportunity to narrow the evidence–practice gap. PLoS Medicine, 11 , 1–6. https://doi.org/10.1371/journal.pmed.1001603
Federal Bureau of Investigation (2022) Federal Bureau of Investigation Crime Data Explorer. Retrieved March 5, 2022 from https://crime-data-explorer.app.cloud.gov/pages/explorer/crime/crime-trend
Field, S. (1992). The effect of temperature on crime. The British Journal of Criminology, 32 (3), 340–351.
Gates, A., Klein, M., Acquaotta, F., Garland, R. M., & Scovronick, N. (2019). Short-term association between ambient temperature and homicide in South Africa: A case-crossover study. Environmental Health, 18 (1), 1–7.
Gough, D. (2015). Qualitative and mixed methods in systematic reviews. Systematic Reviews, 4 , 181. https://doi.org/10.1186/s13643-015-0151-y
Hill, S. A. (1884). The effects of the weather upon death rate and crime in India. Nature (london), 29 (745), 338–340.
Hipp, J. R., Curran, P. J., Bollen, K. A., & Bauer, D. J. (2004). Crimes of opportunity or crimes of emotion? Testing two explanations of seasonal change in crime. Social Forces, 82 (4), 1333–1372.
Hu, X., Chen, P., Huang, H., Sun, T., & Li, D. (2017). Contrasting impacts of heat stress on violent and nonviolent robbery in Beijing, China. Natural Hazards, 87 (2), 961–972.
Laub, J. H., & Frisch, N. E. (2016). Translational criminology: A new path forward. In T. G. Blommrg (Ed.), Advancing criminology and criminal justice policy (pp. 78–88). Routledge.
Google Scholar
LeBeau, J. L., & Corcoran, W. T. (1990). Changes in calls for police service with changes in routine activities and the arrival and passage of weather fronts. Journal of Quantitative Criminology, 6 , 269–291.
LeBeau, J., & Coulson, R. (1996). Routine activities and the spatial-temporal variation of calls for police service: The experience of opposites on the quality of life spectrum. Police Studies, 19 (4), 1–14.
Linning, S. J., Andresen, M. A., Ghaseminejad, A. H., & Brantingham, P. J. (2017). Crime seasonality across multiple jurisdictions in British Columbia, Canada. Canadian Journal of Criminology and Criminal Justice, 59 (2), 251–280.
Mapou, A. E., Shendell, D., Ohman-Strickland, P., Madrigano, J., Meng, Q., Whytlaw, J., & Miller, J. (2017). Environmental factors and fluctuations in daily crime rates. Journal of Environmental Health, 80 (5), 8–22.
Michael, R. P., & Zumpe, D. (1983). Annual rhythms in human violence and sexual aggression in the United States and the role of temperature. Social Biology, 30 (3), 263–278.
Michel, S. J., Wang, H., Selvarajah, S., Canner, J. K., Murrill, M., Chi, A., Efron, D. T., & Schneider, E. B. (2016). Investigating the relationship between weather and violence in Baltimore, Maryland, USA. Injury, 47 (1), 272–276.
Miles-Novelo, A., & Anderson, C. A. (2019). Climate change and psychology: Effects of rapid global warming on violence and aggression. Current Climate Change Reports, 5 (1), 36–46.
Miles-Novelo, A., & Anderson, C. A. (2022). Climate change and human behavior: Impacts of a rapidly changing climate on human aggression and violence . Cambridge University Press.
Book Google Scholar
Moher, D., Liberati, A., Tetzlaff, J., et al. (2009). Preferred reporting items for systematic reviews and meta-analyses: The PRISMA statement. PLoS Medicine . https://doi.org/10.1371/journal.pmed.1000097
Pesta, G. B., Blomberg, T. G., Ramos, J., & Ranson, J. W. (2019). Translational criminology: Toward best practice. American Journal of Criminal Justice, 44 (3), 499–518.
Police.UK. (2022). Data.police.uk. Retrieved March 5, 2022 from https://data.police.uk/
Queensland Police Service. (2022). Queensland Police Service—online crime map. Retrieved March 5, 2022 from https://qps-ocm.s3-ap-southeast-2.amazonaws.com/index.html
Quetelet, L. A. (1842). Of the development of the propensity to crime classics in environmental criminology (pp. 45–92). CRC Press.
Ranson, M. (2014). Crime, weather, and climate change. Journal of Environmental Economics and Management, 67 (3), 274–302.
Rotton, J., & Cohn, E. G. (2000). Violence is a curvilinear function of temperature in Dallas: A replication. Journal of Personality and Social Psychology, 78 (6), 1074.
Schinasi, L. H., & Hamra, G. B. (2017). A time series analysis of associations between daily temperature and crime events in Philadelphia, Pennsylvania. Journal of Urban Health, 94 (6), 892–900.
Sivarajasingam, V., Corcoran, J., Jones, D., Ware, A., & Shepherd, J. (2004). Relations between violence, calendar events and ambient conditions. Injury, 35 (5), 467–473.
Stevens, H. R., Graham, P. L., Beggs, P. J., & Hanigan, I. C. (2021). In cold weather we bark, but in hot weather we bite: Patterns in social media anger, aggressive behavior, and temperature. Environment and Behavior, 53 (7), 787–805.
Tompson, L., Johnson, S., Ashby, M., Perkins, C., & Edwards, P. (2015). UK open source crime data: Accuracy and possibilities for research. Cartography and Geographic Information Science, 42 (2), 97–111.
Wikström, P. O. H. (2017). Crime as alternative: Towards a cross-level situational action theory of crime causation. In J. Mcord (Ed.), Beyond empiricism (pp. 1–37). Routledge.
Download references
Acknowledgements
We wish to acknowledge Dr Fahimeh Khalaj for their assistance in identifying, gathering, and coding the papers that form this systematic review.
This work was supported by Australian Research Council Discovery Project (DP150101293).
Author information
Authors and affiliations.
Queensland Centre for Population Research, School of Earth and Environmental Sciences, The University of Queensland, Brisbane, QLD, 4072, Australia
Jonathan Corcoran
School of Social Sciences, The University of Queensland, Brisbane, QLD, 4072, Australia
Renee Zahnow
You can also search for this author in PubMed Google Scholar
Contributions
Both authors contributed equally to both the research and writing of the manuscript. Both authors read and approved the final manuscript.
Corresponding author
Correspondence to Jonathan Corcoran .
Ethics declarations
Competing interests.
The authors declare that they have no competing interests. We have no known conflict of interest to disclose.
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Supplementary Information
Additional file1: text s1..
PRISMA checklist. Text S2. Full list of included studies in this review. Text S3. Main characteristics of the included studies. Text S4. Weather-crime relationships.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/ . The Creative Commons Public Domain Dedication waiver ( http://creativecommons.org/publicdomain/zero/1.0/ ) applies to the data made available in this article, unless otherwise stated in a credit line to the data.
Reprints and permissions
About this article
Cite this article.
Corcoran, J., Zahnow, R. Weather and crime: a systematic review of the empirical literature. Crime Sci 11 , 16 (2022). https://doi.org/10.1186/s40163-022-00179-8
Download citation
Received : 13 May 2022
Accepted : 28 November 2022
Published : 18 December 2022
DOI : https://doi.org/10.1186/s40163-022-00179-8
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Weather-crime association
Crime Science
ISSN: 2193-7680
- General enquiries: [email protected]
- Skip to Guides Search
- Skip to breadcrumb
- Skip to main content
- Skip to footer
- Skip to chat link
- Report accessibility issues and get help
- Go to Penn Libraries Home
- Go to Franklin catalog
Criminology - Research Guide: Sources for Lit Reviews
- Getting started
- Sources for Lit Reviews
- Gray literature collections
- Crime Rates
- Corrections
- Law Enforcement & Courts
Lit Review Sources
Journals featuring literature reviews.
- Annual Reviews Articles are lengthy literature reviews with BIG bibliographies. Useful for both the text summary and the citations for further reading. Includes Annual Review of Criminology , Annual Review of Law and Social Science and Annual Review of Sociology. HINT! Use the "Advanced Search" link in the upper right corner of the startup window. This permits searching in title, abstract, and keywords only and in specific journals.
- Crime & Justice. 1979- . A journal composed of literature review on criminal justice topics, published annually.
- Annals of the American Academy of Political and Social Science Penn's house journal since 1889, Ann AAPSS publishes single-topic issues six times per year. Recent issues on criminology and criminal justice have been: • Fatal police shootings : patterns, policy, and prevention . Ann AAPSS 687 (January 2020). • Regulating crime : the new criminology of crime control . Ann AAPSS 679 (September 2018). • Migrant smuggling as a collective strategy and insurance policy : views from the margins . Ann AAPSS 676 (March 2018). • The Middle East and regional transition, terrorism, and countering violent extremism : what the next President will face . Ann AAPSS 668 (November 2016). • Tough on crime, tough on families? Criminal justice and family life in America . Ann AAPSS 665 (May 2016). • The great experiment : realigning criminal justice in California and beyond . Ann AAPSS 664 (March 2016).
- Advances in Criminological Theory. 1989- . Print volumes, some e-books. Single-topic volumes.
- Criminal Justice History. 19 vols. 1980-2003. Print only, now ceased. Published by John Jay Press for the Crime and Justice History Group.
- Translational Criminology. 2009- . Published by the Center for Evidence-Based Crime Policy, George Mason University. More a report on current research projects in evidence-based crime policy than a journal of literature reviews.
- Sociology of Crime, Law, and Deviance An ebook series, each volume focused on a specific topic. Recent volumes include Methods of Criminology and Criminal Justice Research; Race, Ethnicity and Law; The Politics of Policing; and Punishment and Incarceration : a Global Perspective.
Best practices and systematic reviews databases
- The Campbell Collaboration See The Campbell Library for published systematic reviews of interventions in crime and justice, as well as social welfare, education, and international development. Campbell systematic reviews also appear in the open-access ejournal, Campbell Systematic Reviews .
- CrimeSolutions.gov / National Institute of Justice Web-based clearinghouse of more than 500 evaluated programs and practices.
- Model Programs Guide / Office of Juvenile Justice & Delinquency Prevention Identifies evidence-based juvenile justice and youth prevention, intervention, and reentry programs. Provides a finely-detailed topics list.
- What Works in Reentry Clearinghouse / Council of State Governments Scores specific reentry programs and practices for beneficial harmful evidence.
- Evidence-based practice online resources / Justice Research and Statistics Association Link list of government, academic, and nonprofit programs.
Dissertations
Every dissertation should include a literature review, to demonstrate how the dissertation fits into the research landscape.
- ProQuest Dissertations and Theses Searches doctoral dissertations, an excellent source for lit reviews.
- NCJRS Abstracts / National Criminal Justice Reference Service. c.1970- . Describes 220,000+ research reports, journal articles, and government documents relating to crime, law enforcement, and the justice system. Many fulltext documents and US Dept of Justice gray literature. HINT! Use the Advanced Search page's "Source Type" filter option for "Literature review", "Best practice/state-of-the-art review", "Issue overview", "Guideline", "Overview text" and other lit review-like genres. HINT! Use the NCJRS Thesaurus to find subject terms.
- Criminal Justice Abstracts with Full Text. 1968- . Abstracts of the scholarly literature and applied literature on criminology and related disciplines. Many citations also include fulltext. Reflects materials received at the Gottfredson Library (formerly Criminal Justice/National Council on Crime and Delinquency Library), Rutgers University Library, Newark.
- Index to Legal Periodicals (Current & Retrospective). 1908- . An excellent tool for tackling the enormous law review, legal yearbook, bar association, and government legal publications literature from the U.S., Canada, U.K., Ireland, Australia, and New Zealand. For foreign legal research, consider using Index to Foreign Legal Periodicals (1985- ).
- Sociological Abstracts. 1963- . From across the field of sociology, useful subject terms include "crime rates," "recidivism," "victim offender relations," and "family violence." . Recently absorbed Social Services Abstracts, adding coverage for social work and social services journals.
- Gray Literature Database. (Gottfredson Library of Criminal Justice, Rutgers Univ.) A supplement to Criminal Justice Abstracts , describing technical reports, working papers, government and agency reports, and conference proceedings - that is, information not commercially published - available online or at the Gottfredson Library. CrimDoc is a similar gray literature database from Univ of Toronto.
- HeinOnline Legal research database containing fulltext documents organized into collections. New collections include Gun Regulation & Legislation in America and History of Capital Punishment.
- PsycINFO. 1887- . Published by American Psychological Association. Comprehensive coverage of the psychological research literature. HINT! The Advanced Search page has a "Methodology" search option filter - select "Literature Review" , "Meta Analysis" , and "Systematic Review" .
Guides and Tips for Writing Literature Reviews
- "How to write a literature review" / Andrew S Denney & Richard Tewksbury Journal of Criminal Justice Education 24, 2 (2013): 218-324 (via HeinOnline).
- "Doing a literature review" / Jeffrey W Knopf PS: Political Science & Politics 39, 1 (January 2006): 127-132 (via Cambridge Journals Online).
- Systematic approaches to a successful literature review / Andrew Booth. (SAGE, 2012) Print only.
- The literature review: a step-by-step guide for students / Diana Ridley. (2nd ed. SAGE, 2012) Print only.
- Preparing Literature Reviews in the Social Sciences (Penn Libraries guide) Needs updating, but still useful for suggestions.
Reference works
Reference works make excellent starting points for research; they provide concise articles on key topics by scholars of the field, often accompanied by suggestions for further reading. The sources listed below are print volumes shelved in the Van Pelt Library Reference Stacks , on the first floor of Van Pelt, unless otherwise noted.
- Compendium of Research on violence against women, 1993-2016. (National Institute of Justice, 2017) Annually-updated reference work describing every NIJ-funded research project on violence against women since 1993.
- ASC Division on Corrections & Sentencing Handbook Series Ebook series sponsored by the American Society of Criminology.
- Elsevier's dictionary of criminal science, in eight languages : English/American, French, Italian, Spanish, Portuguese, Dutch, Swedish, and German. Call Number: Available online Publication Date: Elsevier, 1960
- << Previous: Getting started
- Next: Books >>
- Last Updated: Jul 1, 2024 12:30 PM
- URL: https://guides.library.upenn.edu/criminology
An official website of the United States government
The .gov means it’s official. Federal government websites often end in .gov or .mil. Before sharing sensitive information, make sure you’re on a federal government site.
The site is secure. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely.
- Publications
- Account settings
Preview improvements coming to the PMC website in October 2024. Learn More or Try it out now .
- Advanced Search
- Journal List
- HHS Author Manuscripts

Criminogenic risk assessment: A meta-review and critical analysis
Seth j prins.
1. Columbia University, Departments of Epidemiology and Sociomedical Sciences
2. Columbia University, Department of Sociology
Associated Data
A vast body of research underlies the ascendancy of criminogenic risk assessment, which was developed to predict recidivism. It is unclear, however, whether the empirical evidence supports its expansion across the criminal legal system. This meta-review thus attempts to answer the following questions: 1) How well does criminogenic risk assessment differentiate people who are at high risk of recidivism from those at low risk of recidivism? 2) How well do researchers’ conclusions about (1) match the empirical evidence? 3) Does the empirical evidence support the theory, policy, and practice recommendations that researchers make based on their conclusions? A systematic literature search identified 39 meta-analyses and systematic reviews that met inclusion criteria. Findings from these meta-analyses and systematic reviews are summarized and synthesized, and their interpretations are critically assessed. We find that criminogenic risk assessment’s predictive performance is based on inappropriate statistics, and that conclusions about the evidence are inconsistent and often overstated. Three thematic areas of inferential overreach are identified: contestable inferences from criminalization to criminality, from prediction to explanation, and from prediction to intervention. We conclude by exploring possible reasons for the mismatch between proponents’ conclusions and the evidence, and discuss implications for policy and practice.
Introduction
Over the past 25 years, actuarial risk assessment of criminogenic risk factors has become an “evidence-based” policy and practice in the criminal legal system, strongly promoted within expert circles of policymakers, researchers, and practitioners ( National Institute of Corrections, 2010 ). 1 Criminogenic risk assessment can be defined as (1) the use of statistical methods to predict an individual’s legal system outcomes and categorize them accordingly, purportedly to (2) manage carceral populations through efficient and effective allocation of supervision resources and, ideally, to reduce individuals’ risk through appropriate rehabilitative and social services.
The first part of this definition is about quantifying certain individual characteristics associated with, and often thought to be generative of, illegal behavior. Four of these individual characteristics (a history of antisocial behavior, antisocial personality pattern, antisocial attitudes and cognitions, and antisocial associates), have been consistently associated with recidivism, violence, and other legal system outcomes in almost any sample of people involved in the criminal legal system ( Dowden and Andrews, 1999 ; Gendreau et al., 1996 ; Lipsey and Derzon, 1999 ). The second part of the definition is about intervening on manipulable aspects of these predictors such as attitudes, cognitions, elements of personality, and other “criminogenic” targets. Such efforts can modestly reduce recidivism rates ( Andrews et al., 1990 ; Andrews and Dowden, 2006 ).
A vast body of research underlies the ascendancy of criminogenic risk assessment. As a result of its apparant success, it is moving from the back-end of the criminal legal system, where it was developed to assess the risk of recidivism, to the front-end of the system, in pre-trial processing, sentencing, and policing ( Gottfredson and Moriarty, 2006 ; Lowenkamp and Whetzel, 2009 ; Storey et al., 2014 ; Trujillo and Ross, 2008 ).
The relative success of this approach to risk assessment has been interpreted as evidence that it taps into the causes of “criminal behavior” more generally, and that targeting these factors can therefore also reduce illegal behavior and correctional supervision rates overall. Indeed, an explanatory framework emerged around “the Big Four” antisocial criminogenic risk factors as fundamental to the roots of crime itself, and a model for organizing and applying this knowledge—the risk-need-responsivity model of correctional assessment and rehabilitative programming—is widely accepted and promoted ( Andrews and Bonta, 2010 ; Bonta and Andrews, 2017 ; James, 2018 ; Serin and Lowenkamp, 2015 ).
Yet, with the field’s embrace and promotion of criminogenic risk assessment and the risk-need-responsivity model, its advocates make expansive claims about what it can achieve. Some proponents even argue that risk assessment should characterize the proper function of the criminal legal system itself. For example, Andrews and Bonta (2010) suggest that the prediction of illegal behavior is a central activity of the criminal legal system, because “from it stems community safety, prevention, treatment, ethics, and justice.” In addition to reducing recidivism rates, proponents suggest that the framework might be able to improve sentencing procedures, facilitate jail diversion, reduce prison populations, help scale down mass incarceration without jeopardizing public safety, and ultimately, prevent crime altogether ( Andrews et al., 2011 ; Clement et al., 2011 ; Monahan and Skeem, 2016 ).
The present meta-review interrogates the plausibility of such claims by attempting to answer the following questions:
How well does criminogenic risk assessment differentiate people who are at high risk of recidivism from those at low risk of recidivism?
- How well do researchers’ conclusions about (1) match the empirical evidence?
Does the empirical evidence support the theory, policy, and practice recommendations that researchers make based on their conclusions?
To date, scores of meta-analyses and systematic reviews have attempted to answer the first question, by synthesizing vast amounts of research on the predictive utility and validity of criminogenic risk factors and particular risk assessment instruments. These reviews typically conclude that the evidence supports the continued use and expansion of criminogenic risk assessment. 2 Concurrently, many critics have written about the scientific, cultural, and political forces that brought risk assessment to the forefront in the era of mass incarceration (e.g., Feeley and Simon, 1992 ; Garland, 2003 ), and on the ways in which risk may be gendered and racialized ( Hannah-Moffat, 1999 , 2004 ). However, these critiques have not always engaged directly with the empirical evidence thought to support criminogenic risk assessment, instead challenging the framework’s premises outright.
This division of academic labor means that researchers who largely accept the premises of criminogenic risk assessment have tended to oversee empirical research, its translation to policy and practice, and assessments of its effectiveness. Critics, in turn, have tended to question or dismiss the entire endeavor without directly engaging the empirical evidence on which proponents base their claims. The present study bridges these worlds, approaching the empirical basis of criminogenic risk assessment from a theoretical perspective more skeptical than many of its current proponents.
Our purpose, in sum, is to evaluate whether what the field says about criminogenic risk assessment is consistent with what the evidence says about criminogenic risk assessment. We do this by conducting a meta-review of 39 meta-analyses and systematic reviews of the predictive performance of criminogenic risk factors, with a focus on history of antisocial behavior, antisocial attitudes and cognitions, antisocial personality, and antisocial peers. Our goal is to provide a bird’s eye view of not only the empirical evidence surrounding criminogenic risk assessment, but also how the field understands and interprets that knowledge. This entails that we engage with the literature’s quantitative data and methods, but also that we excavate its tacit theoretical and political assumptions.
A premise of our approach is that the way researchers mobilize concepts, language, and methods to make claims about evidence and practice can reveal hidden ontological and epistemological assumptions, and even contradictions. This is consequential if the widespread acceptance and expansion of criminogenic risk assessment is predicated on the misinterpretation or misuse of the concepts, terms, and methods associated with it. This, in turn, can have a real impact on people’s lives, if scores generated from risk assessments restrict people’s freedom or determine their access to health treatment or other services.
Moreover, we focus primarily on the empirical basis of criminogenic risk assessment, and the field’s interpretation of it, rather than the merits of the risk-need-responsivity model, because the former is prerequisite for certain aspects of the latter. Indeed, the originators of the model acknowledge that criminogenic risk assessment was developed based on a “radical empirical approach to building theoretical understanding” ( Andrews & Bonta, 2010 , p. 132). Although they admit that this approach might be confused with “dustbowl empiricism” ( Andrews & Bonta, 2010 , p. 133), they argue that it nonetheless “lead[s] to a deeper theoretical appreciation of criminal conduct” and is “practically useful in decreasing the human and social costs of crime” ( Andrews & Bonta, 2010 , p. 133). Moreover, while the most recent iteration of the Risk-Need-Responsivity model de-emphasizes prior distinctions between risk factors based on the antisociality construct and others ( Bonta and Andrews, 2017 ), the influence of this psychopathological conceptualization of crime and criminality—as something that emerges from within deviant or abnormal individuals, versus a social relation—looms large, as we shall see below. This meta-review analyzes, assesses, and critiques this logic.
To answer the three questions posed above, we conducted a systematic literature search and review to identify meta-analyses and systematic reviews that examined the predictive utility of criminogenic risk factors. (We will subsequently refer to the meta-analyses and systematic reviews as “reviews,” while we will refer to the primary studies and data sources that constituted those reviews as “primary studies.”) The details of our methods follow.
Inclusion criteria
Reviews were included if they were published in English language journals between 1990 and 2020, focused on a legal system outcome (e.g., recidivism or arrest), and focused on male subjects. We excluded studies of criminogenic risk assessment among women for several interrelated reasons. Sex does not appear to moderate associations between criminogenic risk factors and criminal legal system outcomes ( Singh and Fazel, 2010 ). Yet, it was “…derived from statistical analyses of aggregate male correctional population data and…based on male-derived theories of crime” ( Hannah-Moffat, 2009 : 211), and thus while criminogenic risk assessment may appear to be “gender neutral,” it may nonetheless fail to be gender- responsive ( Hannah-Moffat, 2009 , 2013 ). More recent efforts to incorporate gender-informed variables into the criminogenic risk framework, however, may merely reproduce gender-normative stereotypes and “neutralize gender politics and decontextualize women’s experiences” ( Hannah-Moffat, 2010 : 201). While these issues are critical, they are beyond the scope of the present review.
Search strategy
See the online supplement for search databases and terms. Search results were downloaded into a reference management system, de-duplicated, and titles and meta-data were screened to isolate meta-analyses and systematic reviews. Titles and abstracts of retained reviews were screened based on inclusion criteria to obtain a final sample.
Data extraction and analysis
Meta-data were compiled from the final sample of reviews. Citation information was obtained from Web of Science and Google Scholar. Select characteristics of reviews were tabulated. To answer the first question of this meta-review, we extracted and synthesized quantitative results and researchers’ conclusions and interpretations. To answer the second question, each author of the present meta-review independently rated review conclusions, to determine whether reviews deemed the evidence for the predictive utility of criminogenic risk assessment to be strong, moderate, or weak. Our inter-rater reliability, estimated with Cohen’s kappa, was 0.84, p < 0.01. Ratings reflect consensus scores reached after discussing disagreements. To answer the third question, we make claims based on a close reading of the reviews, from which we identify and examine recurring issues with the concepts, language, and methods mobilized by researchers in this body of work.
Supplemental Figure 1 is a diagram of the flow of information through the meta-review process. The initial search yielded 12,952 records. Articles were retained if their titles or abstracts contained the terms meta-analysis or review . This reduced the number of records to 561. Titles and abstracts of these 561 reviews were read to determine whether they met inclusion criteria. The vast majority were excluded because they did not include a criminal legal system outcome. Thirty-nine meta-analyses or systematic reviews were retained for complete analysis.
Select review characteristics
Table 1 provides a description of retained reviews, and Supplemental Table 1 presents selected information from each, including disaggregated data from Table 1 .
Meta-description of included meta-analyses and systematic reviews
| Meta-description | Bibliometric Analysis | |||
|---|---|---|---|---|
| Studies included in meta-review | 39 | Top 10 references within the reviews | ||
| Unique publications sources | 25 | 10 | ||
| Study type | 8 | |||
| Meta-analysis | 26 | 65 | Andrews & Bonta, 1995 | 8 |
| Meta-regression | 1 | 2.5 | Gendreau et al., 2002 | 8 |
| Meta-review | 1 | 2.5 | 8 | |
| Systematic review | 8 | 20 | 7 | |
| Narrative review | 4 | 10 | 7 | |
| Peer reviewed | 6 | |||
| Yes | 36 | 92.3 | 6 | |
| No | 3 | 7.7 | 8 | |
| Year of publication | Top 10 first authors cited in the reviews | |||
| 1990 – 2000 | 7 | 17.5 | Andrews DA | 91 |
| 2001 – 2010 | 16 | 40 | Bonta J | 33 |
| 2011 – 2020 | 17 | 42.5 | Gendreau P | 31 |
| Unique publication outlets | 24 | Hare RD | 29 | |
| Top 3 publication outlets | Walters GD | 21 | ||
| Criminal Justice & Behavior | 7 | Douglas KS | 14 | |
| Law and Human Behavior | 4 | Harris GT | 13 | |
| Psychological Assessment | 3 | Cooke DJ | 12 | |
| Edens JF | 12 | |||
| Top five most-cited reviews | 3934 | 52.1 | Dowden C | 11 |
| Lipsey & Derzon, 1998 | 1553 | 20.6 | ||
| 827 | 10.9 | |||
| 602 | 8.0 | |||
| Andrews, Bonta, & Wormith, 2006 | 585 | 7.7 | ||
| Leistico et al. 2008 | 367 | 4.9 | ||
| Risk assessment instruments | ||||
| Many | 12 | 30.8 | ||
| Level of Services Inventory | 4 | 10.3 | ||
| Psychopathy Checklist | 8 | 20.5 | ||
| Youth Level of Services Inventory | 1 | 2.6 | ||
| Other | 3 | 7.7 | ||
| Not reported | 11 | 28.2 | ||
| Not applicable | 3 | 7.7 | ||
| Sample characteristics | ||||
| Offenders | 16 | 41.0 | ||
| Juvenile offenders | 7 | 17.9 | ||
| Offenders and community | 10 | 25.6 | ||
| Not reported | 3 | 7.7 | ||
| Not applicable | 3 | 7.7 | ||
| Outcome definition | ||||
| Any recidivism | 13 | 33.3 | ||
| General recidivism | 3 | 7.7 | ||
| Violent recidivism | 3 | 7.7 | ||
| General/violent recidivism | 4 | 10.3 | ||
| Any or violent recidivism | 3 | 7.7 | ||
| Any re-arrest or re-conviction | 3 | 7.7 | ||
| Violent or sexual reoffending | 1 | 2.6 | ||
| Not reported | 6 | 15.4 | ||
| Not applicable | 3 | 7.7 | ||
Note: Percentages are of the 39 studies included in this meta-review unless otherwise noted.
Table 1 shows that the 39 reviews, two-thirds of which were meta-analyses, were published in 25 unique sources. Criminal Justice and Behavior and Law and Human Behavior published the most number of reviews (7 and 4 respectively). The vast majority of reviews were peer-reviewed (N=36, or 92.3%). Those that were not peer reviewed appeared in books or government-sponsored publications.
Collectively, reviews have been cited 7,553 times by other journals, according to Web of Science or Google Scholar. While the plurality of reviews has been cited between one and 20 times, 52.1% of the total citations can be attributed to five high-impact reviews. The plurality of reviews were published between 2011 and 2020.
Samples from primary studies in 84.5% of reviews were drawn from people who were involved with the criminal legal system (either adult or juvenile “offenders”). The outcome investigated by nearly all reviews was recidivism. However, definitions of this construct were heterogeneous: types of recidivism often were not distinguished (i.e., re-arrest, re-conviction, and technical violations were considered the same outcome), or a definition was not provided.
Supplemental Table 1 shows that primary studies from the reviews cover a half-century, from 1965–2020, and sample sizes (of combined participants from primary studies) ranged from roughly 2,400 to nearly 140,000, though many reviews did not report this information.
Thirty-three of the 39 meta-analyses and systematic reviews were available in the Web of Science database, which made it possible to conduct a bibliometric analysis of their complete reference lists. The results of this analysis are presented in the second column of Table 1 , which shows the top 10 cited references and top 10 cited first authors. Andrews (91 citations) and Bonta (33 citations), the creators and owners of the Level of Services Inventory, and their students or frequent co-authors (e.g., Dowden, 11 citations and Gendreau, 31 citations) were among the top-cited authors and were authors of the top-cited references.
Table 2 presents meta-analytic effect size estimates and other predictive performance indicators from the sample of reviews for the four “antisocial” criminogenic risk factors for recidivism. Most reviews reported findings in terms of either weighted point-biserial correlation coefficients or Cohen’s d statistics, both of which were typically referred to as “effect sizes.”
Meta-analytic effect sizes and other performance indicators for criminogenic risk factors and general recidivism
| Study | History of antisocial behavior | Antisocial attitudes | Antisocial personality | Antisocial peers | Demographics | LSI Total | PCL Total | PCL Factor 1 | PCL Factor 2 |
|---|---|---|---|---|---|---|---|---|---|
| Asscher et al., 2011 | 0.32 | 0.37 | 0.42 | ||||||
| 0.5 | 0.51 | 0.56 | 0.17 – 0.42 | ||||||
| Gardner, et al., 2015 | 0.23 – 0.31 | ||||||||
| Gutierrez, et al., 2013 | 0.44 | 0.36 | 0.51 | 0.41 | 0.16 – 0.43 | ||||
| Leistico et al., 2008 | 0.55 | 0.38 | 0.6 | ||||||
| 0.29 – 0.76 | |||||||||
| Wilson & Gutierrez, 2014 | 0.57 | 0.39 | 0.6 | 0.39 | |||||
| 0.08 | 0.07 | 0.12 | |||||||
| Desmarais, Johnson, &Singh | 0.24 – 0.36 | ||||||||
| 5 instruments, 0.22 – 0.32 | |||||||||
| 0.06 – 0.35 | 0.2 | 0.03 – 0.23 | |||||||
| 0.25 | 0.27 | 0.18 | 0.29 | ||||||
| Gendreau, et al., 1992 | 0.22 | 0.16 | 0.19 | 0.27 | 0.06 – 0.18 | ||||
| 0.18 | 0.18 | 0.18 | 0.18 | 0.05 – 0.16 | |||||
| Lipsey & Derzon, 1998 | 0.09 – 0.27 | 0.04 – 0.43 | 0.09 – 0.26 | ||||||
| 0.28 | 0.19 | 0.31 | 0.22 | 0.12 – 0.24 | 0.29 | ||||
| 0.32 | 0.28 | ||||||||
| 0.02 – 0.7 | |||||||||
| 0.32 – 0.4 | |||||||||
| 0.39 – 0.4 | 0.06 – 0.24 | ||||||||
| 0.07 – 0.6 | |||||||||
| Walters, 2012 | Cognitions: 0.2 | ||||||||
| Walters, 2003b | 0.26 | ||||||||
| Walters, 2003a | 0.15 | 0.32 | |||||||
| Kennealy, et al., 2010 | 1.04 | 1.15 | |||||||
| Yu, Geddes, & Fazel, 2012 | 2.4 | ||||||||
| ROC-AUC = 0.66 | |||||||||
| Sensitivity = 0.4 | |||||||||
| Specificity = 0.8 | |||||||||
| Positive Predictive Value = 0.52 | |||||||||
| Negative Predictive Value = 0.76 | |||||||||
| 28 instruments, Mean ROC-AUC = 0.64 | |||||||||
| ROC-AUC = 0.69 | |||||||||
Note. LSI: Level of Services Inventory. PCL: Psychopathy Checklist. Factor 1 represents callous/unemotional/narcissistic. Factor 2 represents antisocial, anger/aggression, impulsivity.
For studies that reported correlation coefficients, the range of mean effect size estimates for history of antisocial behavior was 0.06 – 0.35, for antisocial attitudes 0.16 – 0.2, for antisocial personality 0.18 – 0.31, and for antisocial peers 0.18 – 0.27. The range of estimates for demographic characteristics such as sex, racialized group membership, and education/employment status was 0.05 – 0.26. The magnitude of point-biserial correlations are difficult to interpret because it depends on the coefficient itself and the prevalence of the outcome (an issue we will discuss below). However, a heuristic is that coefficients of 0.1, 0.3, and 0.5 are small, medium, and large, respectively ( Rice and Harris, 2005 ). Thus, reviews tended to find small to medium effect sizes.
Also in Table 2 , for studies that reported weighted mean Cohen’s d , the range of estimates for history of antisocial behavior was 0.32 – 0.57, for antisocial attitudes 0.23 – 0.51, for antisocial personality 0.42 – 0.6, and for antisocial peers 0.39 – 0.41. For demographic characteristics, the range was 0.16 – 0.44. Cohen’s d is easier to interpret, as it does not depend on the prevalence of the outcome. Cohen’s d can be interpreted as the proportion of a standard deviation difference between two groups. Cohen’s heuristic for small, medium, and large effects is 0.2, 0.5, and 0.8, respectively ( Rice and Harris, 2005 ). Reviews reporting Cohen’s d thus tended to find small to medium effect sizes.
Other meta-analyses reported weighted mean estimates for particular instruments overall. Table 2 shows that the correlation coefficient effect size estimates for the Level of Services Inventory ranged from 0.06 – 0.6, and for the Psychopathy Checklist, 0.26 – 0.28. Factor 2 of the Psychopathy Checklist, which measures antisocial characteristics, anger/aggression, and impulsivity, had a stronger effect size (0.29 – 0.32) than Factor 1, which measures callous, unemotional, and narcissistic traits (0.15 – 0.18).
A small number of meta-analyses calculated the mean area under the Receiver Operating Characteristic curve (ROC-AUC). This statistic represents the probability that a randomly chosen individual who has recidivated would be ranked as having higher criminogenic risk than a randomly chosen individual who had not recidivated. Schwalbe (2007) , calculated an ROC-AUC of 0.64 from a meta-analysis of 28 different risk assessment instrument validation studies. Whittington and colleagues (2013) found a mean ROC-AUC of 0.69 from 65 studies. In a meta-analysis of 23 samples using the Level of Services Inventory and the Psychopathy Checklist, Fazel and colleagues (2012) found a mean ROC-AUC for recidivism of 0.66, a sensitivity of 0.4 (the probability that someone was assessed as high-risk given that they recidivated), a specificity of 0.8 (the probability that someone was assessed as low-risk given that they did not recidivate), a positive predictive value of 0.52 (the probability that someone will recidivate given that they were assessed as high-risk), and a negative predictive value of 0.76 (the probability that someone will not recidivate given that they were assessed as low-risk).
Eighteen of the reviews, or roughly 46%, tested for heterogeneity in meta-analytic results as a function of study characteristics such as sample composition (male/female, white/racialized group), study design (cross-sectional, longitudinal), source of risk assessment coding (interview/files), publication status (published/unpublished), etc. In general, these reviews found moderate to high degrees of heterogeneity that were attributable to the above characteristics. Seven reviews, or roughly 18%, discussed the quality of their primary studies. Four of these considered study design to be a proxy for quality, and as a result two included only prospective, longitudinal designs ( Bonta et al., 1998 , 2014 ). Two assessed whether design moderated meta-analytic results. One of these found that design had no effect on results ( Andrews and Dowden, 2006 ), and one found that prospective studies were more likely to obtain statistically significant results than cross-sectional studies ( Whittington et al., 2013 ). One study found that coder-rated quality of the outcome variable was positively associated with effect size ( Lipsey and Derzon, 1999 ). Eight reviews mentioned publication bias and 6 (15%) tested for it, and found that the likelihood of publication bias was low. This is consistent with Singh and Fazel’s (2010) meta-review, which found that only a quarter of reviews assessed for publication bias, which likely biases results in favor of positive significant findings.

How well do conclusions about criminogenic risk assessment’s performance match the empirical evidence?
Supplemental Table 2 paraphrases the primary conclusions of the reviews. Roughly 37% of the reviews concluded that evidence for predictive performance was strong, 37% concluded it was moderate, 13% concluded it was weak or that results should be interpreted cautiously, and 13% did not draw explicit conclusions.
Thus, while over a third of the reviews judged the predictive performance of criminogenic risk assessment to be weak to moderate, over a third of the reviews deemed it to be strong. All but one meta-analysis drew these conclusions based on point-biserial correlations, Cohen’s d , or ROC-AUC. The vast majority relied on the former two statistics, which do not quantify predictive performance.
Measures of “effect” versus measures of prediction/classification.
Most reviews used the language of “effect size” in describing point-biserial correlations or Cohen’s d . This confuses and conflates the language and goals of causal inference with the language and goals of prediction. Moreover, there are a number of major, well-understood problems with the use of point-biserial correlations and Cohen’s d even as measures of effect , including their dependence on the marginal distribution of the independent variable, arbitrary features of study design, and sampling variability (e.g., Cumming, 2013 , 2014 ; Greenland et al., 1986 ).
But one issue in particular warrants further examination: the point-biserial correlation coefficient depends on the prevalence of the outcome, which was frequently not reported in the reviews or the primary studies that constituted them. Of greater concern is that a large number of reviews made conversions among correlation coefficients, Cohen’s d , and ROC-AUC, in order to implement meta-analytic procedures, using methods for this conversion that are sensitive to outcome prevalence. However, these reviews rarely reported the outcome prevalence estimates used in conversions or acknowledged that commonly cited tabular conversion charts assume an outcome prevalence of 50%. Using a 50% prevalence, or base rate, can overestimate the correlation coefficient if the true base rates are lower or higher. This is relevant because a study of nearly 68,000 people released from prisons in 2005, randomly sampled to represent the roughly 401,000 people released from prisons that year in 30 states, found that average recidivism rates are appreciably higher than 50% ( Alper et al., 2018 ). The proportion of people who were re-arrested within three, six, and nine years of release was 68%, 79%, and 83% respectively ( Alper et al., 2018 ).
Supplemental Figure 2 demonstrates the instability of point-biserial correlations converted from Cohen’s d , as a function of outcome prevalence and the magnitude of d . This plot was developed using the standard conversion formula from Rice and Harris (2005) . For various magnitudes of Cohen’s d (curved lines), an outcome prevalence (x-axis) of 50% results in the maximum point-biserial r (y-axis). As outcome prevalence decreases or increases from 50%, the point-biserial r decreases. The potential for serious bias revealed in this figure—that the true magnitudes of correlations are likely lower than reported in the reviews—has been comprehensively discussed in the psychology literature ( McGrath and Meyer, 2006 ).
Even if point-biserial correlation coefficients and Cohen’s d were described and interpreted not as effects, but purely for prediction, they do not convey some important information relevant to answering the first, technical question of this meta-review, about how well criminogenic risk assessment differentiates people who are at high risk of recidivism from those at low risk of recidivism. Only one meta-analysis ( Fazel et al., 2012 ) presented measures that provide this information: sensitivity, specificity, positive predictive value, and negative predictive value. This review found that criminogenic risk assessments were better at identifying people at low risk for recidivism than people at high risk for recidivism, i.e., negative predictive values were high. They argued, however, that positive predictive values were unacceptably low: only 52% of individuals judged to be moderate to high risk went on to commit any offense (virtually equivalent to flipping a coin).
Furthermore, one of the meta-analyses reviewed here found that the Receiver Operator Characteristic curve was defined incorrectly in 27.8% of studies, and the Area Under the Curve statistic was defined in only 34% of studies, and, when it was defined, the definition was incorrect 37.5% percent of the time ( Singh et al., 2013 ). Of greater concern, the estimated Area Under the Curve values were only interpreted in one-third of the studies, and was interpreted accurately in only 12.5% of these.
Thus, while empirical indicators provide relatively consistent magnitudes for the association between criminogenic risk factors and recidivism, the most commonly used statistics do not directly answer the first question regarding criminogenic risk assessment’s ability to distinguish people at high vs. low risk of recidivism. And because the most common statistic—the point-biserial correlation coefficient—is unstable relative to outcome prevalence, even those measures were likely inflated: of the 17 reviews that presented correlation coefficients, only three explicitly stated that they collected information about outcome prevalence from their primary studies. Five others mentioned the issue of sensitivity to outcome prevalence, but did not state whether they had information on true base rates from primary studies or made assumptions about outcome prevalence. The one meta-analysis that reported positive and negative predictive values found that risk assessments were good at correctly identifying people at low risk of recidivism, but virtually no better than chance at identifying people at high risk of recidivism. The technical performance of criminogenic risk assessment has thus been interpreted inconsistently, and arguably inappropriately, by the framework’s proponents.
In this section, we analyze how the reviews talk about risk assessment and illegal behavior more broadly, and assesses whether they make inferences that are supported by the data. Three themes are identified: contestable inferences from criminalization to criminality, contestable inferences from prediction to explanation, and contestable inferences from prediction to intervention.
Contestable inferences from criminalization to criminality.
Reviews tended to conflate exposure to the criminal legal system with illegal behavior . This occurred with both the outcome (recidivism) and predictors (criminogenic risks). For the outcome, reviews tended to conflate the causes of re-arrest, re-conviction, or the revocation of probation or parole with the causes of recidivism resulting from new crimes. Indeed, 50% of reviews used heterogeneous definitions of recidivism or did not report a definition of recidivism. There are two broad categories of situation that can result in recidivism: new illegal offenses and technical violations of the terms of community supervision, e.g., missing an appointment with a parole officer. Most technical violations are not instances of illegal behavior ( Council of State Governments Justice Center, 2019 ), and there is often great discretion among individual community corrections officers and agencies about which technical violations are pursued ( Jones and Kerbs, 2007 ). Thus, incident illegal behavior is sufficient but not necessary for recidivism.
The heterogeneity of recidivism definitions reflects the heterogeneity among risk assessment instruments used to predict recidivism. In their review, Desmarais and colleagues (2016) found that of 19 risk assessment instruments validated in U.S. correctional settings, 31% of validation studies defined recidivism as a new arrest, 13% as re-conviction, 10% as reincarceration, and 4% as technical violations. Importantly, the definition of recidivism influences the predictive performance of risk assessment instruments. For example, the Level of Services Inventory was found to be a valid predictor of recidivism in roughly half as many studies when the definition was re-arrest versus reincarceration ( Vose et al., 2008 ).
Only two of the meta-analyses and systematic reviews acknowledged the difference between exposure to the criminal legal system and illegal behavior. The remainder of the reviews took for granted that legal system outcomes were the result of agential behaviors that emerged from within deviant individuals (e.g., Bonta et al., 2014 ).
Recidivism can be the result of an individual’s own behaviors, the proclivities of their supervision officer, or institutional policies and customs, and the causal mechanisms for recidivism are not uniform across these scenarios. For example, impulsivity may be one of many mechanisms for committing a new robbery, but family or employment problems may be the mechanism for missing a mandated treatment session. And the disposition of a community corrections officer might supersede both of these mechanisms in some circumstances.
As Schwalbe (2008) notes in his review, none of this is important if the goal of criminogenic risk assessment is purely prediction:
As statistical prediction devices, actuarial risk assessments do not assume an underlying causal process related to recidivism. Rather, they count risk factors irrespective of the specific factors that may or may not be present for an individual case. (pp. 1368–1369)
But for explaining crime or illegal behavior, and reducing risk, enumerating the correct mechanisms of recidivism is paramount.
An analogous problem arises with criminogenic predictor constructs, which also conflate illegal behavior with exposure to the criminal legal system. Only two reviews recognized the conceptual and empirical distance between illegal behavior and exposure to the criminal legal system, both within the context of racialized disparities. In the first, Wilson and Gutierrez (2013) compared the predictive ability of the Level of Services Inventory among Aboriginal versus non-Aboriginal “offenders” in Canada, and found effect modification of Aboriginal status and risk score: high-risk Aboriginals and non-Aboriginals had the same probability of recidivism, but low-risk Aboriginals had a higher probability of recidivism than low-risk non-Aboriginals. The authors characterized this finding as an “underclassification” of low-scoring Aboriginals. But a more critical interpretation is that low-risk Aboriginals were subject to a lower threshold of policing, arrest, and sentencing, i.e., they were victims of racialized discrimination. Similarly, in a review of studies that compared risk assessments for ethnic minority and white offenders in the United Kingdom, Raynor and Lewis (2011) found that ethnic minorities consistently had significantly lower risk scores, but received the same sentences as higher-risk white offenders. The authors attributed this finding to racialized discrimination in the British criminal legal system.
Findings such as these reveal that because crime is viewed as emerging from within deviant or abnormal individuals, criminogenic risk assessments struggle to account for distortions in the purported “signal” of individual differences that are in fact due to socio-structural “noise.” In fact, whether or not a person will be re-arrested or re-convicted is influenced by factors that have nothing to do with their criminogenic risk profiles, such as the way the criminal legal system targets their racialized social position.
Indeed, criminogenic risk assessment avoids altogether basic questions about which behaviors are considered crimes and whether behaviors that are deemed criminal are treated differentially across time, space, and groups of people. Story (2016 : 10) clarifies this difference between criminality and criminalization:
While criminality is understood to be a state of objective deviance located in the individual, to be criminalized is to be subjectified as well as subjugated by the coercions of law enforcement and the criminal justice system, both of which are highly malleable relative to changes in laws, policy, and institutional dictates….
The point is not that criminogenic risk instruments may contain racialized, gendered, or other sorts of biases, but rather that, even if they do not, they may still perform unevenly across groups if they attempt to map onto individuals the discriminatory operations of the criminal legal system. Calibrating individual-level risk items for the sole purpose of reducing the uneven performance of risk assessments across racialized groups, as Wilson and Gutierrez (2013) suggest, without addressing structural and institutional sources of discrimination and disparities, thus becomes a normative rather than technical solution. While it might make risk assessments “perform better” in a predictive sense, such recalibration would likely serve to mask, and reproduce, the structural and institutional discrimination that caused the instrument’s underperformance in the first place.
Instead, most reviews implied that the question Why do some people engage in illegal behavior more than others? is the same as the question Why does the criminal legal system target some people more than others? This conflation was sometimes made rather consciously:
The risk principle of case classification relates not to the retributive or deterrent aspects of justice but to the objective of reduced reoffending through rehabilitative programs. Let justice be done and let the just penalty be set, the just obligations be established, and the just decisions be made. The risk principle of human service becomes relevant when, in that just context, interest extends to public protection through the delivery of human services. ( Andrews & Dowden, 2006 , p. 90)
In other words, advocates of criminogenic risk assessment take as a premise that the criminal legal system is just. If there are unjust distortions, they are not the concern of criminogenic risk assessment because they belong to the system as a whole. But if, in practice, risk assessment reflexively reinscribes systemic injustice under a guise of scientific objectivity, the intellectual and moral indifference implied by the above quotation becomes untenable.
Contestable inferences from prediction to explanation.
The outcome in nearly all of the reviews was recidivism, and roughly 74% provided a definition of this outcome. However, many reached conclusions that were not restricted to recidivism, but also to crime or illegal behavior more broadly. As noted above and in Table 1 , 58% of the reviews drew on primary studies that had samples made up exclusively of juvenile and adult “offenders.” Most of these discussed their theoretical orientation and findings in a way that strongly suggested their results tapped into the origins of crime or illegal behavior, and that predictors of recidivism might explain the onset and duration of illegal behavior. For example (emphases added):
GPCSL [General Personality and Cognitive Social Learning theory] proposes that the causes of crime are to be found within the individual and his/her social learning environment. (p. 279)
The general findings of the current meta-analysis are consistent with broad social psychological perspectives of criminal behavior . (p. 138)
The Big Four and Central Eight underpin a general personality and cognitive social learning theory of criminal behavior that provides an explanatory model of the origin and continuation of criminal conduct , and informs methods for predicting, reducing , managing, and preventing criminal behavior. (p. 157)
The LSI was developed from a general personality and social psychological perspective of crime (Andrews & Bonta, 2003), embodied in the Big Four covariates of criminal conduct —antisocial attitudes, antisocial associates, antisocial personality, and a history of antisocial behavior (the constellation is sometimes referred to as the Central Eight, with the inclusion of the needs areas leisure and recreation, family and marital, substance abuse, and employment and education). These covariates are linked to the origin of criminal behavior (and are hence called criminogenic needs), and services directed toward these areas of risk and need might reduce antisocial behavior. (p. 331)
These quotations show that many reviews motivated their analyses with a theory of crime or theory of criminal behavior , although reviews focused on studies of recidivism , in which individuals were already involved in the criminal legal system.
The problem with conflating the predictors, let alone causal explanations, for the onset of illegal behavior or exposure to the legal system with causal explanations for recidivism has long been recognized (e.g., asymmetric causation , Uggen and Piliavin, 1998 ). Yet, few reviews dealt directly with the implications of generalizing from their legal system sampling frames to individuals not involved in the system, and thus made the extension from recidivism to “crime” or onset of illegal behavior without clear intention or justification. One exception is a thoughtful explanation in Cottle and colleagues ( Cottle et al., 2001 ), regarding why their meta-analysis would focus only on recidivism and not initial offending:
It is not feasible to make meaningful assumptions about predictors of reoffending behavior based on predictors found to be associated with first-time delinquency.… …[S]tudies examining recidivism risk factors typically are based on more homogenous samples of adolescents already identified as delinquent. Therefore, variables significantly associated with reoffending behavior in juveniles are not necessarily useful in initially distinguishing between adolescents who will or will not become delinquents.
Nevertheless, slippage from what the evidence says about recidivism prediction to what research says about the onset, duration, and origins of illegal behavior appears in nearly half of the reviews analyzed here.
Contestable inferences from prediction to intervention.
Even if criminogenic risk assessment correctly predicted recidivism, correct prediction does not imply effective intervention; this is true even if predictive risk factors are manipulable ( Greenland, 2005 ; Hernán and VanderWeele, 2011 ; Pearl, 2014 ). Accurately predicting the effects of interventions is not possible without the identification of causal mechanisms ( Schwartz et al., 2016 ). Yet, proponents of criminogenic risk assessment switch from talking about recidivism prediction to talking about recidivism reduction without directly engaging with causation—their emphasis on manipulable risk factors merely assumes it. Below is a sample of quotations that illustrate this question-begging (emphases added):
The importance of these dynamic risk factors is that, in addition to being predictive of criminal behavior, they can serve as targets for treatment programming. Treatments that successfully address these dynamic risk factors or criminogenic needs are associated with reduced recidivism (p. 280)
Changes in dynamic factors achieved through treatment that are subsequently linked to reductions in recidivism are known as criminogenic needs. (p. 243)
Moreover, the design of effective offender treatment programs is highly dependent on knowledge of the predictors of recidivism (p. 575)…Dynamic risk factors, or what Andrews and Bonta commonly refer to as criminogenic needs (e.g., antisocial cognitions, values, and behaviors), are mutable and thus serve as the appropriate targets for treatment (p. 575)
Although the prediction of adult criminal recidivism is important and interesting, some have argued (Douglas & Kropp, 2002), and we concur, that the ultimate purpose of risk assessment should be the prevention as opposed to the prediction of criminal recidivism. (p. 346)
This theory argues that interventions should target for change empirically established predictors of recidivism (such as antisocial peers, antisocial attitudes, and antisocial personality. (p.23)…Given the fact that the LSI includes a number of dynamic items, a reduction in an offender’s total LSI score should occur after the offender has received treatment services appropriate for his or her risk…. (p. 27)
Even if we granted that criminogenic risk assessment’s manipulable risk factors were indeed causal, research evaluating correctional interventions suggests that these ostensibly causal effects do not equal potential intervention effects. While a complete review of the correctional intervention literature is beyond the scope of this analysis, it is worth briefly noting that this literature does not clearly corroborate the causal assumptions in the preceding quotations. Numerous analyses of the effectiveness of interventions that target criminogenic risk factors to reduce recidivism tend to find small to moderate effects and have not confirmed hypotheses about mechanisms of action ( Andrews & Dowden, 2006 ; Lowenkamp et al., 2006 ). In fact, intervention effects are significantly larger when programs are combined with other services, such as mental health counseling, employment and vocational training, and educational programs ( Landenberger and Lipsey, 2005 ). There is very little evidence that recidivism reduction is achieved by reducing “antisocial” criminogenic risk factors per se, rather than more general therapeutic and social service outcomes combined with real improvements in the material conditions of people’s lives. The assumptive transition, then, in many of the reviews analyzed here, from risk prediction to risk reduction, is not supported by the data.
We know a great deal about which individual-level factors are associated with recidivism. However, criminogenic risk assessment 1) does a poor to modest job differentiating among people at high versus low risk, 2) its predictive performance is often misinterpreted and overstated, and 3) many inferences drawn from its empirical evidence base are not supported by the data. Our findings suggest that we know comparatively little about criminogenic risk assessment’s actual predictive performance, in terms of false positives, false negatives, and other metrics derived from these measures. We know even less about how, and to what effect, decisions about sensitivity, specificity, and positive and negative predictive values are implemented and evaluated in the field, only that these metrics are poorly understood by researchers and practitioners in the rare cases they are even considered.
The slippage identified in the preceding sections suggests that the state of evidence does not warrant claims that criminogenic risk assessment’s “theoretical and empirical base…should be disseminated widely for purposes of enhanced crime prevention throughout the criminal legal system and beyond….” ( Andrews et al., 2011 emphasis added). Existing evidence does not speak to its efficacy beyond tertiary prevention. In order for such claims to be evidence-based, the methodological, definitional, and inferential problems discussed above must be systematically addressed. A complete causal model that elaborates the structural- and individual-level antecedents, confounders, and mediators of criminogenic risk factors must be subjected to explicit hypothesis testing in appropriate samples.
One reason this has not already happened may be the radical empirical approach that forms the foundation of criminogenic risk assessment. That is to say, because the theory was developed to fit the data, rather than proposed a priori and subjected to empirical confirmation, competing explanations were not subjected to rigorous hypothesis testing. Other reasons may include prior theoretical commitments and a lack of attention to sample construction and comparison groups. For example, Andrews and Bonta (2010 , pp. 79, 93), have argued that it is a “myth” that the “roots of crime are buried deep in structural inequality.” They go on to cite the results of many of the meta-analyses reviewed here, arguing that social factors such as socioeconomic status are demonstrably weaker predictors of recidivism than criminogenic risk factors. Yet this does not appear to be the case: of the nine studies that provided estimates for so-called “demographic” risk factors, roughly 56% found “effect sizes” equal to or greater than the criminogenic risk factors. Table 2 shows that demographic risk did not perform much worse (and sometimes performed better) than antisocial characteristics in their association with recidivism. This is notable because we would not expect a factor like socioeconomic status to be strongly associated with anything in a sample where it does not vary appreciably, and the vast majority of people targeted by mass criminalization and mass incarceration are low-income.
What might explain the mismatch between the empirical evidence and proponents’ conclusions about it?
Above we have suggested that many researchers seem to overstate the predictive utility of criminogenic risk assessment in relation to the empirical evidence on which they base their claims. One possible explanation for this mismatch is that the authors of these more optimistic reviews may not be neutral arbiters of the studies they examine—both because they are often also the authors of the studies they review, and because they have financial interests in the instruments on which these studies are based. To explore this hypothesis, we conducted a post-hoc bibliometric analysis of all references cited in our sample of reviews with R package Bibliometrix ( Aria and Cuccurullo, 2017 ), as well as a co-citation network analysis of the reviews and their analyzed studies, using R package igraph ( Csardi and Nepusz, 2006 ).
For 35 of the 39 meta-analyses and systematic reviews, authors indicated which references were analyzed as part of review procedures, or provided lists of these primary studies in appendices or supplemental materials . We created a directed network of the relationships between the reviews and their primary studies. Supplemental Figure 3 displays this network in two layouts, with red nodes representing reviews that judged the predictive utility of criminogenic risk factors to be strong, blue nodes representing reviews that judged it to be weak, and grey nodes representing analyzed studies. The size of the grey nodes is proportional to the number of reviews that cite them.
These networks suggest that there are two distinct clusters of reviews, each of which tends to cite a group of primary studies that the other cluster mostly ignores, although there is some overlap. Moreover, each cluster tends to correspond to a different ideological position about the performance of criminogenic risk assessment: those reviews that deem the predictive utility of criminogenic risk factors to be strong tend to co-cite a similar body of studies that is distinct from the studies cited by the reviews that deem the predictive utility of criminogenic risk factors to be weak.
What characterizes the cluster of reviews that are most bullish about the predictive utility of criminogenic risk assessment? One key feature of this cluster of reviews is the involvement of the developers of a particular risk instrument, or their students and frequent collaborators. Andrews, Bonta, Dowden, Gendreau, and Wormith were authors on 73% of the reviews that judged predictive performance to be strong. Three of the five most-cited reviews (overall) included combinations of the Level of Service Inventory’s creators or their students or co-authors.When we restrict the bibliometric sample to the reviews that involve these authors, we find that 17 of the top 20 primary studies cited in those reviews were authored or co-authored by Andrews, Bonta, Dowden, or Gendreau. This degree of self-citation suggests a rather insular field that is largely self-refereed. Furthermore, Andrews, Bonta, and Wormith have a proprietary interest in the Level of Services Inventory and receive royalties on sales of the instrument from its publisher, Multi-Health Systems. Conflicts of interest such as this were disclosed in only two of the nine reviews involving these authors.
Implications for policy and practice
In theory, risk assessment in the criminal legal system might productively be used to focus resources on the people most in need of support and social institutions most in need of change. But it is difficult to imagine how it might live up to this promise without radical changes, from its conceptual underpinnings to its development, implementation, and evaluation. At the very least, as the public begins to take greater notice of criminogenic risk assessment, often opposing it on ethical as well as scientific grounds ( Angwin et al., 2016 ; Barry-Jester et al., 2015 ; Smith, 2016 ), it is incumbent upon researchers to be clear about its scientific versus political content. This is because the perceived empirical superiority of criminogenic risk assessment lends the appearance of scientific objectivity to the selection and prioritization of risk factors, their scoring and weighting, and their tuning and revision, belying the political and value-laden decisions inherent in all data generating and modeling endeavors ( O’Neil, 2016 ).
One way to address the theoretical and empirical overreach demonstrated above might be to democratize and de-privatize criminogenic risk assessment. This would entail: (1) making criminogenic risk assessment instruments open source and free; (2) providing open access to scoring, coding, and statistical modeling procedures; (3) providing open access to de-identified calibration and validation data; and (4) requiring jurisdictions to collect data on, and report, false positives and false negatives.
There should be no profit motive (or paywall blocking access) to the design, dissemination, and evaluation of risk assessments used to make claims about public safety, deprive people of freedom, enable or remove their access to limited treatment and social service resources, or otherwise limit or expand their life chances. In addition to transparency in the constitutive components of risk, the way in which these items are prioritized, weighted, and scored should be public and reproducible. Like certain data stored in the National Archive of Criminal Justice Data, deidentified data collected by jurisdictions using criminogenic risk assessments should be publicly available, with proper privacy protections. Jurisdictions that use criminogenic risk assessments should be required to collect data on and report sensitivity, specificity, positive predictive values, and negative predictive values on a regular basis. While the calibration of these performance measures of course has technical components, the moral and political dimensions of misclassification should be subject to the same public dialogue that informs other jurisprudential and penal norms.
Limitations
The present meta-review is limited in the following ways: First, it is of course possible that there was human error in implementing systematized procedures for screening reviews and extracting data. However, our procedures were designed to minimize this risk. Second, the primary aim of this meta-review was not to quantify a synthesis of findings across reviews, but rather to conduct critical, narrative analysis. Thus, despite being firmly grounded in quantitative methods, this review reflects the subjectivities, inherent biases, conceptual orientation, and political and normative perspectives of the authors. Its findings should thus be understood in that context. Finally, this meta-review is constrained by the methodological deficits of its constituent reviews.
As the criminogenic risk assessment expands at the same time that the criminal legal system slowly inches toward the precipice of reform, it is essential that we are clear about what the evidence does and does not say, in order to resist the hubris of overreach and to prevent the production or reproduction of harmful, unintended consequences. Targeted, strategic, and theory-driven research on the mechanisms of prediction and successful interventions—both individual and structural—is paramount as the field moves forward.
Supplementary Material
Online supplement, acknowledgments.
The authors thank Drs. Sharon Schwartz, Bruce Link, and Lisa Bates for invaluable comments on earlier drafts of this manuscript. SJP also thanks Jennifer Skeem for their participation on his dissertation committee. This work was supported by the National Institute of Mental Health (T32-MH-13043) and National Institute on Drug Abuse (T32-DA-37801 and K01-DA045955).
Seth J. Prins is Assistant Professor of Epidemiology and Sociomedical Sciences at Columbia University. His work concerns the collateral public health consequences of mass incarceration and the school-to-prison pipeline, and how the division and structure of labor influence mental health.
Adam Reich is an Associate Professor of Sociology at Columbia University, and a faculty affiliate at Columbia’s Interdisciplinary Center for Innovative Theory and Empirics (INCITE). He is the author of four books, the most recent of which is Working for Respect: Community and Conflict at Walmart (Columbia, 2018), which he co-authored with Peter Bearman.
1 Not all actuarial risk assessments focus on criminogenic risk factors, and not all criminogenic risk assessments are actuarial. This meta-review, however, concerns the framework of actuarial criminogenic risk assessment.
2 One exception is a collection of meta-analyses and systematic reviews that casts doubt on criminogenic risk assessment’s methodological rigor and predictive utility ( Desmarais et al., 2016 ; Fazel et al., 2012 ; Singh et al., 2013 ; Singh and Fazel, 2010 ). The force of this research, though, is (appropriately) directed at unpacking the first question above, with only cursory attention to the second and third.
* References for all meta-analyses and systematic reviews analyzed in this meta-review are available in the online supplement .
- Alper M, Deruose MR and Markman J (2018) 2018 Update on Prisoner Recidivism: A 9-year Follow-up Period (2005–2014) . NCJ250975, Special Report. Washington, DC: Bureau of Justice Statistics, Office of Justice Programs, U.S. Department of Justice. [ Google Scholar ]
- Andrews DA and Bonta J (2010) The Psychology of Criminal Conduct . 5th ed. Albany, NY: LexisNexis, Anderson Publishing. [ Google Scholar ]
- Andrews DA and Dowden C (2006) Risk principle of case classification in correctional treatment: A meta-analytic investigation. International journal of offender therapy and comparative criminology 50 . SAGE Publications: 88–100. DOI: 10.1177/0306624X05282556. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Andrews DA, Zinger I, Hoge RD, et al. (1990) Does correctional treatment work? A clinically relevant and psychologically informed meta-analysis . Criminology 28 : 369–404. DOI: 10.1111/j.1745-9125.1990.tb01330.x. [ CrossRef ] [ Google Scholar ]
- Andrews DA, Bonta JL, Wormith JS, et al. (2004) LS / CMI Level of Service / Case Management Inventory . Multi-Health Systems: Multi-Health Systems: 1–4. [ Google Scholar ]
- Andrews DA, Bonta J and Wormith JS (2011) The risk-need-responsivity (RNR) model. Does adding the good lives model contribute to effective crime prevention? Criminal Justice and Behavior 38 (7). Sage Publications Ltd.: 735–755. DOI: / 10.1177/0093854811406356. [ CrossRef ] [ Google Scholar ]
- Angwin J, Larson J and Kirchner L (2016) Machine Bias: There’s software used across the country to predict future criminals . And it’s biased against blacks . Available at: https://www.propublica.org/article/machine-bias-risk-assessments-in-criminal-sentencing (accessed 9 July 2019). [ Google Scholar ]
- Aria M and Cuccurullo C (2017) bibliometrix: An R-tool for comprehensive science mapping analysis. Journal of Informetrics 11 (4). Elsevier Ltd: 959–975. DOI: 10.1016/j.joi.2017.08.007. [ CrossRef ] [ Google Scholar ]
- Barry-Jester AM, Casselman B and Goldstein D (2015) Should prison sentences be based on crimes that haven’t been committed yet? Available at: https://fivethirtyeight.com/features/prison-reform-risk-assessment/ (accessed 9 July 2019).
- Bonta J and Andrews D (2017) The Psychology of Criminal Conduct . 6th ed. New York: Routledge. [ Google Scholar ]
- Bonta J, Law M and Hanson K (1998) The prediction of criminal and violent recidivism among mentally disordered offenders: A meta-analysis . Psychological Bulletin 123 ( 2 ): 123–142. [ PubMed ] [ Google Scholar ]
- Bonta J, Blais J and Wilson HA (2014) A theoretically informed meta-analysis of the risk for general and violent recidivism for mentally disordered offenders. Aggression and Violent Behavior 19 . Elsevier BV: 278–287. DOI: 10.1016/j.avb.2014.04.014. [ CrossRef ] [ Google Scholar ]
- Campbell MA, French S and Gendreau P (2009) The Prediction of Violence in Adult Offenders: A Meta-Analytic Comparison of Instruments and Methods of Assessment . Criminal Justice and Behavior 36 ( 6 ): 567–590. DOI: 10.1177/0093854809333610. [ CrossRef ] [ Google Scholar ]
- Clement M, Schwarzfeld M and Thompson M (2011) The national summit on justice reinvestment and public safety: Addressing recidivism, crime, and corrections spending . New York, New York: Council of State Governments Justice Center. [ Google Scholar ]
- Cohen J (1988) Statistical Power Analysis for the Behavioral Sciences . Lawrence Erlbaum Associates. [ Google Scholar ]
- Cottle C, Lee RJ and Heilbrun K (2001) The prediction of criminal recidivism in juveniles . Criminal Justice and Behavior 28 : 367–394. DOI: 10.1177/0093854801028003005. [ CrossRef ] [ Google Scholar ]
- Council of State Governments Justice Center (2019) Confined and Costly: How Supervision Violations are Filling Prisons and Burdening Budgets . New York, New York: Council of State Governments Justice Center. Available at: https://csgjusticecenter.org/wp-content/uploads/2020/01/confined-and-costly.pdf (accessed 28 April 2020). [ Google Scholar ]
- Csardi G and Nepusz T (2006) The igraph software package for complex network research . InterJournal Complex Systems : 1–9. [ Google Scholar ]
- Cumming G (2013) Cohen’s d needs to be readily interpretable: Comment on Shieh (2013) . Behavior Research Methods 45 ( 4 ): 968–971. DOI: 10.3758/s13428-013-0392-4. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Cumming G (2014) The New Statistics: Why and How. Psychological Science 25 (1). SAGE Publications Inc: 7–29. DOI: 10.1177/0956797613504966. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Desmarais SL, Johnson KL and Singh JP (2016) Performance of recidivism risk assessment instruments in U.S. correctional settings . Psychological services 13 : 206–22. DOI: 10.1037/ser0000075. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Dowden C and Andrews DA (1999) What works in young offender treatment: A meta-analysis . Forum on Corrections Research 11 ( 2 ): 21–24. [ Google Scholar ]
- Dowden C and Brown SL (2002) The role of substance abuse factors in predicting recidivism: A meta-analysis. Psychology, Crime & Law 8 (3). United Kingdom: 243–264. [ Google Scholar ]
- Edens JF, Campbell JS and Weir JM (2007) Youth Psychopathy and Criminal Recidivism: A Meta-Analysis of the Psychopathy Checklist Measures. Law and Human Behavior 31 (1). American Psychological Law Society: 53–75. DOI: / 10.1007/s10979-006-9019-y. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Fazel S, Singh JP, Doll H, et al. (2012) Use of risk assessment instruments to predict violence and antisocial behaviour in 73 samples involving 24 827 people: Systematic review and meta-analysis. British Medical Journal 345 . British Medical Journal Publishing Group: e4692–e4692. DOI: 10.1136/bmj.e4692. [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Feeley M and Simon J (1992) The new penology: Notes on the emerging strategy of corrections and its implications . Criminology 30 : 449–474. DOI: 10.1111/j.1745-9125.1992.tb01112.x. [ CrossRef ] [ Google Scholar ]
- Garland D (2003) The Rise of Risk. In: Ericson RV and Doyle A (eds) Risk and Morality . Toronto: University of Toronto Press. [ Google Scholar ]
- Gendreau P, Little T and Goggin C (1996) A meta-analysis of the predictors of adult offender recidivism: What works! Criminology 34 : 575–608. DOI: 10.1111/j.1745-9125.1996.tb01220.x. [ CrossRef ] [ Google Scholar ]
- Gottfredson SD and Moriarty LJ (2006) Statistical Risk Assessment: Old Problems and New Applications. Crime and Delinquency 52 (1). SAGE PUBLICATIONS, INC.: 178–200. DOI: 10.1177/0011128705281748. [ CrossRef ] [ Google Scholar ]
- Greenland S (2005) Epidemiologic measures and policy formulation: lessons from potential outcomes . Emerging themes in epidemiology 2 : 5. DOI: 10.1186/1742-7622-2-5. [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Greenland S, Schlesselman JJ, Criqui MH, et al. (1986) The fallacy of employing standardized regression coefficients and correlations as measures of effect . American journal of epidemiology 123 ( 2 ): 203–208. [ PubMed ] [ Google Scholar ]
- Hannah-Moffat K (1999) Moral Agent or Actuarial Subject:: Risk and Canadian Women’s Imprisonment . Theoretical Criminology 3 ( 1 ): 71–94. DOI: 10.1177/1362480699003001004. [ CrossRef ] [ Google Scholar ]
- Hannah-Moffat K (2004) V. Gendering Risk at What Cost: Negotiations of Gender and Risk in Canadian Women’s Prisons. Feminism & Psychology Andrews BCCCFH-MH-MH-MH-MPRVV (ed.) 14 (2). US: 243–249. DOI: 10.1177/0959353504042178. [ CrossRef ] [ Google Scholar ]
- Hannah-Moffat K (2009) Gridlock or mutability: Reconsidering “gender” and risk assessment . Criminology & Public Policy 8 ( 1 ): 209–219. DOI: 10.1111/j.1745-9133.2009.00549.x. [ CrossRef ] [ Google Scholar ]
- Hannah-Moffat K (2010) Sacrosanctor Flawed:Risk, Accountability and Gender- Responsive Penal Politics . 22 ( 2 ): 25. [ Google Scholar ]
- Hannah-Moffat K (2013) Actuarial sentencing: An “unsettled” proposition. Justice Quarterly 30 . Taylor & Francis: 270–296. DOI: 10.1080/07418825.2012.682603. [ CrossRef ] [ Google Scholar ]
- Harris GT, Rice ME and Quinsey VL (1993) Violent Recidivism of Mentally Disordered Offenders . Criminal Justice and Behavior 20 ( 4 ): 315–335. DOI: 10.1177/0093854893020004001. [ CrossRef ] [ Google Scholar ]
- Hernán MA and VanderWeele TJ (2011) Compound treatments and transportability of causal inference . Epidemiology (Cambridge, Mass.) 22 ( 3 ): 368–377. DOI: 10.1097/EDE.0b013e3182109296. [ PMC free article ] [ PubMed ] [ CrossRef ] [ Google Scholar ]
- James N (2018) Risk and Needs Assessment in the Federal Prison System . 7–5700 R44087. Washington, DC: Congressional Research Service. [ Google Scholar ]
- Jones M and Kerbs JJ (2007) Probation and Parole Officers and Discretionary Decision-Making: Responses to Technical and Criminal Violations . Federal Probation; 71 (1): 9–15. [ Google Scholar ]
- Landenberger N a. and Lipsey MW (2005) The positive effects of cognitive–behavioral programs for offenders: A meta-analysis of factors associated with effective treatment . Journal of Experimental Criminology 1 ( 4 ): 451–476. DOI: 10.1007/s11292-005-3541-7. [ CrossRef ] [ Google Scholar ]
- Leistico A-MR, Salekin RT, DeCoster J, et al. (2008) A large-scale meta-analysis relating the Hare measures of psychopathy to antisocial conduct. Law and Human Behavior 32 (1). American Psychological Law Society: 28–45. DOI: 10.1007/s10979-007-9096-6. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Lipsey MW and Derzon JH (1999) Predictors of Violent or Serious Delinquency in Adolescence and Early Adulthood: A Synthesis of Longitudinal Research. In: Loeber R and Farrington D (eds) Serious & Violent Juvenile Offenders: Risk Factors and Successful Interventions . Thousand Oaks: SAGE Publications Ltd, pp. 86–105. DOI: 10.4135/9781452243740. [ CrossRef ] [ Google Scholar ]
- Lowenkamp CT and Whetzel J (2009) The development of an actuarial risk assessment instrument for u.s. pretrial services . Federal Probation 73 ( 2 ): 33–36. [ Google Scholar ]
- Lowenkamp CT, Latessa EJ and Smith P (2006) Does correctional program quality really matter? The impact of adhering to the principles of effective intervention . Criminology Public Policy 5 : 575–594. DOI: 10.1111/j.1745-9133.2006.00388.x. [ CrossRef ] [ Google Scholar ]
- McGrath RE and Meyer GJ (2006) When effect sizes disagree: the case of r and d . Psychological Methods 11 ( 4 ): 386–401. DOI: 10.1037/1082-989X.11.4.386. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Mokros A, Vohs K and Habermeyer E (2014) Psychopathy and violent reoffending in German-speaking countries: A meta-analysis . European Journal of Psychological Assessment 30 ( 2 ): 117. DOI: 10.1027/1015-5759/a000178. [ CrossRef ] [ Google Scholar ]
- Monahan J and Skeem JL (2016) Risk assessment in criminal sentencing. Annual Review of Clinical Psychology 12 . United States: 489–513. DOI: 10.1146/annurev-clinpsy-021815-092945. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- National Institute of Corrections (2010) A framework for evidence-based decision making in local criminal justice systems . Washington DC: Prepared for the National Institute of Corrections by the Center for Effective Public Policy, Pretrial Justice Institute, Justice Management Institute, and The Carey Group. [ Google Scholar ]
- Olver ME, Stockdale KC and Wormith JS (2009) Risk assessment with young offenders: A meta-analysis of three assessment measures . Criminal Justice and Behavior 36 ( 4 ): 329–353. DOI: 10.1177/0093854809331457. [ CrossRef ] [ Google Scholar ]
- Olver ME, Stockdale KC and Wormith JS (2014) Thirty years of research on the Level of Service scales: A meta-analytic examination of predictive accuracy and sources of variability . Psychological Assessment 26 : 156–176. DOI: 10.1037/a0035080. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- O’Neil C (2016) Weapons of Math Destruction: How Big Data Increases Inequality and Threatens Democracy . New York: Crown Books. [ Google Scholar ]
- Pearl J (2014) Is Scientific Knowledge Useful for Policy Analysis? A Peculiar Theorem Says: No . Journal of Causal Inference 2 ( 1 ): 109–112. DOI: 10.1515/jci-2014-0017. [ CrossRef ] [ Google Scholar ]
- Pusch N and Holtfreter K (2018) Gender and Risk Assessment in Juvenile Offenders: A Meta-Analysis . Criminal Justice and Behavior 45 ( 1 ): 56–81. DOI: 10.1177/0093854817721720. [ CrossRef ] [ Google Scholar ]
- Raynor P and Lewis S (2011) Risk-need Assessment, Sentencing and Minority Ethnic Offenders in Britain. The British Journal of Social Work 41 (7). Oxford University Press, Oxford UK: 1357–1371. DOI: / 10.1093/bjsw/bcr111. [ CrossRef ] [ Google Scholar ]
- Rice ME and Harris GT (2005) Comparing effect sizes in follow-up studies: ROC Area, Cohen’s d, and r . Law and human behavior 29 ( 5 ): 615–620. DOI: 10.1007/s10979-005-6832-7. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Schwalbe CS (2007) Risk Assessment for Juvenile Justice: A Meta-Analysis. Law and Human Behavior 31 (5). Springer Science+Business Media Inc, New York NY: 449–462. DOI: / 10.1007/s10979-006-9071-7. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Schwalbe CS (2008) A Meta-Analysis of Juvenile Justice Risk Assessment Instruments. Predictive Validity by Gender. Criminal Justice and Behavior 35 (11). Sage Publications Ltd.: 1367–1381. DOI: / 10.1177/0093854808324377. [ CrossRef ] [ Google Scholar ]
- Schwartz S, Gatto NM and Campbell UB (2016) Causal identification: a charge of epidemiology in danger of marginalization. Annals of Epidemiology 26 (10). Elsevier Inc: 669–673. DOI: 10.1016/j.annepidem.2016.03.013. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Serin RC and Lowenkamp CT (2015) Selecting and Using Risk and Need Assessments. Drug Court Practitioner Fact Sheet Vol. X No. 1. National Drug Court Institute. [ Google Scholar ]
- Simourd L and Andrews DA (1994) Correlates of Delinquency: A Look at Gender Differences . Forum on Corrections Research 6 ( 1 ): 26–31. [ Google Scholar ]
- Singh JP and Fazel S (2010) Forensic risk assessment. Criminal Justice and Behavior 37 . SAGE PUBLICATIONS, INC.: 965–988. DOI: 10.1177/0093854810374274. [ CrossRef ] [ Google Scholar ]
- Singh JP, Desmarais SL and Van Dorn RA (2013) Measurement of Predictive Validity in Violence Risk Assessment Studies: A Second-Order Systematic Review. Behavioral Sciences and the Law 31 (1). Wiley Subscription Services, Inc.: 55–73. DOI: 10.1002/bsl.2053. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Smith M (2016) In Wisconsin, a Backlash Against Using Data to Foretell Defendants’ Futures . New York Times , 22 June . Available at: https://nyti.ms/2mAxdm2 .
- Storey JE, Kropp PR, Hart SD, et al. (2014) Assessment and management of risk for intimate partner violence by police officers using the brief spousal assault form for the evaluation of risk. Criminal Justice and Behavior 41 . SAGE Publications: 256–271. DOI: 10.1177/0093854813503960. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Story B (2016) The prison in the city: Tracking the neoliberal life of the ‘million dollar block’ . Theoretical Criminology . DOI: 10.1177/1362480615625764. [ CrossRef ] [ Google Scholar ]
- Trujillo MP and Ross S (2008) Police Response to Domestic Violence. Journal of Interpersonal Violence 23 (4). SAGE Publications: 454–473. DOI: 10.1177/0886260507312943. [ PubMed ] [ CrossRef ] [ Google Scholar ]
- Uggen C and Piliavin I (1998) Asymmetrical Causation and Criminal Desistance . Journal of Criminal Law and Criminology 88 ( 4 ): 1399–1422. [ Google Scholar ]
- Vose B, Cullen FT and Smith P (2008) The empirical status of the Level of Service Inventory. Federal Probation 72 (3). Administrative Office of the United States Courts: 22–29. [ Google Scholar ]
- Whittington R, Hockenhull JC, McGuire J, et al. (2013) A systematic review of risk assessment strategies for populations at high risk of engaging in violent behaviour: update 2002–8. Health technology assessment (Winchester, England) 17 (50). Whittington,R. Health and Community Care Research Unit, University of Liverpool, Liverpool, UK.: i–128. [ PMC free article ] [ PubMed ] [ Google Scholar ]
- Wilson HA and Gutierrez L (2013) Does One Size Fit All?: A Meta-Analysis Examining the Predictive Ability of the Level of Service Inventory (LSI) With Aboriginal Offenders . Criminal Justice and Behavior 41 ( 2 ): 196–219. DOI: 10.1177/0093854813500958. [ CrossRef ] [ Google Scholar ]
A systematic review of crime facilitated by the consumer Internet of Things
- Original Article
- Published: 15 October 2019
- Volume 34 , pages 97–125, ( 2021 )
Cite this article

- John M. Blythe 1 &
- Shane D. Johnson 1
2278 Accesses
22 Citations
23 Altmetric
Explore all metrics
The nature of crime is changing—estimates suggest that at least half of all crime is now committed online. Once everyday objects (e.g. televisions, baby monitors, door locks) that are now internet connected, collectively referred to as the Internet of Things (IoT), have the potential to transform society, but this increase in connectivity may generate new crime opportunities. Here, we conducted a systematic review to inform understanding of these risks. We identify a number of high-level mechanisms through which offenders may exploit the consumer IoT including profiling, physical access control and the control of device audio/visual outputs. The types of crimes identified that could be facilitated by the IoT were wide ranging and included burglary, stalking, and sex crimes through to state level crimes including political subjugation. Our review suggests that the IoT presents substantial new opportunities for offending and intervention is needed now to prevent an IoT crime harvest.
This is a preview of subscription content, log in via an institution to check access.
Access this article
Subscribe and save.
- Get 10 units per month
- Download Article/Chapter or eBook
- 1 Unit = 1 Article or 1 Chapter
- Cancel anytime
Price includes VAT (Russian Federation)
Instant access to the full article PDF.
Rent this article via DeepDyve
Institutional subscriptions

Similar content being viewed by others

Identifying Security Challenges in the IoT for the Public Sector: A Systematic Review

Legal/Regulatory Issues for MMBD in IoT

The Internet of Things: Opportunities, Challenges, and Social Implications of an Emerging Paradigm
Explore related subjects.
- Artificial Intelligence
In computer science, conference papers undergo a rigorous peer-review process.
Due to page constraints, only example citations are included in the text. More details of the full set of papers reviewed can be found in the electronic supplementary material.
To be clear, we only used additional references not identified through the systematic search to provide further context about crimes identified through the systematic search.
Agadakos, I., C.-Y. Chen, M. Campanelli, P. Anantharaman, M. Hasan, B. Copos, et al. 2017. Jumping the Air Gap: Modeling Cyber-Physical Attack Paths in the Internet-of-Things. In CPS-SPC’17 , Vol. 17.
Aktypi, A., J.R.C. Nurse, and M. Goldsmith. 2017. Unwinding Ariadne’s Identity Thread: Privacy Risks with Fitness Trackers and Online Social Networks. In Proceedings of the 2017 on Multimedia Privacy and Security , 1–11. Dallas, TX, USA.
Aljosha, J., U. Johanna, M. Georg, V.G. Artemios, and W. Edgar. 2017. Lightweight Address Hopping for Defending the IPv6 IoT. In Proceedings of the 12th International Conference on Availability, Reliability and Security — ARES’17 , 1–10.
Amin, S.M., and A.M. Giacomoni. 2012. Smart Grid-Safe, Secure, Self-Healing. IEEE Power & Energy Magazine 10: 33–40.
Article Google Scholar
Anand, S.A., and N. Saxena. 2016. Vibreaker: Securing Vibrational Pairing with Deliberate Acoustic Noise. In Proceedings of the 9th ACM Conference on Security & Privacy in Wireless and Mobile Networks , 103–108.
Bachy, Y., F. Basse, V. Nicomette, E. Alata, M. Kaaniche, J.C. Courrege, and P. Lukjanenko. 2015. Smart-TV Security Analysis: Practical Experiments. In Proceedings of the 45th Annual IEEE/IFIP International Conference on Dependable Systems and Networks Smart - TV , 497–504.
Badenhop, C.W., B.W. Ramsey, B.E. Mullins, and L.O. Mailloux. 2016. Extraction and Analysis of Non-volatile Memory of the ZW0301 Module, a Z-Wave Transceiver. Digital Investigation 17: 14–27.
Banafa, A. 2016. Internet of Things (IoT): Security, Privacy and Safety. https://datafloq.com/read/internet-of-things-iot-security-privacy-safety/948 .
BBC News. 2017a. EU Clamps Down on Social Media Job Snoops. https://www.bbc.co.uk/news/technology-40592516 .
BBC News. 2017b. Man Jailed for Hacking into Jennifer Lawrence’s Online Account. http://www.bbc.co.uk/newsbeat/article/38741309/man-jailed-for-hacking-into-jennifer-lawrences-online-account .
BBC News. 2018. West Midlands PCC Calls Car Security Summit. http://www.bbc.co.uk/news/uk-england-birmingham-43737877 .
Blythe, J.M., and L. Coventry. 2018. Costly But Effective: Comparing the Factors that Influence Employee Anti-malware Behaviours. Computers in Human Behavior 87: 87–97.
Blythe, J.M., and S.D. Johnson. 2018. Rapid Evidence Assessment on Labelling Schemes and Implications for Consumer IoT Security. DCMS: London. https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/747296/Rapid_evidence_assessment_IoT_security_oct_2018.pdf .
Blythe, J.M., S. Michie, J. Watson, and C.E. Lefevre. 2017. Internet of Things in Healthcare: Identifying Key Malicious Threats, End-User Protective and Problematic Behaviours. In Proceedings of the 3rd Digital Health Conference 2017, London, UK.
Blythe, J.M., N. Sombatruang, and S.D. Johnson. 2019. What Security Features and Crime Prevention Advice is Communicated in Consumer IoT Device Manuals and Support Pages? Journal of Cybersecurity 5 (1).
Bugeja, J., A. Jacobsson, and P. Davidsson. 2017. An analysis of malicious threat agents for the smart connected home. In 2017 IEEE International Conference on Pervasive Computing and Communications Workshops, PerCom Workshops 2017 , 557–562.
Byrt, T., J. Bishop, and J. Carlin. 1993. Bias, Prevalence and Kappa. Journal of Clinical Epidemiology 46 (5): 423–429.
Chen, D., S. Kalra, D. Irwin, P. Shenoy, and J. Albrecht. 2015. Preventing Occupancy Detection from Smart Meter Data. IEEE Transactions on Smart Grid 6 (5): 2426–2434.
Chen, Y., and B. Luo. 2012. S2A: Secure Smart Household Appliances. In Proceedings of the second ACM conference on Data and Application Security and Privacy , 217–228.
CIPD. 2013. Pre - employment Checks: An Employer’s Guide . http://www.cipd.co.uk/binaries/pre-employment-checks_2013.pdf .
Clarke, R.V. 1980. Situational Crime Prevention: Theory and Practice. The British Journal of Criminology 20: 136.
Clarke, R.V. 1995. Situational Crime Prevention. Crime and Justice 19: 91–150.
Cockbain, E., K. Bowers, and G. Dimitrova. 2018. Human Trafficking for Labour Exploitation: The Results of a Two-Phase Systematic Review Mapping the European Evidence Base and Synthesising Key Scientific Research Evidence. Journal of Experimental Criminology 14 (3): 319–360.
Coleman, F.L. 1997. Stalking Behavior and the Cycle of Domestic Violence. Journal of Interpersonal Violence 12 (3): 420–432.
College of Policing. 2018. Crime Reduction Toolkit. http://whatworks.college.police.uk/toolkit/Pages/Toolkit.aspx .
Copos, B., K. Levitt, M. Bishop, and J. Rowe. 2016. Is Anybody Home? Inferring Activity from Smart Home Network Traffic. In IEEE Security and Privacy Workshops (SPW) , 245–251.
Coppolino, L., V. Dalessandro, S. Dantonio, L. Levy, and L. Romano. 2015. My Smart Home is Under Attack. In IEEE 18th International Conference on Computational Science and Engineering , 145–151.
Coventry, L., P. Briggs, J.M. Blythe, and M. Tran. 2014. Using Behavioural Insights to Improve the Public’ S Use of Cyber Security Best Practices . Innovation and Skills: Report for the Department of Business.
Google Scholar
DCMS. 2018. Secure by Design: Improving the Cyber Security of Consumer Internet of Things Report . https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/686089/Secure_by_Design_Report_.pdf .
Denning, T., C. Matuszek, K. Koscher, J.R. Smith, and T. Kohno. 2009. A Spotlight on Security and Privacy Risks with Future Household Robots. In Proceedings of the 11th International Conference on Ubiquitous Computing , 105–114. ACM.
Felson, M. 1994. Crime and Everyday Life . Thousand Oaks, CA: Pine Forge.
Feng, X., M. Ye, V. Swaminathan, and S. Wei. 2017. Towards the Security of Motion Detection-based Video Surveillance on IoT Devices. In Proceedings of the on Thematic Workshops of ACM Multimedia 2017 , 228–235. ACM.
Fernandes, E., J. Jung, and A. Prakash. 2016. Security Analysis of Emerging Smart Home Applications. In IEEE Symposium on Security and Privacy Security , 636–654.
Fernandes, E., A. Rahmati, J. Jung, and A. Prakash. 2017. Security Implications of Permission Models in Smart-Home Application Frameworks. IEEE Security and Privacy 15 (2): 24–30.
Forrester, D., M. Chatterton, K. Pease, and R. Brown. 1988. The Kirkholt Burglary Prevention Project .
FTC. 2015. IoT Privacy & Security in a Connected World . https://www.ftc.gov/system/files/documents/reports/federal-trade-commission-staff-report-november-2013-workshop-entitled-internet-things-privacy/150127iotrpt.pdf .
Garcia-Morchon, O., S. Kumar, S. Keoh, R. Hummen, and R. Struik. 2014. Security Considerations in the IP - Based Internet of Things. Draft - Garcia - Core - Security - 06 . https://tools.ietf.org/html/garcia-core-security-03.txt .
Greensmith, J. 2015. Securing the Internet of Things with Responsive Artificial Immune Systems. In Proceedings of the 2015 Annual Conference on Genetic and Evolutionary Computation , 113–120.
Henry, N., and A. Powell. 2015. Beyond the ‘Sext’: Technology-Facilitated Sexual Violence and Harassment Against Adult Women. Australian & New Zealand Journal of Criminology 48 (1): 104–118.
Higgins, J., and S. Green. 2011. Cochrane Handbook for Systematic Reviews of Interventions .
Ho, G., D. Leung, P. Mishra, A. Hosseini, D. Song, and D. Wagner. 2016. Smart Locks: Lessons for Securing Commodity Internet of Things Devices. In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security , 461–472.
Hoang, N.P., and D. Pishva. 2015. A TOR-Based Anonymous Communication Approach to Secure Smart Home Appliances. In International Conference on Advanced Communication Technology, ICACT , Vol. 3, 517–525.
Hong, J. 2012. The State of Phishing Attacks. Communications of the ACM 55 (1): 74–81.
Jacobsson, A., M. Boldt, and B. Carlsson. 2016. A Risk Analysis of a Smart Home Automation System. Future Generation Computer Systems 56: 719–733.
Johnson, S.D., N. Tilley, and K.J. Bowers. 2015. Introducing EMMIE: An Evidence Rating Scale to Encourage Mixed-Method Crime Prevention Synthesis Reviews. Journal of Experimental Criminology 11 (3): 459–473.
Kang, W.M., S.Y. Moon, and J.H. Park. 2017. An Enhanced Security Framework for Home Appliances in Smart Home. Human-Centric Computing and Information Sciences 7 (1): 6.
Kaspersky. 2017. Kaspersky Lab Research Reveals the Cost and Profitability of Arranging a DDoS Attack. https://usa.kaspersky.com/about/press-releases/2017_kaspersky-lab-research-reveals-the-cost-and-profitability-of-arranging-a-ddos-attack .
Kumar, P., M. Ylianttila, A. Gurtov, S.G. Lee, and H.J. Lee. 2014. An Efficient and Adaptive Mutual Authentication Framework for Heterogeneous Wireless Sensor Network-Based Applications. Sensors 14 (2): 2732–2755.
Laxton, C. 2014. Virtual World, Real Fear: Women’s Aid Report into Online Abuse, Harassment and Stalking . Bristol: Women’s Aid.
Laycock, G. 2004. The UK Car Theft Index: An Example of Government Leverage. In Understanding and Preventing Car Theft, Vol. 17 of Crime Prevention Studies , 25–44. Willan: Cullompton.
Lee, M., K. Lee, J. Shim, S. Cho, and J. Choi. 2016. Security Threat on Wearable Services: Empirical Study Using a Commercial Smartband. In 2016 IEEE International Conference on Consumer Electronics - Asia (ICCE - Asia) , 1–5.
Liu, Y., S. Hu, and T.Y. Ho. 2015a. Vulnerability Assessment and Defense Technology for Smart Home Cybersecurity Considering Pricing Cyberattacks. In: IEEE/ACM International Conference on Computer - Aided Design , 183–190.
Liu, X., Z. Zhou, W. Diao, Z. Li, and K. Zhang. 2015b. When Good Becomes Evil: Keystroke Inference with Smartwatch. In Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security — CCS’15 , 1273–1285.
Lo, C.H., and N. Ansari. 2013. CONSUMER: A Novel Hybrid Intrusion Detection System for Distribution Networks in Smart Grid. IEEE Transactions on Emerging Topics in Computing 1 (1): 33–44.
Lotfy, K., and M.L. Hale. 2016. Assessing Pairing and Data Exchange Mechanism Security in the Wearable Internet of Things. In 2016 IEEE International Conference on Mobile Services (MS) , 25–32.
Lyu, M., D. Sherratt, A. Sivanathan, H.H. Gharakheili, A. Radford, and V. Sivaraman. 2017. Quantifying the Reflective DDoS Attack Capability of Household IoT Devices. In Proceedings of the 10th ACM Conference on Security and Privacy in Wireless and Mobile Networks — WiSec’17 , 46–51.
Mailley, J., R. Garcia, S. Whitehead, and G. Farrell. 2008. Phone Theft Index. Security Journal 21 (3): 212–227.
Maiti, A., M. Jadliwala, J. He, and I. Bilogrevic. 2015. (Smart)Watch Your Taps: Side-Channel Keystroke Inference Attacks using Smartwatches. In Proceedings of the 2015 ACM International Symposium on Wearable Computers — ISWC’15 , 27–30. New York: ACM Press.
Manky, D. 2013. Cybercrime as a Service: a Very Modern Business. Computer Fraud & Security 6: 9–13.
Maple, C. 2017. Security and Privacy in the Internet of Things. Journal of Cyber Policy 2 (2): 155–184.
Metropolitan Police. 2003. Findings from the Multi- agency Domestic Violence Murder Reviews in London. https://paladinservice.co.uk/wp-content/uploads/2013/07/Findings-from-the-Domestic-Homicide-Reviews.pdf .
Min, B., and V. Varadharajan. 2015. Design and Evaluation of Feature Distributed Malware Attacks Against the Internet of Things (IoT). In 20th International Conference on Engineering of Complex Computer Systems (ICECCS) , 80–89
Mitchell, K., D. Finkelhor, L. Jones, and J. Wolak. 2010. Use of Social Networking Sites in Online Sex Crimes Against Minors: An Examination of National Incidence and Means of Utilization. Journal of Adolescent Health 47 (2): 183–190.
Mitnick, K.D., and W.L. Simon. 2003. The Art of Deception: Controlling the Human Element in Security . New York: Wiley.
NPower. 2018. Energy Theft. https://www.npower.com/home/help-and-support/meter-readings/meter-tampering/ .
NSPCC. 2018. Facebook Tops List of Sites Used for Online Grooming. https://www.nspcc.org.uk/what-we-do/news-opinion/Facebook-tops-list-online-grooming/ .
Obermaier, J., and M. Hutle. 2016. Analyzing the Security and Privacy of Cloud-Based Video Surveillance Systems. In Proceedings of the 2nd ACM International Workshop on IoT Privacy, Trust, and Security — IoTPTS’16 , 22–28. New York: ACM Press.
Office for National Statistics. 2017a. Crime in England and Wales: Year Ending December 2017 . London: ONS.
Office for National Statistics. 2017b. Overview of Burglary and Other Household Theft: England and Wales . London: ONS.
Oluwafemi, T., T. Kohno, S. Gupta, and S. Patel. 2013a. Experimental Security Analyses of Non-Networked Compact Fluorescent Lamps: A Case Study of Home Automation Security. In Proceedings of the LASER 2013 (LASER 2013) , 13–24. https://www.usenix.org/laser2013/program/oluwafemi .
Oluwafemi, T., T. Kohno, S. Gupta, and S. Patel. 2013b. Experimental Security Analyses of Non-Networked Compact Fluorescent Lamps: A Case Study of Home Automation Security. In Proceedings of the LASER 2013 (LASER 2013) , 13–24.
Paladin. 2018. Paladin’s Definition of Stalking. https://paladinservice.co.uk/ .
Pawson, R.A.Y., and N. Tilley. 2018. What Works in Evaluation Research? The British Journal of Criminology 34 (3): 291–306.
Pease, K. 1997. Crime reduction. In The Oxford Handbook of Criminology , 2nd ed, ed. M. Maguie. Oxford: Clarendon Press.
Powell, A., and N. Henry. 2018. Policing Technology-Facilitated Sexual Violence Against Adult Victims: Police and Service Sector Perspectives. Policing and Society 28 (3): 291–307.
Rahman, M., B. Carbunar, and U. Topkara. 2013. Fit and Vulnerable: Attacks and Defenses for a Health Monitoring Device. https://doi.org/10.1109/TMC.2015.2418774
Ratajczyk, E., U. Brady, J.A. Baggio, A.J. Barnett, I. Perez-Ibara, N. Rollins, et al. 2016. Challenges and Opportunities in Coding the Commons: Problems, Procedures, and Potential Solutions in Large-N Comparative Case Studies. International Journal of the Commons , 10 (2), 440–466.
Reichherzer, T., M. Timm, N. Earley, N. Reyes, and V. Kumar. 2017. Using Machine Learning Techniques to Track Individuals & Their Fitness Activities. In Proceedings of the 32nd International Conference on Computers and Their Applications, CATA 2017 , 119–124.
Sasse, A. 2015. Scaring and Bullying People into Security Won’t Work. IEEE Security and Privacy 13 (3): 80–83.
Schneier, B. 2018. Click Here to Kill Everybody: Security and Survival in a Hyper-Connected World . New York: WW Norton & Company.
Seto, M. 2015. Internet - Facilitated Sexual Offending . https://www.smart.gov/SOMAPI/printerFriendlyPDF/adult-sec4.pdf .
Sivaraman, V., D. Chan, D. Earl, and R. Boreli. 2016. Smart-Phones Attacking Smart-Homes. In Proceedings of the 9th ACM Conference on Security & Privacy in Wireless and Mobile Networks — WiSec’16 , 195–200.
Sivaraman, V., H.H. Gharakheili, A. Vishwanath, R. Boreli, and O. Mehani. 2015. Network-Level Security and Privacy Control for Smart-Home IoT Devices. In 2015 IEEE 11th International Conference on Wireless and Mobile Computing, Networking and Communications, WiMob 2015 , 163–167.
Smartgrid.gov. 2018. What is the Smart Grid? https://www.smartgrid.gov/the_smart_grid/smart_grid.html .
Snader, R., Kravets, R., and Harris III, A.F. 2016. CryptoCop: Lightweight, Energy-Efficient Encryption and Privacy for Wearable Devices. In 2nd ACM Workshop on Wearable Systems and Applications. WearSys 2016 , 7–12.
Srinivasan, V., J. Stankovic, and K. Whitehouse. 2008. A Fingerprint and Timing-Based Snooping Attack on Residential Sensor Systems. ACM SIGBED Review 5 (1): 1–2.
Statistica. 2018. Estimated Global Commercial Drone Unit Sales in 2016 and 2017 (in 1,000 Units). https://www.statista.com/statistics/740428/global-commercial-drone-unit-sales/ .
Tekeoglu, A., and A.S. Tosun. 2015a. A Closer Look into Privacy and Security of Chromecast Multimedia Cloud Communications. In 2015 IEEE Conference on Computer Communications Workshops ( INFOCOM WKSHPS ), 121–126
Tekeoglu, A., and A.S. Tosun. 2015b. Investigating Security and Privacy of a Cloud-Based Wireless IP Camera: NetCam. In Proceedings — International Conference on Computer Communications and Networks, ICCCN , 2015 – October .
Thing, V.L.L. 2017. IEEE 802.11 Network Anomaly Detection and Attack Classification: A Deep Learning Approach. In Wireless Communications and Networking Conference (WCNC) .
Torre, I., F. Koceva, O.R. Sanchez, and G. Adorni. 2017. Fitness Trackers and Wearable Devices: How to Prevent Inference Risks? In Proceedings of the 11th International Conference on Body Area Networks . EAI.
Tzezana, R. 2016. Scenarios for Crime and Terrorist Attacks Using the Internet of Things. European Journal of Futures Research 4 (1): 18.
Tzezana, R. 2017. High-Probability and Wild-Card Scenarios for Future Crimes and Terror Attacks Using the Internet of Things. Foresight 19 (1): 1–14.
Vemi, S.G., and C. Panchev. 2015. Vulnerability Testing of Wireless Access Points Using Unmanned Aerial Vehicles (UAV). In Proceedings of the European Conference on e - Learning , 245.
Vigo, R., E. Yuksel, and Dewi Puspa Kencana Ramli, C. 2012. Smart Grid Security a Smart Meter-Centric Perspective. In 2012 20th Telecommunications Forum (TELFOR) , 127–130
Visan, B.A., J. Lee, B. Yang, A.H. Smith, and E.T. Matson. 2017. Vulnerabilities in Hub Architecture IoT Devices. In 2017 14th IEEE Annual Consumer Communications and Networking Conference , CCNC 2017 , 83–88
Wang, C., X. Guo, Y. Wang, Y. Chen, and B. Liu. 2016. Friend or Foe? In Proceedings of the 11th ACM on Asia Conference on Computer and Communications Security — ASIA CCS’16 , 189–200.
Wang, H., T.T.-T. Lai, and R. Roy Choudhury. 2015. MoLe: Motion Leaks Through Smartwatch Sensors. In Proceedings of the 21st Annual International Conference on Mobile Computing and Networking — MobiCom’15 , 155–166.
Wazid, M., A.K. Das, V. Odelu, N. Kumar, and W. Susilo. 2017. Secure Remote User Authenticated Key Establishment Protocol for Smart Home Environment. In IEEE Transactions on Dependable and Secure Computing , 5971 (c).
Weisburd, D., D.P. Farrington, and C. Gill (eds.). 2016. What Works in Crime Prevention and Rehabilitation: Lessons from Systematic Reviews . New York: Springer.
Which? 2017. Safety Alert: See How Easy it is for Almost Anyone to Hack Your Child’s Connected Toys. https://www.which.co.uk/news/2017/11/safety-alert-see-how-easy-it-is-for-almost-anyone-to-hack-your-childs-connected-toys/ .
Williams, R., E. McMahon, S. Samtani, M. Patton, and H. Chen. 2017. Identifying Vulnerabilities of Consumer Internet of Things (IoT) Devices: A Scalable Approach. In 2017 IEEE International Conference on Intelligence and Security Informatics: Security and Big Data, ISI 2017 , 179–181.
Wrap. 2017. Smart Devices & Secure Data Eradication: The Evidence . http://www.wrap.org.uk/sites/files/wrap/DataEradicationreportDefra.pdf .
Wurm, J., K. Hoang, O. Arias, A.-R. Sadeghi, and Y. Jin. 2016. Security Analysis on Consumer and Industrial IoT Devices. In 2016 21st Asia and South Pacific Design Automation Conference (ASP - DAC) , 519–524.
Xu, H., D. Sgandurra, K. Mayes, P. Li, and R. Wang. 2017. Analysing the Resilience of the Internet of Things Against Physical and Proximity Attacks , Vol. 10658.
Yoshigoe, K., W. Dai, M. Abramson, and A. Jacobs. 2016. Overcoming Invasion of Privacy in Smart Home Environment with Synthetic Packet Injection. In Proceedings of 2015 TRON Symposium, TRONSHOW 2015 , 1 (C).
Download references
Acknowledgements
This work was funded by the UK EPSRC as part of the PETRAS IoT Research Hub—Cybersecurity of the Internet of Things grant no. EP/N02334X/1 and the Dawes Centre for Future Crime at University College London.
Author information
Authors and affiliations.
Department of Security and Crime Science, Dawes Centre for Future Crime at UCL, UCL Jill Dando Institute of Security and Crime Science, University College London, 35 Tavistock Square, London, WC1H 9EZ, UK
John M. Blythe & Shane D. Johnson
You can also search for this author in PubMed Google Scholar
Corresponding author
Correspondence to Shane D. Johnson .
Additional information
Publisher's note.
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Electronic supplementary material
Below is the link to the electronic supplementary material.
Supplementary material 1 (DOCX 33 kb)
Rights and permissions.
Reprints and permissions
About this article
Blythe, J.M., Johnson, S.D. A systematic review of crime facilitated by the consumer Internet of Things. Secur J 34 , 97–125 (2021). https://doi.org/10.1057/s41284-019-00211-8
Download citation
Published : 15 October 2019
Issue Date : March 2021
DOI : https://doi.org/10.1057/s41284-019-00211-8
Share this article
Anyone you share the following link with will be able to read this content:
Sorry, a shareable link is not currently available for this article.
Provided by the Springer Nature SharedIt content-sharing initiative
- Internet of Things
- Systematic review
- Crime harvest
- Find a journal
- Publish with us
- Track your research

CRJU U361 - Criminal Justice Research Methods: Literature Review
- Brainstorming
- Literature Review
- Reference Sources
- Criminal Justice Journals
- Articles & Databases
- Internet Searching
- APA 7th Style Examples
- More about APA 7th Ed.
What is a Literature Review?
A Literature Review is a systematic and comprehensive analysis of books, scholarly articles, and other sources relevant to a specific topic providing a base of knowledge on a topic. Literature reviews are designed to identify and critique the existing literature on a topic to justify your research by exposing gaps in current research. This investigation should provide a description, summary, and critical evaluation of works related to the research problem and should also add to the overall knowledge of the topic as well as demonstrating how your research will fit within a larger field of study. A literature review should offer a critical analysis of the current research on a topic and that analysis should direct your research objective. This should not be confused with a book review or an annotated bibliography both research tools but very different in purpose and scope. A Literature Review can be a stand-alone element or part of a larger end product, know your assignment. The key to a good Literature Review is to document your process.
Literature Review LibGuide

To see the Full Literature Review Guide click here
There is SO much more information on the full LibGuide for Literature Reviews Please make sure to click over to that LibGuide for more examples, explanations, and hints.
Elements in a Literature Review
- Elements in a Literature Review txt of infographic
Critical Evaluation
Process of a literature review.
The process of writing a literature review is not necessarily a linear process, you will often have to loop back and refine your topic, try new searches and altar your plans. The info graphic above illustrates this process. It also reminds you to continually keep track of your research by citing sources and creating a bibliography.
- Know what the review is for; each assignment will offer the purpose for the review. For example, is it for “background”, or a “pro and con discussion”, "integration", “summarizing”, etc.
- Create a “search plan”, decide where you will search for information, what type of information you will need.
- Research - Preform Searches; choose sources and collect information to use in your paper. Make sure you cite the sources used.
- Think - Analyze information in a systematic manner and begin your literature review (e.g., summarize, synthesize, etc.). Make sure you cite the sources used.
- Complete - Write your paper, proof & revise and create your finished bibliography.
Literature Review Places to Look
Help from other universities.
Help and tips in writing a Review of Literature
- Learn How to Write a Review of Literature - University of Wisconsin-Madison Writing Center Learn How to Write a Review of Literature - From the University of Wisconsin-Madison Writing Center.
- Literature Reviews - UNC Chapel Hill Writing Center
- The Literature Review: A Few Tips on Conducting It
- Writing a Literature Review by Temple University
- << Previous: Brainstorming
- Next: Reference Sources >>
- Last Updated: Aug 12, 2024 3:16 PM
- URL: https://uscupstate.libguides.com/CriminalJusticeResearchMethods

PSYC 210: Foundations of Psychology
- Tips for Searching for Articles
What is a literature review?
Conducting a literature review, organizing a literature review, writing a literature review, helpful book.
- Avoiding Plagiarism
- Google Scholar

A literature review is a compilation of the works published in a particular field of study or line of research, usually over a specific period of time, in the form of an in-depth, critical bibliographic essay or annotated list in which attention is drawn to the most significant works.
- Summarizes and analyzes previous research relevant to a topic
- Includes scholarly books and articles published in academic journals
- Can be an specific scholarly paper or a section in a research paper
The objective of a Literature Review is to find previous published scholarly works relevant to an specific topic
- Help gather ideas or information
- Keep up to date in current trends and findings
- Help develop new questions
A literature review is important because it:
- Explains the background of research on a topic
- Demonstrates why a topic is significant to a subject area
- Helps focus your own research questions or problems
- Discovers relationships between research studies/ideas
- Suggests unexplored ideas or populations
- Identifies major themes, concepts, and researchers on a topic
- Tests assumptions; may help counter preconceived ideas and remove unconscious bias
- Identifies critical gaps, points of disagreement, or potentially flawed methodology or theoretical approaches
Source: "What is a Literature Review?", Old Dominion University, https://guides.lib.odu.edu/c.php?g=966167&p=6980532
1. Choose a topic. Define your research question.
Your literature review should be guided by a central research question. It represents background and research developments related to a specific research question, interpreted, and analyzed by you in a synthesized way.
- Make sure your research question is not too broad or too narrow.
- Write down terms that are related to your question for they will be useful for searches later.
2. Decide on the scope of your review.
How many studies do you need to look at? How comprehensive should it be? How many years should it cover?
- This may depend on your assignment.
- Consider these things when planning your time for research.
3. Select the databases you will use to conduct your searches.
- By Research Guide
4. Conduct your searches and find the literature.
- Review the abstracts carefully - this will save you time!
- Many databases will have a search history tab for you to return to for later.
- Use bibliographies and references of research studies to locate others.
- Use citation management software such as Zotero to keep track of your research citations.
5. Review the literature.
Some questions to help you analyze the research:
- What was the research question you are reviewing? What are the authors trying to discover?
- Was the research funded by a source that could influence the findings?
- What were the research methodologies? Analyze the literature review, samples and variables used, results, and conclusions. Does the research seem complete? Could it have been conducted more soundly? What further questions does it raise?
- If there are conflicted studies, why do you think that is?
- How are the authors viewed in the field? Are they experts or novices? Has the study been cited?
Source: "Literature Review", University of West Florida, https://libguides.uwf.edu/c.php?g=215113&p=5139469
A literature review is not a summary of the sources but a synthesis of the sources. It is made up of the topics the sources are discussing. Each section of the review is focused on a topic, and the relevant sources are discussed within the context of that topic.
1. Select the most relevant material from the sources
- Could be material that answers the question directly
- Extract as a direct quote or paraphrase
2. Arrange that material so you can focus on it apart from the source text itself
- You are now working with fewer words/passages
- Material is all in one place
3. Group similar points, themes, or topics together and label them
- The labels describe the points, themes, or topics that are the backbone of your paper’s structure
4. Order those points, themes, or topics as you will discuss them in the paper, and turn the labels into actual assertions
- A sentence that makes a point that is directly related to your research question or thesis
This is now the outline for your literature review.
Source: "Organizing a Review of the Literature – The Basics", George Mason University Writing Center, https://writingcenter.gmu.edu/writing-resources/research-based-writing/organizing-literature-reviews-the-basics
- Literature Review Matrix Here is a template on how people tend to organize their thoughts. The matrix template is a good way to write out the key parts of each article and take notes. Downloads as an XLSX file.
The most common way that literature reviews are organized is by theme or author. Find a general pattern of structure for the review. When organizing the review, consider the following:
- the methodology
- the quality of the findings or conclusions
- major strengths and weaknesses
- any other important information
Writing Tips:
- Be selective - Select only the most important points in each source to highlight in the review. It should directly relate to the review's focus.
- Use quotes sparingly.
- Keep your own voice - Your voice (the writer's) should remain front and center. .
- Aim for one key figure/table per section to illustrate complex content, summarize a large body of relevant data, or describe the order of a process
- Legend below image/figure and above table and always refer to them in text
Source: "Composing your Literature Review", Florida A&M University, https://library.famu.edu/c.php?g=577356&p=3982811
- << Previous: Tips for Searching for Articles
- Next: Citing Your Sources >>
- Last Updated: Aug 21, 2024 3:43 PM
- URL: https://infoguides.pepperdine.edu/PSYC210
Explore. Discover. Create.
Copyright © 2022 Pepperdine University
- Skip to main content
- Skip to primary sidebar
- Request Info
- Search Search Site Faculty/Staff
- Open Navigation Menu Menu Close Navigation Menu
- Literature Review Guidelines
Making sense of what has been written on your topic.
Goals of a literature review:.
Before doing work in primary sources, historians must know what has been written on their topic. They must be familiar with theories and arguments–as well as facts–that appear in secondary sources.
Before you proceed with your research project, you too must be familiar with the literature: you do not want to waste time on theories that others have disproved and you want to take full advantage of what others have argued. You want to be able to discuss and analyze your topic.
Your literature review will demonstrate your familiarity with your topic’s secondary literature.
GUIDELINES FOR A LITERATURE REVIEW:
1) LENGTH: 8-10 pages of text for Senior Theses (485) (consult with your professor for other classes), with either footnotes or endnotes and with a works-consulted bibliography. [See also the citation guide on this site.]
2) NUMBER OF WORKS REVIEWED: Depends on the assignment, but for Senior Theses (485), at least ten is typical.
3) CHOOSING WORKS:
Your literature review must include enough works to provide evidence of both the breadth and the depth of the research on your topic or, at least, one important angle of it. The number of works necessary to do this will depend on your topic. For most topics, AT LEAST TEN works (mostly books but also significant scholarly articles) are necessary, although you will not necessarily give all of them equal treatment in your paper (e.g., some might appear in notes rather than the essay). 4) ORGANIZING/ARRANGING THE LITERATURE:
As you uncover the literature (i.e., secondary writing) on your topic, you should determine how the various pieces relate to each other. Your ability to do so will demonstrate your understanding of the evolution of literature.
You might determine that the literature makes sense when divided by time period, by methodology, by sources, by discipline, by thematic focus, by race, ethnicity, and/or gender of author, or by political ideology. This list is not exhaustive. You might also decide to subdivide categories based on other criteria. There is no “rule” on divisions—historians wrote the literature without consulting each other and without regard to the goal of fitting into a neat, obvious organization useful to students.
The key step is to FIGURE OUT the most logical, clarifying angle. Do not arbitrarily choose a categorization; use the one that the literature seems to fall into. How do you do that? For every source, you should note its thesis, date, author background, methodology, and sources. Does a pattern appear when you consider such information from each of your sources? If so, you have a possible thesis about the literature. If not, you might still have a thesis.
Consider: Are there missing elements in the literature? For example, no works published during a particular (usually fairly lengthy) time period? Or do studies appear after long neglect of a topic? Do interpretations change at some point? Does the major methodology being used change? Do interpretations vary based on sources used?
Follow these links for more help on analyzing historiography and historical perspective .
5) CONTENTS OF LITERATURE REVIEW:
The literature review is a research paper with three ingredients:
a) A brief discussion of the issue (the person, event, idea). [While this section should be brief, it needs to set up the thesis and literature that follow.] b) Your thesis about the literature c) A clear argument, using the works on topic as evidence, i.e., you discuss the sources in relation to your thesis, not as a separate topic.
These ingredients must be presented in an essay with an introduction, body, and conclusion.
6) ARGUING YOUR THESIS:
The thesis of a literature review should not only describe how the literature has evolved, but also provide a clear evaluation of that literature. You should assess the literature in terms of the quality of either individual works or categories of works. For instance, you might argue that a certain approach (e.g. social history, cultural history, or another) is better because it deals with a more complex view of the issue or because they use a wider array of source materials more effectively. You should also ensure that you integrate that evaluation throughout your argument. Doing so might include negative assessments of some works in order to reinforce your argument regarding the positive qualities of other works and approaches to the topic.
Within each group, you should provide essential information about each work: the author’s thesis, the work’s title and date, the author’s supporting arguments and major evidence.
In most cases, arranging the sources chronologically by publication date within each section makes the most sense because earlier works influenced later ones in one way or another. Reference to publication date also indicates that you are aware of this significant historiographical element.
As you discuss each work, DO NOT FORGET WHY YOU ARE DISCUSSING IT. YOU ARE PRESENTING AND SUPPORTING A THESIS ABOUT THE LITERATURE.
When discussing a particular work for the first time, you should refer to it by the author’s full name, the work’s title, and year of publication (either in parentheses after the title or worked into the sentence).
For example, “The field of slavery studies has recently been transformed by Ben Johnson’s The New Slave (2001)” and “Joe Doe argues in his 1997 study, Slavery in America, that . . . .”
Your paper should always note secondary sources’ relationship to each other, particularly in terms of your thesis about the literature (e.g., “Unlike Smith’s work, Mary Brown’s analysis reaches the conclusion that . . . .” and “Because of Anderson’s reliance on the president’s personal papers, his interpretation differs from Barry’s”). The various pieces of the literature are “related” to each other, so you need to indicate to the reader some of that relationship. (It helps the reader follow your thesis, and it convinces the reader that you know what you are talking about.)
7) DOCUMENTATION:
Each source you discuss in your paper must be documented using footnotes/endnotes and a bibliography. Providing author and title and date in the paper is not sufficient. Use correct Turabian/Chicago Manual of Style form. [See Bibliography and Footnotes/Endnotes pages.]
In addition, further supporting, but less significant, sources should be included in content foot or endnotes . (e.g., “For a similar argument to Ben Johnson’s, see John Terry, The Slave Who Was New (New York: W. W. Norton, 1985), 3-45.”)
8 ) CONCLUSION OF LITERATURE REVIEW:
Your conclusion should not only reiterate your argument (thesis), but also discuss questions that remain unanswered by the literature. What has the literature accomplished? What has not been studied? What debates need to be settled?
Additional writing guidelines
History and American Studies
- About the Department
- Major Requirements & Courses
- What courses will I take as an History major?
- What can I do with my History degree?
- History 485
- Methodology
- Choosing a Topic
- Book Reviews
- Historiographic Clues
- Understanding Historical Perspective
- Sample Literature Review
- Using Quotations
- Ellipses and Brackets
- Footnotes and Endnotes
- Content Notes
- Citation Guide
- Citing Non-Print Resources
- How to Annotate
- Annotated Examples
- Journals vs. Magazines
- Understanding Plagiarism
- Historians Define Plagiarism
- Plagiarism Tutorial
- UMW Honor System
- Presentation Guidelines
- Tips for Leading Seminars
- Hints for Class Discussion
- Speaking Center
- Guidelines for a Research Paper
- Library Research Plan
- How to Use ILL
- Database Guide
- Guide to Online Research
- Writing Guidelines
- Recognizing Passive Voice
- Introduction and Conclusion
- MS Word’s Grammar and Spellcheck
- Writing Center
- What You Need to Know
- Links to Online Primary Sources by Region
- What will I learn from my American Studies major?
- What courses will I take as an American Studies major?
- What can I do with my American Studies degree?
- American Studies 485
- For Prospective Students
- Honors and Award Recipients
- Internships
Alumni Intros

How have History & American Studies majors built careers after earning their degrees? Learn more by clicking the image above.
Recent Posts
- History and American Studies Symposium–April 26, 2024
- Fall 2024 Courses
- Fall 2023 Symposium – 12/8 – All Welcome!
- Spring ’24 Course Flyers
- Internship Opportunity – Chesapeake Gateways Ambassador
- Congratulations to our Graduates!
- History and American Studies Symposium–April 21, 2023
- View umwhistory’s profile on Facebook
- View umwhistory’s profile on Twitter

An official website of the United States government, Department of Justice.
Here's how you know
Official websites use .gov A .gov website belongs to an official government organization in the United States.
Secure .gov websites use HTTPS A lock ( Lock A locked padlock ) or https:// means you’ve safely connected to the .gov website. Share sensitive information only on official, secure websites.
NCJRS Virtual Library
Trafficking in human beings and organized crime: a literature review, additional details.
Ottawa, Ontario K1A 0R2 Canada , Canada
Availability
Related topics.

Crime & Mystery
4 New Crime Novels Thrumming With Menace
Our mystery columnist reviews books by Scott Phillips, Morgan Richter, Snowden Wright and Jamie Harrison.
Credit... Pablo Amargo
Supported by
- Share full article
By Sarah Weinman
- Aug. 28, 2024
If you’re going to write about seedy underbellies and strange subcultures, then follow the road map created by Scott Phillips: Make it funny, make it ribald, make it memorable. That’s what Phillips has been doing ever since his lauded 2000 debut, “The Ice Harvest.”
THE DEVIL RAISES HIS OWN (Soho Crime, 368 pp., $27.95) is his latest novel to feature the photographer Bill Ogden, who was first seen in “Cottonwood,” set on the Kansas frontier in 1872.

Now, more than four decades removed from his “Cottonwood” shenanigans, he’s living in Los Angeles, still able to work (and score), albeit more slowly. His granddaughter, Flavia, fresh off killing her husband back in Kansas (“I recently collapsed Albert’s cranial vault,” she says), has taken on partner/successor duties at his photography studio. Both are pulled into the orbit of the “blue movie” industry — milder in 1916, to be sure, but still prone to violence — where they encounter a vivid, pungent cast of scoundrels and flimflam artists, from a film star named Magnolia Sweetspire to a mousy postal inspector named Melvin de Kamp.
Phillips always adopts a wonderfully deadpan air, but beneath his black humor is a steely emotional core. “The Devil Raises His Own” is a romp, but it’s also a poignant exploration of chosen families, broken homes and desperate dreams.
We are having trouble retrieving the article content.
Please enable JavaScript in your browser settings.
Thank you for your patience while we verify access. If you are in Reader mode please exit and log into your Times account, or subscribe for all of The Times.
Thank you for your patience while we verify access.
Already a subscriber? Log in .
Want all of The Times? Subscribe .
Advertisement
We earn a commission for products purchased through some links in this article.
Best cosy crime to read
Our round-up of the best comforting mystery novels to read right now.
If you fancy yourself as an amateur detective, these are the books for you. Cosy crime takes much from the Golden Age of crime and authors such as Agatha Christie and Dorothy L Sayers: although there is often a (sometimes quite violent) murder, this isn't lingered on and the focus is very much on the investigation, often led by an amateur with a talent for sleuthing.
They are often set in a quintessentially English setting, such as the (imagined) chocolate box village of St Mary's Mead where Miss Marple kept a beady eye out for trouble, or the luxury Coopers Chase retirement home of Richard Osman's Thursday Murder Club series.
Denouements are often neatly resolved, with the murderer caught and punished, leaving the reader feeling like all is well in the world. If that all sounds appealing right now, read on...
D Is For Death by Harriet F Townson
The first inabrilliant newseries of historical mysteriesfrom the author better knownas Harriet Evans. Set in the1930s, it follows Dora as sheflees her impending nuptials– then gets caught up in amurder case after findinga body in The London Library.
D is for Death by Harriet F Townson

Miss Austen Investigates by Jessica Bull
When I first heard about this book, which casts Jane Austen as an amateur detective, I thought it sounded a bit gimmicky – but it is so clever and well done. When Jane’s younger brother, Georgy, who is disabled, is falsely accused of a murder, she must clear his name and find the real killer.

Knife Skills For Beginners by Orlando Murrin
A cookery school is the setting for this murder mystery billed as MasterChef meets The Thursday Murder Club – a pretty appealing pairing! When a dead body is found in the kitchen, chef Paul Delamere is the main suspect and, in order to clear his name, he must find the real killer from among his culinary students.
Knife Skills for Beginners by Orlando Murrin

The Housekeepers by Alex Hay
This Edwardian heist story is such a fun read! After housekeeper Mrs King is dismissed from her position in a grand Park Lane house after years of service, she gets a group of women together to burgle the home of her former employer on the night of the annual costume ball.

The Fellowship Of The Puzzlemakers by Samuel Burr
A gorgeously quirky read about Pippa, a crossword compiler, who establishes a place for fellow puzzlemakers to gather. It’s also the story of Clayton, who was found abandoned as a baby on the doorstep of the fellowship’s HQ, and his quest to solve the biggest puzzle of all: who he really is.
The Fellowship of Puzzlemakers by Samuel Burr

We Solve Murders by Richard Osman
Osman has done it again with this, the first of what will be a new series of mysteries. Our detectives are father- and daughter-in-law Steve and Amy, who become embroiled in murder after a dead body turns up on the tropical island where Amy is working.

The Christmas appeal by Janice Hallett
Fans of Hallett’s fiendish mysteries will love this festive offering that reunites readers with the Fairways Players am dram group who appeared in The Appeal . Plans are in progress for a special performance of Jack And The Beanstalk but not before murder, mayhem and a dead Santa.
Viper The Christmas Appeal by Janice Hallett

A Death In The Parish by Reverend Richard Coles
Daniel Clement is back for the second in the brilliant Canon Clement Mystery series and he's working again with detective sergeant Neil Vandaloo after a local teenage boy is killed in what appears to be a ritualistic murder. Again, there are brilliant characters (especially Daniel's Mother Audrey who is up to no good) and a potent mix of poignancy and humour.
W&N A Death in the Parish by Reverend Richard Coles

The Shell House Detectives by Emylia Hall
This cosy crime novel from the author of The Book Of Summers is set in a small Cornish town. Recently widowed Ally is walking her dog on the beach when she discovers a young man who’s fallen from the cliffs above – or was he pushed? When the police seem to be getting nowhere, Ally teams up with former policeman Jayden to investigate.

The Three Dahlias by Katy Watson
Fans of Golden Age crime novels will love this delightful country house mystery about three rival actors who team up to solve a murder. Fans and VIPs have gathered together at the home of legendary crime writer Lettice Davenport for a weekend of fun and games, but things take a sinister turn when a real murder happens during a re-enactment.

Over My Dead Body by Maz Evans
The hero of this hilarious murder mystery is feisty surgeon Dr Miriam Price, who turns detective in the afterlife to try to work out who killed her. The only person who can see her – and therefore help her – is her neighbour Winnie, who she has been in a feud with for years. A really entertaining read that will appeal to fans of Richard Osman.

The Magpie Murders by Anthony Horowitz
If your idea of a good read is a Miss Marple or a Poirot, you'll love this. When a literary editor gets the latest manuscript from her best-selling crime writer she's delighted - she knows fans love his detective, Atticus Pünd, a celebrated solver of crimes in the sleepy English villages of the 1950s. But all is not as it seems and within the pages of the book are clues about a real-life murder. This clever mystery-within-a-mystery hooks you in from the first page and is complex enough to hold you to the last.
Orion Magpie Murders by Anthony Horowitz

Murder Under The Tuscan Sun by Rachel Rhys
An isolated castle in 1920s Italy is the setting for this engrossing historical mystery, which has shades of Agatha Christie about it. Recently widowed Connie starts a new life in Tuscany caring for an invalid – but strange goings-on soon make her begin to question her own sanity.
Murder Under the Tuscan Sun by Rachel Rhys

The Monogram Murders by Sophie Hannah
Nearly 40 years ago Agatha Christie killed off Hercule Poirot - but now he is back. For the first time Christie's estate have given permission for the legendary Belgian detective to be - literally - brought back to life by another writer. It could easily have backfired but Sophie Hannah has done a terrific job. In The Monogram Murders , three bodies are found dead on the same day in a luxurious London hotel with a monogrammed cufflink in each of their mouths. Guaranteed to give ‘ze little grey cells’ a workout!
HarperCollins Publishers The Monogram Murders by Sophie Hannah

Agatha Raisin And The Quiche Of Death by MC Beaton
MC Beaton was one of the many pen names of the prolific Scottish author Marion Chesney, who died in 2019 having written 31 books about Agatha Raisin and 34 about Hamish Macbeth. Agatha is a brilliant character - difficult, fiery, rebellious, but also vulnerable. This first book in the series sees Agatha moving to a new town in the Cotswolds and in an effort to fit in she enters a (bought) quiche is a local baking competition - only for the judge to die after eating it. Agatha then turns detective to clear her name.
Agatha Raisin and the Quiche of Death by MC Beaton

The Last Devil To Die by Richard Osman
No cosy crime round up is complete without a mention of the Thursday Murder Club series, credited with the recent interest in gentle murder mysteries. This is the fourth book in the series and sees the septugenarians facing their most dangerous case yet.

11 must-read novels about marriage

Join our Book Club Live with Lucy Foley

Join our new book club

Kate Atkinson's writing tips
10 best books to read now
Best books of 2024 (so far)
Books for kids: conversation starters
Best feel-good books

10 best short books
16 best romance novels

A summer short story from Philippa Gregory
16 best fantasy books

IMAGES
VIDEO
COMMENTS
A literature review can be a short introductory section of a research article or a report or policy paper that focuses on recent research. Or, in the case of dissertations, theses, and review articles, it can be an extensive review of all relevant research. The format is usually a bibliographic essay; sources are briefly cited within the body ...
Consequently, the application of artificial intelligence (AI) in crime prediction is a significant and well-researched area. This study investigates AI strategies in crime prediction. We conduct a systematic literature review (SLR). Our review evaluates the models from numerous points of view, including the crime analysis type, crimes studied ...
In the same year, Worrall also summarised this macro-level police levels-crime literature, concluding that '…a police presence matters' (2010: 48). Like Lim et al. (2010) and Worrall (2010), we present a systematic review of the police-levels crime literature. We go a step further, however, and invoke formal meta-analytic techniques to ...
The papers identified as review or related-work studies (a total of 13) date back to 2003 and are connected to the keyword strategy that we used (find further details in "Study selection" section). In addition, to review papers (a total of 9), we also include two editorials, one book chapter, and one research paper, because they contain an extensive literature review in the field of crime ...
A literature review is an overview of literature published on a topic, issue, or theory. It can cover a wide variety of materials including but not limited to scholarly articles, books, dissertations, reports, conference proceedings, etc. The purpose of a literature review is to describe, summarize, and evaluate the works being examined for the ...
A literature review is a comprehensive summary and analysis of previously published research on a particular topic. Literature reviews should give the reader an overview of the important theories and themes that have previously been discussed on the topic, as well as any important researchers who have contributed to the discourse.
2. Method. We answered our research questions with a scoping literature review, which is described as 'a form of knowledge synthesis that addresses an exploratory research question aimed at mapping key concepts, types of evidence, and gaps in research related to a defined area or field by systematically searching, selecting, and synthesizing existing knowledge' (Colquhoun et al., Citation ...
Why do inequality and deprivation produce high crime and ...
The current literature review presented in this article confirms this with 36 of the 69 (52%) reviewed articles using NNs to predict crime hotspots and shown in Table 1. Neural network predictions from the literature may be for a specific type of crime or the frequency of occurrence of a specific type of crime, or the general location for a ...
Lorenc T, Petticrew M, Whitehead M, et al. Crime, fear of crime and mental health: synthesis of theory and systematic reviews of interventions and qualitative evidence. Southampton (UK): NIHR Journals Library; 2014 Mar. (Public Health Research, No. 2.2.) ... Figure 3 shows the flow of literature through the review. A total of 12,093 references ...
The weather-crime association has intrigued scholars for more than 150 years. While there is a long-standing history of scholarly interest in the weather-crime association, the last decade has evidenced a marked increase in the volume and diversity of empirical studies concerned with weather and its social implications including crime. In this paper we conduct a review of the empirical ...
This is the first systematic literature review with this perspective over cyber threat intelligence to the best of our knowledge. The rest of this paper is organized as follows. First, Section 2 outlines the background as well as related work. Further on, Section 3 elaborates on the research design behind this study.
Articles are lengthy literature reviews with BIG bibliographies. Useful for both the text summary and the citations for further reading. Includes Annual Review of Criminology, Annual Review of Law and Social Science and Annual Review of Sociology. HINT! Use the "Advanced Search" link in the upper right corner of the startup window.
The current study analyzes a sample of academic articles examining "fear of crime" and that were published in peer-reviewed journals during the past 25 years (n = 547).Using a systematic quantitative literature review method, results show that the fear of crime scholarship—and citations to it—increased significantly during this time, although most studies were undertaken in a handful ...
This literature review examines the available empirical evidence on a variety of police-led violence reduction strategies (offender-focused, place-based, and community- ... and social disorder to prevent more serious crime. A review of the evaluation literature suggests that broken windows policing strategies, particularly those that ...
Criminology and literature is an interdisciplinary field con-necting the social scientific study of crime, criminals, criminal law, and criminal justice with humankind's artistic, imaginative expression in written word. The thesis of the field is that crimes are texts—broadly defined as things made by humans—with
To answer the second question, each author of the present meta-review independently rated review conclusions, to determine whether reviews deemed the evidence for the predictive utility of criminogenic risk assessment to be strong, moderate, or weak. Our inter-rater reliability, estimated with Cohen's kappa, was 0.84, p < 0.01. Ratings ...
The nature of crime is changing—estimates suggest that at least half of all crime is now committed online. Once everyday objects (e.g. televisions, baby monitors, door locks) that are now internet connected, collectively referred to as the Internet of Things (IoT), have the potential to transform society, but this increase in connectivity may generate new crime opportunities. Here, we ...
A Literature Review is a systematic and comprehensive analysis of books, scholarly articles, and other sources relevant to a specific topic providing a base of knowledge on a topic. Literature reviews are designed to identify and critique the existing literature on a topic to justify your research by exposing gaps in current research. This investigation should provide a description, summary ...
Conclusion. We have reviewed literature concerning prevention of violent crime and have identified the definitions and prevalence of violent crime, characteristics of both victims and offenders, modus operandi, and suggestions for effective strategies against it, as well as implications for policy and officer training.
(d) Personal history documentation and literature review used for distribution and studied by the gang members. Ianni and Reuss-Ianni : Analyze the social organization and the internal relationship of an Italian American OC family: US: Mafia: The Lupollo family, fictive name for an OC family based in New York from its origin to the 1960s.
on a systematic review of more than 500 scientific evaluations of crime prevention practices. This Research in Brief summa-rizes the research methods and conclu-sions found in that report. In 1996, a Federal law required the U.S. Attorney General to provide Con-gress with an independent review of the Many crime prevention programs work. Others ...
A literature review is a compilation of the works published in a particular field of study or line of research, usually over a specific period of time, in the form of an in-depth, critical bibliographic essay or annotated list in which attention is drawn to the most significant works.. Summarizes and analyzes previous research relevant to a topic ...
Your literature review must include enough works to provide evidence of both the breadth and the depth of the research on your topic or, at least, one important angle of it. The number of works necessary to do this will depend on your topic. For most topics, AT LEAST TEN works (mostly books but also significant scholarly articles) are necessary ...
The authors' review of varying definitions of "trafficking in human beings" favors the definitions offered by Wijers and Lap-Chew (1997) and that of the United Nations Convention Against Transnational Organized Crime (2000). These definitions emphasize the use of coercion and force to compel individuals to be transported within and across ...
THE DEVIL RAISES HIS OWN (Soho Crime, 368 pp., $27.95) is his latest novel to feature the photographer Bill Ogden, who was first seen in "Cottonwood," set on the Kansas frontier in 1872. Image
When a literary editor gets the latest manuscript from her best-selling crime writer she's delighted - she knows fans love his detective, Atticus Pünd, a celebrated solver of crimes in the sleepy ...